Researchers aiming to make MITMEngine more accurate and flexible
Cloudflare is working on numerous improvements to MITMEngine, an open source utility that’s designed to detect HTTPS interception, a tell-tale sign of potentially suspicious activity.
At Black Hat USA earlier this month, Cloudflare’s Gabriele Fisher and Luke Valenta offered a deep dive into HTTPS interception practices, in which TLS-terminating middleboxes or middleware can be used to potentially snoop on internet users, or even steal private data.
Monster-in-the-Middle
Launched earlier this year, MITMEngine provides insight into HTTPS interception practices through TLS fingerprinting and tracking discrepancies between the User-Agent headers and ClientHello messages.
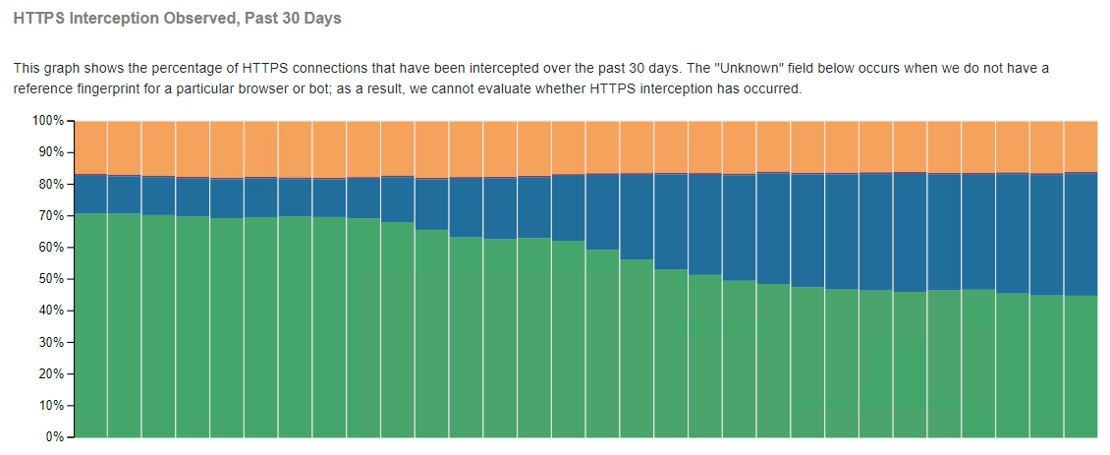
According to metrics from Cloudflare’s HTTPS interception dashboard, MALCOLM, around 16% of internet traffic observed on the organization’s network is suspected as having been intercepted.
“[HTTPS interception occurs] when a TLS connection between a client and a server goes through a third party,” Fisher explained. “This third party in the middle is either hardware, called the ‘middlebox’, or software called ‘middleware’.”
Examples of these so-called ‘monsters-in-the-middle’ include corporate or government proxies and antivirus software.
Although these proxies aim to protect clients by detecting malware or command and control traffic, Fisher said middleware can be used to deliver adware or malware, alongside the in-built capability to censor or spy on clients.
“These proxies can also be used for malicious means,” she noted. “In recent news in Kazakhstan, the government forced Kazakh ISPs to make the clients install root certificates so they could intercept HTTPS traffic.
“Kazakh ISPs encouraged users to install this root certificate by saying it would protect them from fraud, hacking attempts or illegal content – but really this setup allows the Kazakh government to potentially spy on citizens’ everyday online activity.”
Further examples of HTTPS interception being used for malicious means include adware and malware.
Start your MITMEngine
Cloudflare’s MITMEngine can help a server to identify suspicious or potentially vulnerable clients connecting to its network. The server can use this knowledge to notify legitimate users that their connection security might be either degraded or compromised.
Although the project has become another useful tool for helping to improve the security of the web ecosystem, Fisher and Valenta noted that additional developments are needed to further improve accuracy and flexibility, as well as reduce maintenance headaches.
“[TLS] fingerprints in the database quickly go stale as browsers are updated, and it’s time consuming to generate and vet new fingerprints manually,” said Valenta. “We hope to be able to automatically generate fingerprints that we trust from connections observed from Cloudflare’s network
“Making these updates automatic is a big to-do for this project that we plan to [implement] soon.”
He added: “TLS terminating middleboxes pose serious threats to network security, even if they are not inherently malicious. The best case for end-to-end connection security is to avoid HTTPS interception altogether.
“But the reality is that it’s sometimes unavoidable. In these cases, middleboxes performing interception should be held to the same security standards as browsers.”
YOU MIGHT ALSO LIKE HTTP/2 pinged by DDoS vulnerabilities