Researcher profits from investigation of underexplored technology
UPDATED A cross-site scripting (XSS) vulnerability that affected the ‘Login with Facebook’ button has earned a security researcher $20,000.
Vinoth Kumar discovered the DOM-based XSS vulnerability in the technology that gives third-party websites the option to authenticate visitors through the Facebook platform.
The security issue arose because of a flawed implementation of the postMessage API.
The window.postMessage() method enables cross-origin communication between Window objects, for example between a web page and an iframe embedded within.
Kumar described the technology is an underexplored avenue for security bug hunters, hence his decision to look into Facebook’s implementation.
Another security researcher, Enguerran Gillier, recently discovered a technically similar XSS flaw in Gmail, as recently reported by The Daily Swig.
Bug bounty hunt
Kumar began by examining Facebook’s third-party plugins in order to try to locate potential iframe issues. He found a fruitful avenue for exploration when he looked at the Facebook Login SDK for JavaScript.
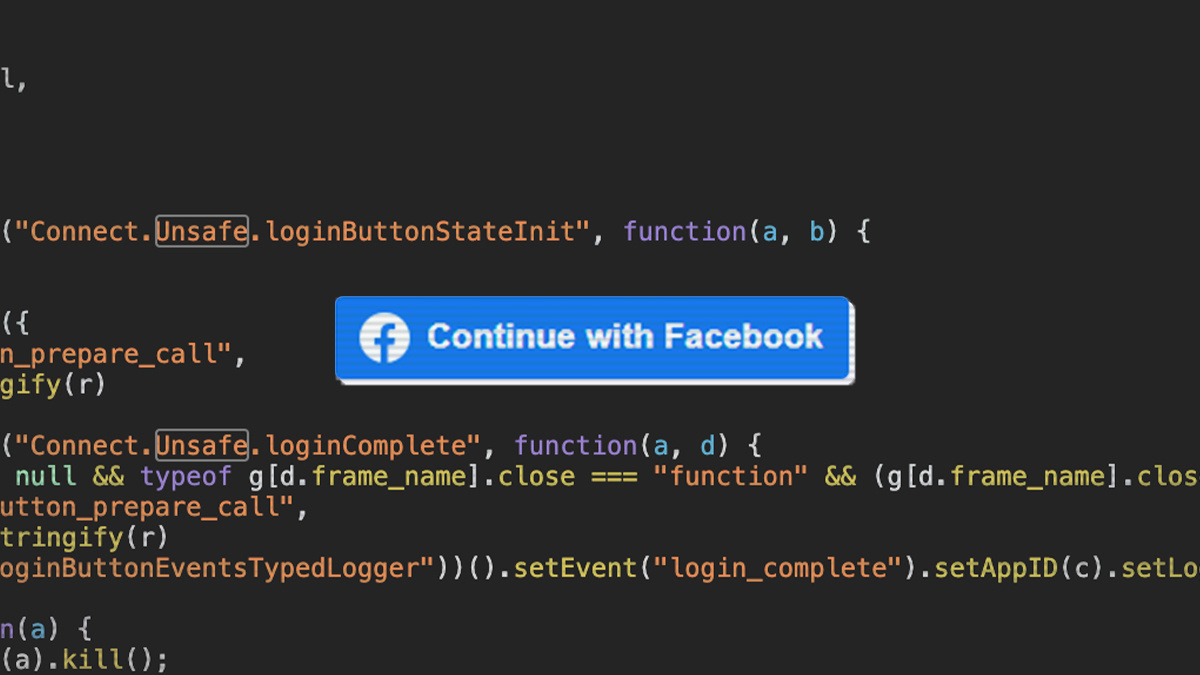
The security researcher realised that there was no URL/schema validation when the JavaScript was being carried out – opening up the possibility of running a DOM XSS-based attack, as Kumar explains in a technical blog post documenting his discovery.
“If we send a payload with url:'javascript:alert(document.domain)’ to the https://www.facebook.com/v6.0/plugins/login_button.php iframe and the user clicks the Continue With Facebook button, javascript:alert(document.domain) would be executed on [the] facebook.com domain.”
