Web browser also hampers bounce tracking, among other tweaks, across all latest Apple OS updates

Apple has bolstered Safari’s protections against third-party trackers by rolling out new mechanisms for blocking CNAME cloaking and bounce tracking.
Safari 14 on Big Sur, the major MacOS update launched yesterday (November 12), can now detect third-party CNAME cloaking requests by capping the expiry of cookies set in third-party, CNAME-cloaked HTTP responses to seven days.
Part of a raft of tweaks to WebKit’s Intelligent Tracking Prevention (ITP) feature, the seven-day limit mirrors ITP’s expiry cap on cookies created through JavaScript, which CNAME cloaking can circumvent.
Read more of the latest privacy news
The bounce tracking detection feature and other ITP tweaks are also incorporated into Catalina and Mojave, iOS 14, and iPadOS 14, according to a post on the WebKit blog.
WebKit engineers have also joined other browsers in their efforts to standardize storage partitioning by allowing partitioned and ephemeral third-party IndexedDB, enabling full third-party cookie blocking by default so that ITP can learn about cross-site trackers during private browsing, and explicitly exempted home screen web applications from the seven-day cap on all script-writeable storage introduced in March.
What Is CNAME cloaking?
‘CNAME cloaking’ disguises third-party trackers as first-party trackers, thereby circumventing ad blockers, by assigning a subdomain for data collection and tracking, linking it to an external server with the CNAME DNS record.
Found in the Domain Name System (DNS), a Canonical Name (CNAME) record maps domain name connections so that multiple services, such as an FTP server and web server running on different ports, can run from a single IP address.
Wilander illustrated how the technique works in a table:
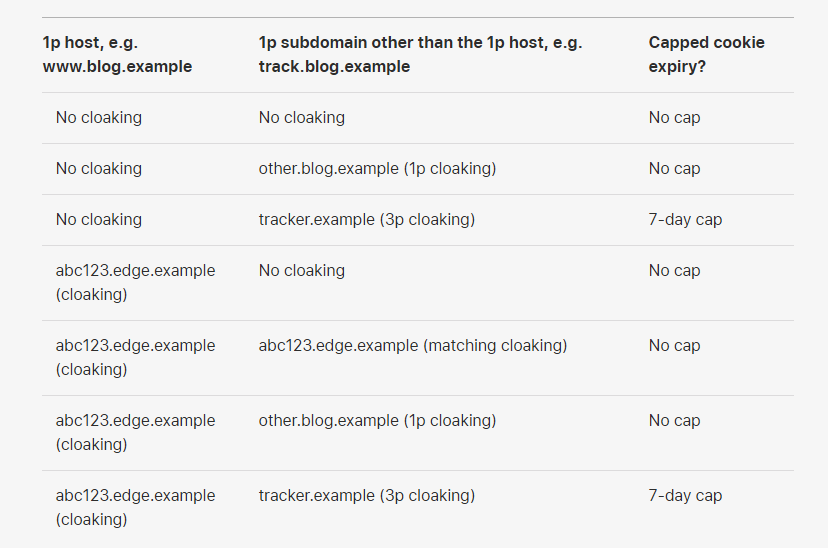
Widespread technique
With the likes of Mozilla now blocking third-party tracking cookies and cryptominers by default, ad tech firms have increasingly encouraged clients to deploy CNAME cloaking.
Of Alexa’s top 300,000 websites, 1,762 websites deployed the technique on 56 trackers, a team of academics recently found.
This included foxnews.com, walmart.com, and bbc.co.uk as of November 2019, as reported by The Daily Swig.
 Apple Safari is built on the WebKit browser engine
Apple Safari is built on the WebKit browser engine
Improperly managed CNAME records can pose a grave security risk, with 250 websites belonging to banks, healthcare companies, restaurant chains, and civil rights groups recently hijacked via old DNS records, for example.
As well as being a potential security risk, the technique will soon become even less effective, with privacy-focused web browser Brave recently unveiling its own mechanism for blocking CNAME cloaking.
YOU MIGHT ALSO LIKE Brave browser acts quickly to resolve Tor session confidentiality bug
Bounce tracking detection
Bounce tracking is now detected through SameSite=Strict jail, which “at a certain threshold”, rewrites “all the tracking domain’s cookies to SameSite=strict”, removing them from cross-site, first-party navigations and simple, redirect-based bounce tracking, said Apple WebKit engineer John Wilander.
The mechanism was developed after WebKit engineers learned of a website using the technique successfully, although the site has since discontinued the practice.
Also known as redirect tracking, bounced tracking is used by trackers to briefly redirect users to their website in order to track them between domains.
RELATED Apple provides technical steer on Face ID, Touch ID authentication for websites






