Ill-equipped businesses set to face off against well-prepared attackers

Organizations are ill-prepared for the rise of 5G, the security risk of which is likely to pervade everything from smart cities to corporate networks for years to come.
A report from Trend Micro, published today (November 15), warns that although the next generation of mobile technology will have the side-effect of new security problems alongside unrivalled speed, scalability and reach.
Trend Micro focused on analysing threats related to private 5G networks – or ‘Campus Local 5G’ – as an exemplar of the wider risks.
Utilities (water and electricity) and industrial plants are likely to be early adopters of private 5G networks, which are likely to become mainstream in the next 18 months or so.
The various threats that organizations face from the rollout of 5G stem in large part from a twist on the well-established SIM-swap, or ‘SIM-jacking’ threat.
SIM-jacking involves fraudsters convincing phone carriers to port a target’s supposedly lost SIM card to one that’s in the hacker’s possession.
The tactic has been used as a component of online bank or cryptocurrency exchange theft – a type of crime that has resulted in multiple prosecutions over the last two years or so.
Once 5G SIM cards become enrolled to the next generation of operational technology equipment, then the potential for mischief will be greatly expanded, Trend Micro says.
And as mobile devices are used for enterprise authentication, hijacked SIM cards can also give hackers access to a user’s enterprise email account as the hardware is regarded as “trusted”.
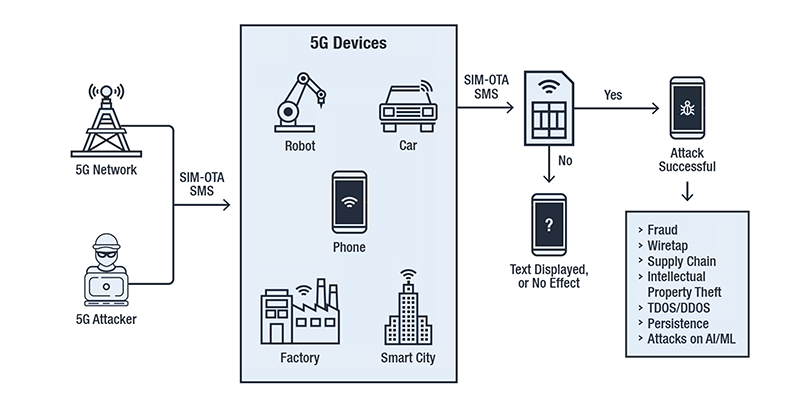 SIM-jacking through abusing the SIM-OTA SMS technology (Image credit: Trend Micro)
SIM-jacking through abusing the SIM-OTA SMS technology (Image credit: Trend Micro)
Turbo-charged malware propagation
The speed and scale of 5G will allow malware to spread further and faster than ever before, which in turn can modify trusted SIM-authorized traffic in the network and cause all sorts of headaches.
Other potential attacks include IoT identity fraud, false decision engine data and logs, and poisoning machine learning rules for the manipulation of business decisions, Trend Micro warns.
“Many industries are poised to tap into the speed, automation, and global reach of 5G, a telecom technology that is new to many of these industries,” the security software firm warns.
“Generally, they will be unprepared, under-skilled, and ill-equipped to handle the sudden simultaneous arrival of many powerful new technologies.
“This will compound the effects of already-mature threat actor groups and complex vulnerabilities in the global telecom carrier ecosystem,” it added.
The weakest link
Bharat Mistry, principal security strategist at Trend Micro, told The Daily Swig that miscreants have already begun discussing mechanisms to abuse 5G networks for profit on underground forums.
“Although 5G offers more security in the transport layer, there’s a weakness in the SIM layer, which ties together the device and the mobile radio,” he explained. “This creates the potential for SIM-Jacking as an entry point to hack into devices and carry out fraud.”
Mistry explained that the threats outlined by Trend Micro are not dependant on who supplies the networking kit and radio masts that provision the network or device manufacturers.
In response to the changing threat landscape that 5G may usher in, Trend Micro advocates a revamped approach to mobile security based on identity federation.
The approach would bring together data network, SIM and device, and roaming integrity under the same roof.
Mistry explained the approach would involve cooperation between multiple entities to offer federated identity through an approach comparable to Single Sign-On technology in conventional enterprise networks.
Trend Micro’s white paper, ‘Securing 5G Through Cyber-Telecom Identity Federation’ (PDF), explains these various threats and their potential remediation in more depth.
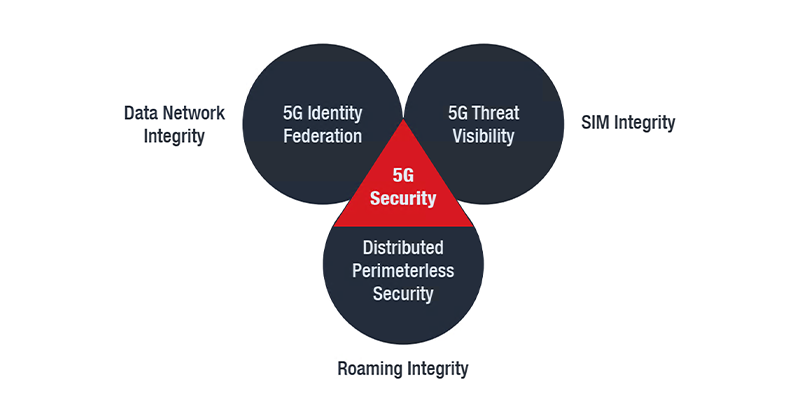 Visualization of an approach to 5G security (Image credit: Trend Micro)
Visualization of an approach to 5G security (Image credit: Trend Micro)
Plus ça change
5G security builds on, and is largely compatible with, key functions and frameworks developed in 4G and earlier technologies. 5G is theoretically more secure than its 4G predecessor, though it’s not without its problems.
For example, security researchers at Purdue University and the University of Iowa recently went public with multiple vulnerabilities in 5G.
The flaws that might potentially be abused to track a victim’s real-time location, spoof emergency alerts, or silently disconnect a 5G-connected phone from the network altogether, among other security and privacy problems.
Some of these new attacks might also be abused to attack existing 4G networks, according to the US academics, who teamed up to develop 5GReasoner, a framework for auditing next generation mobile networks for security and privacy problems.
RELATED Huawei told to shape up if it wants a slice of UK’s 5G rollout