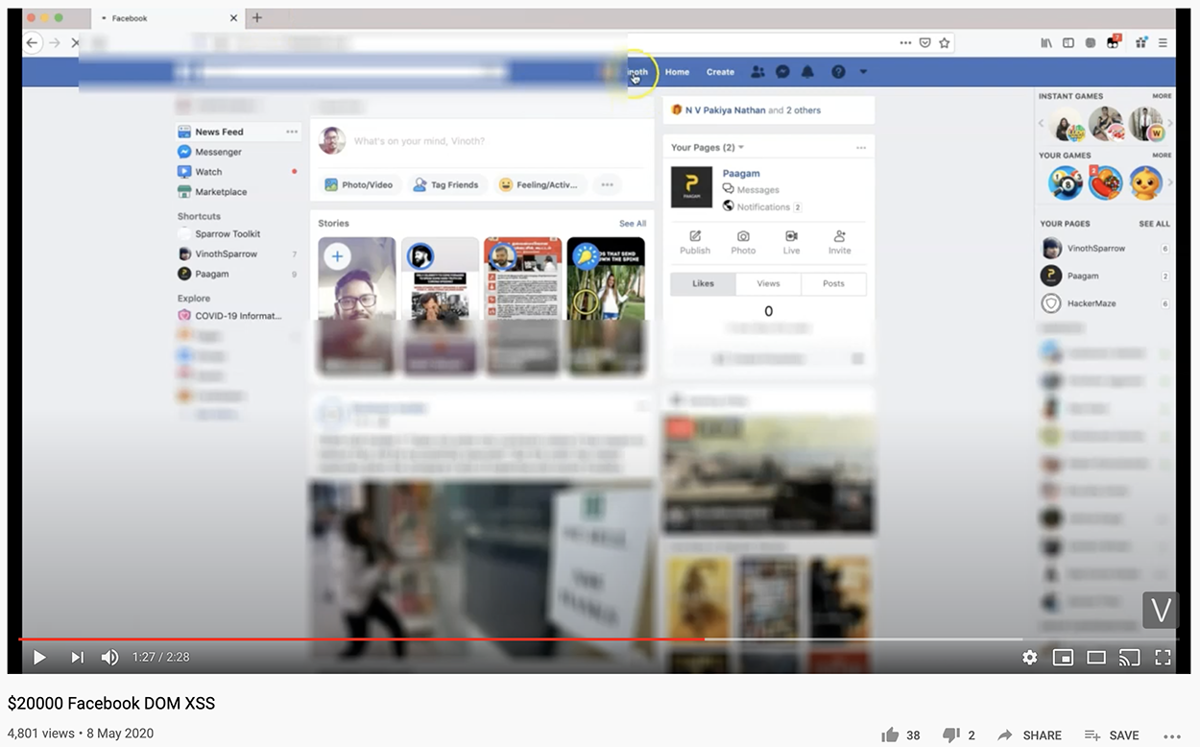 Kumar published a proof-of-concept on YouTube
Kumar published a proof-of-concept on YouTube
Left unresolved, the flaw created a mechanism for a malicious attacker to take over targeted accounts, providing they were able to trick potential marks into clicking on a button on a malicious website.
Kumar explains: “Due to an incorrect post message configuration, someone visiting an attacker-controlled website and clicks login with the Facebook button would trigger XSS on [the] facebook.com domain [on] behalf of [the] logged-in user.”
Read more of the latest bug bounty news
The security researcher’s write-up includes a link to a YouTube video demonstrating a proof-of-concept exploit in action.
The social networking giant confirmed the issue, which it resolved by “adding [a] facebook.com regex domain and schema check in the payload url param,” according to Kumar.
The researcher reported the issue to Facebook on April 17, three before days the social network resolved the security bug. Facebook paid out a $20,000 bug bounty for Kumar’s find on May 1.
Facebook confirmed that it had fixed the bug, adding that its logs showed no malicious exploitation of the security bug discovered by the researcher.
“We’ve fixed the issue and have seen no evidence of abuse," a Facebook company spokesperson told The Daily Swig.
“The bug bounty program has contributed to the safety of the Facebook community since 2011 and we’re thankful to the researcher for reporting this issue to us.”
This story has been updated to add comment from Facebook.






