New research indicates sharp rise in number of DIY phishing kits being sold on underground forums

UPDATED The market for off-the-shelf phishing kits has both expanded in value and diversified over the last year.
Both the number of phishing kit advertisements that appeared on underground cybercrime bazaars and the number of sellers hawking them doubled last year, according to a new study by threat intel firm Group-IB.
The increase is sellers is easy to understand when set against how lucrative the phishing kit marketplace has become, with DIY cybercrime packages averaging out at $304 per item last year, compared to an average of just $122 in 2018.
According to Group-IB, the price for phishing kits depends on their complexity, the quality and the number of phishing pages, as well as the availability of value-added services such as “technical support”.
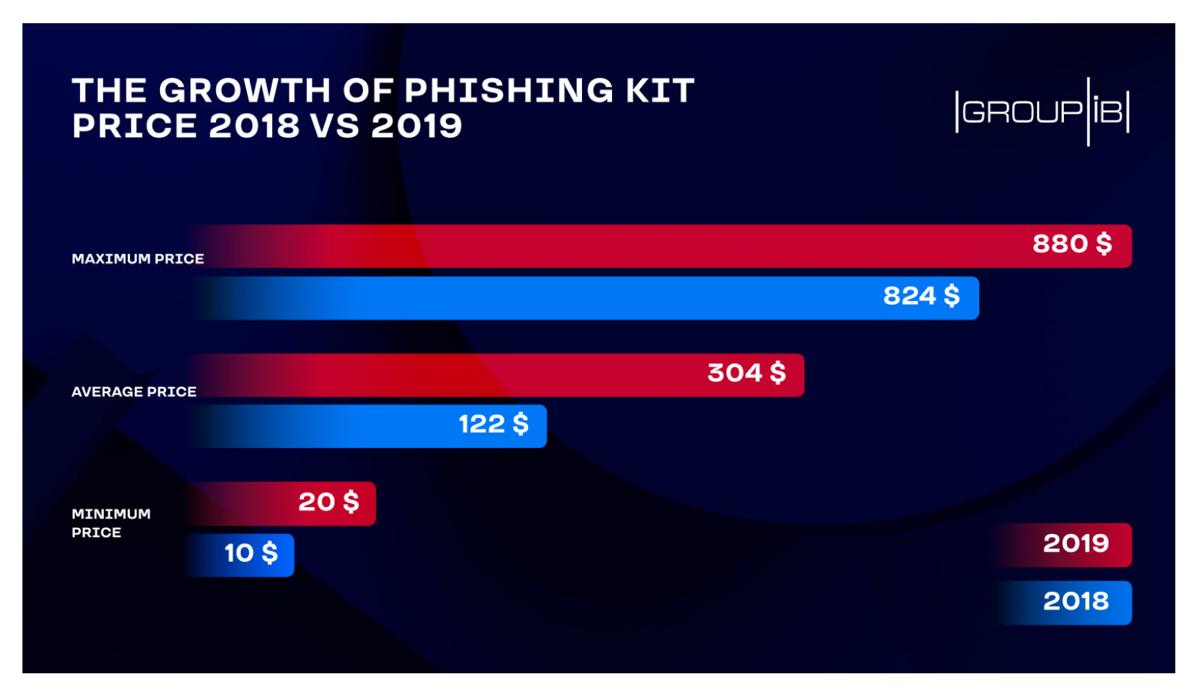 The average price of DIY phishing kits has soared
The average price of DIY phishing kits has soared
Casting the net wide
Phishing kits bundle archive files and scripts that make it straightforward for would-be cybercriminals even with little or no programming skills to create fraudulent sites designed to trick the unwary into handing over their online login credentials.
Historically, phishing fraudsters targeted online bank accounts, but this has changed over time so that the biggest targets last year were Amazon, Google, Office365, and PayPal.
The top three “online markets” for trafficking in phishing kits last year were Exploit, OGUsers, and Crimenetwork, according to Group-IB.
RELATED Charities, IT service workers most easily hoodwinked by phishing attacks – study
More than 16,200 unique phishing kits were detected by Group-IB Threat Intelligence system in 2019.
This huge figure might imply that phishing kits were laying the foundations for the majority of scam sites. However, only 113,460 out of a massive 2.7 million phishing pages detected were developed with a phishing kit.
“Cyber crooks normally remove them or resort to various means to hide them and prevent from being detected by cybersecurity researchers,” according to Group-IB.
Group-IB told The Daily Swig that combatting the boom in phishing kits was important for cybersecurity even though most scam sites avoid using these DIY tools.
“The detection of phishing kits helps to prevent the phishing industry from further expansion, eliminating the production means of this illegal market,” Group-IB explained.
“That’s why cybercriminals understand that their chances to be deanonymized and deprived of their source of income are increasing if the phishing kits are found and normally remove them or hide, which explains why only 4% of the phishing pages detected last year contained a phishing kit.”
Phishing-as-a-Service
Some of the phishing kits were offered free of charge – not because their creators were trying to pump prime the market, but because freebie cybercrime tools came bundled with backdoors that allowed coders to harvest collected data for themselves.
“Phishing kit creators are the driving force of this criminal marketplace – one individual might be behind the creation of hundreds of phishing pages and, even worse, behind the compromise of the personal information of thousands of people,” Group-IB CTO and head of threat hunting intelligence team Dmitry Volkov said in a statement on the research.
The detection of a phishing kit not only helps to locate hundreds or even thousands of phishing pages, but it can also serve as a starting point of an investigation to identify the toolkit’s creator and bring them to justice.
Group-IB has been involved in a number of investigations that resulted in the deanonymization of phishing kit creators.
Volkov explained: “By sharing such info with relevant law enforcers and ensuring the apprehension of cybercrooks, Group-IB seeks to prevent the further spread of ‘disease’ and fight not against its symptoms, phishing pages, but against its causative agent – phishing kit makers.”
This story has been updated to add additional comment from Group-IB
READ MORE When corporate communications smell phishy: Why customers don’t trust your emails






