Social engineering scammers are using cloned social media accounts to carry out deceit

Fraudsters are using Twitter bots to trick unsuspecting tweeters into making PayPal and Venmo payments to accounts under their control.
The bots appear to be activated when a legitimate user asks another for their payment information, presumably discovering these tweets via a search for keywords such as ‘PayPal’, ‘Venmo’, or other services.
They masquerade as the other user by scraping their profile picture and adopting a similar username, before supplying them with false payment information in the hopes the original tweeter will pay into this account.
By way of example, Twitter user ‘Skye’ (@stimmyskye) posted a screenshot online detailing how they were targeted by a bot.
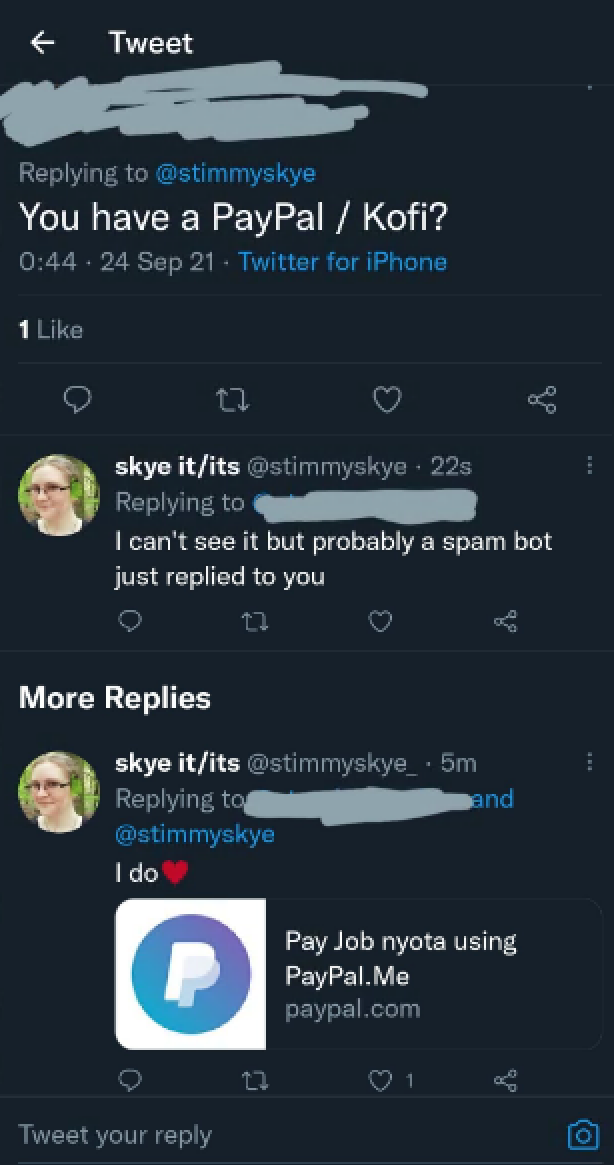
A screenshot of the Twitter bot in action
Skye noted that the bot blocks the account that it is mimicking, and in their case copied the whole profile and added an underscore to the end of the name.
“Because you’re blocked, you’ll see that there’s one reply to that question but the reply tweet won’t show up,” Skye wrote.
“If you see a ghost reply to a comment like that, it’s almost always a scam bot. They delete as fast as they clone your account. You won’t even know it happened.”
Skye also warned: “They will delete the reply tweet, but the account itself will usually not be deleted, just change the username. So the accounts are usually not brand new, they even have followers. You need to check closely.”
Big issue
Venmo and other online payment services have become a popular means for users to pay for things such as charity donations or for goods such as the resale of event tickets.
This latest scam, however, is a stark warning against making or disclosing any sort of transaction on a public forum.
Skye’s tweets have already garnered thousands of retweets and likes. They also claimed that this issue is “months, if not years old”.
Read more of the latest security news about social media networks
The Daily Swig has reached out to Twitter to confirm whether it is aware of these payment-requesting bots and what steps it intends to take to protect users.
In the meantime, Skye has advised: “A failsafe option is to ask for payment info via DM only, or request they be sent to you via DM.
“With DMs, either you’ve got them closed so the scam bot can’t send you any, or you’ve got them open and it’ll show as a DM request rather than just appear in your inbox.”
They added: “It would be extremely easy to detect and prevent this behavior, let’s hope that @TwitterSupport finally does something about it… I would like for this warning to become obsolete.”
Pay close attention
Andy Patel, researcher with F-Secure’s Artificial Intelligence Center of Excellence, told The Daily Swig that he hasn’t seen this kind of bot during his own research, but reiterated Skye’s advice for users.
Patel said: “Given that the mechanism is automated, I’m willing to bet that the attack is fairly successful.
"A Twitter user would need to pay close attention to what is going on in order to notice what’s happened.”
He added: “Don’t publicly link to your PayPal (or similar) account – deal with payments via direct message instead.”
The Daily Swig has reached out to Twitter and will update this article if and when we receive a response.
YOU MAY ALSO LIKE Better future? Safari browser extension is preparing for Apple’s ‘post-privacy’ world






