iLogin
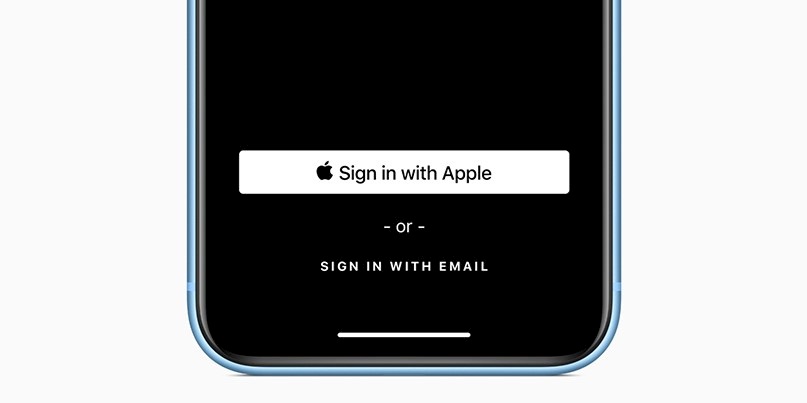
Apple has launched a service that’s pitched as offering the convenience of using a social media account to log in without the privacy downsides.
‘Sign In with Apple’ users have the option of hiding their email address, with Apple creating a random pseudonym address that forwards messages to a user’s primary mailbox.
If a user gets tired of hearing from the developers of a particular app, they can mute alerts from the unique, disposable email address associated with that app.
The tech integrates with Face ID or Touch ID on mobile phones and is designed as an alternative to click-to-login buttons from Google, Facebook, Twitter, and other services.
All accounts are protected with two-factor authentication, with Apple promising not to track users’ activity on apps or websites that support its login technology.
Unveiled at the World Wide Developers Conference (WWDC) yesterday, Sign In with Apple works natively on iOS, macOS, tvOS, and watchOS.
It also works on browsers, as explained in Apple’s run-down of how the technology works.
Breaking the Keychain
The launch of the login technology comes days after a security researcher unveiled a vulnerability in Apple’s in-built password manager technology for macOS.
Keychain offers a means for users to store login credentials for everything from iCloud to Gmail through e-commerce sites and chat apps locally on their Mac, so that their work isn’t constantly interrupted with password prompts.
Independent security researcher Linus Henze discovered flaws that could allow attackers to access passwords inside Keychain without a user prompt.
The vulnerability creates the means for a malicious application to snaffle passwords from Apple’s protected keychain, providing users are first tricked into downloading dodgy software.
Apple patched the vulnerability back in March.
A proof of concept tool – entitled KeySteal – was released after a presentation by Henze at the Mac-focused Objective By the Sea conference in Monaco last weekend.
A second highlight from the security event was the unveiling of a vulnerability in Apple’s support for serial line modems – tech dating back to the 1990s that first shipped with iMacs.
Joshua Hill, chief research officer at Sudo Security Group, presented his findings along with proof of concept code.
The exploit only works on certain early generations of OS X and macOS. Controls introduced by Apple with macOS Sierra in 2016 make the bug impractical to exploit.
For the rest, Apple introduced a patch back in April.






