Time-saving utility was finessed by an IT undergrad during the Google Summer of Code

An open source intelligence (OSINT) tool that collates threat intel data from more than 80 sources is the latest security platform to emerge from the Honeynet Project.
With a single API request, Intel Owl pulls in scan results of files, IPs, and domains from enterprise-focused threat analysis tools such as YARA and Oletools, as well as external sources like VirusTotal and AbuseIPDB.
The free-to-use application helps non-specialists avoid “gathering noise” while speeding up their organization’s threat intelligence operations, said the project’s architects in a recent blog post announcing Intel Owl’s official release.
Google Summer of Code
A beta version of Intel Owl and released in January was masterminded by Matteo Lodi, threat intelligence lead engineer at Italian security firm Certego, with support from the Honeynet Project.
Keen to upgrade a “very limited” web interface and add further integrations, Lodi submitted a brief to the Google Summer of Code, which pairs student developers with open source projects.
A proposal, including a prototype, was accepted from Eshaan Bansal, an IT undergraduate and open source enthusiast based in New Delhi, India.
Intel Owl “seemed really interesting, matched my techstack and had a few beginner-friendly issues”, Bansal tells The Daily Swig.
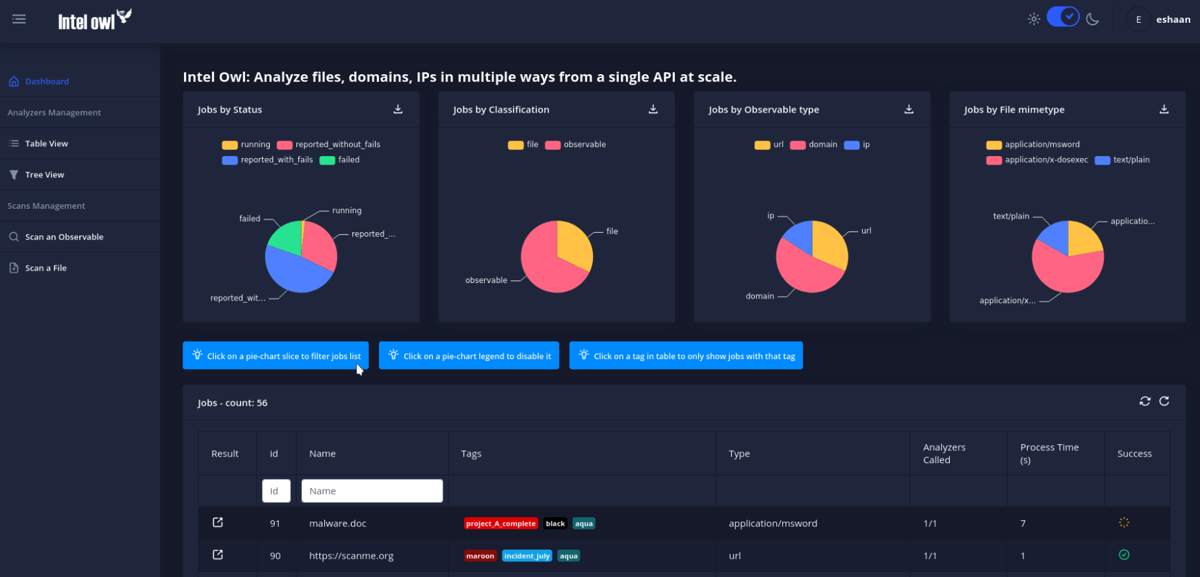 Intel Owl scans files, IPs, and domains from a single API
Intel Owl scans files, IPs, and domains from a single API
Version 1.0.0 of the project emerged a few months later sporting a revamped web interface, complete with dark mode and several new API features.
The dashboard now displays visualized, customizable results from malware and observable scans as soon as they are generated, rather than en masse when the scan finishes.
Users can also tag analyses in order to categorize and filter various scans.
A list of all available analyzers, together with their use case and supported types, can be viewed in a tabular or dendrogram tree view.
Bundled packages
Under the hood, Intel Owl’s internal models can perform static analysis of various file types, as well as strings analysis and PE (Portable Exectable) signature verification. JSON Web Tokens (JWT) are used for authentication.
Bansal also integrated additional analyzers – Team Cymru Hash Registry, Tranco Domain Rank, Cloudflare’s DNS-over-HTTPS malware checker, and YARA with McAfee public rules – into the core API.
Read more of the latest open source software security news
The new Intel Owl web interface is receiving positive feedback, Bansal said. “We have solved various internal architecture problems using design patterns, making it super easy” to integrate analyzers “with just a few lines of code”.
Bansal, who is also a member of capture the flag team Abs0lut3pwn4g3, said he was proudest of “hiding this complexity from the end-user and offering a public interface that is easily customizable” for both users and contributors.
Scaling up
“Intel Owl is fresh, actively maintained and leverages the most recent and trending technologies,” Lodi tells The Daily Swig.
“For instance, the deployment goes seamlessly thanks to Docker,” he says. Kubernetes deployments are possible, and it is “very easy to contribute to, thanks to the Django framework”.
“It is also possible to interact with it in different ways: with the revamped web interface, for a friendly user experience, or with the official python library or CLI tool for advanced users.”
Lodi hailed Bansal’s contribution to a tool that is “really unique and flexible for different use cases.”
Bansal thanked Matteo for helping him to perfect his “proposal”, being “supportive of my ideas” and assisting in solving “various problems regarding code duplicity” and arising as the project scaled up.
The pair, who say the application can be set up within minutes with no extra configuration, have published guidance on installation, usage, and contributing to further development.
Lodi says the next release will have additional analyzers and “basic support for multi-tenancy, for some of the most common authentication methods and for ElasticSearch” to help “more structured organizations to leverage the tool”.
RECOMMENDED Mole in your network: Out-of-band exploitation framework showcased at Black Hat 2020






