Machine learning could be the key to preventing cyber-attacks

Artificial intelligence can help internet service providers prevent DDoS attacks before they happen, say researchers.
Findings from the National University of Singapore and Ben-Gurion University of the Negev, Israel, presented a new method in the peer-reviewed journal Computers & Security.
The method uses machine learning to detect vulnerable smart home devices, which are an attractive target for hackers who assemble botnets to launch DDoS attacks.
The machine learning detector does not invade customers’ privacy and can pinpoint vulnerable devices even if they’re not compromised.
Detecting devices behind the NAT router
“To the best of my knowledge, telcos monitor the traffic and can only detect DDoS attacks once they are executed, which might be too late,” Yair Meidan, Phd student at Ben-Gurion and the research team lead, told The Daily Swig.
“In contrast, our method proposes means to detect potentially vulnerable IoT devices before they are compromised and being used to execute such attacks.
“Once these potentially harmful devices are detected, risk-mitigating actions can be taken.”
Read more of the latest DDoS attack news
Home IoT devices such as smart security cameras, lightbulbs, fridges, and baby monitors are notoriously renowned for their poor security and are often used in DDoS attacks.
Meanwhile, most customers don’t have the technical know-how and awareness to secure their smart home devices or monitor their network for compromised devices. This puts the burden of detecting vulnerable IoT devices on the shoulders of the ISPs.
The idea for the project originated from a telco (telecommunications provider) that faced serious risks to its infrastructure due to IoT-related DDoS attacks, Meidan said, though he did not name the company.
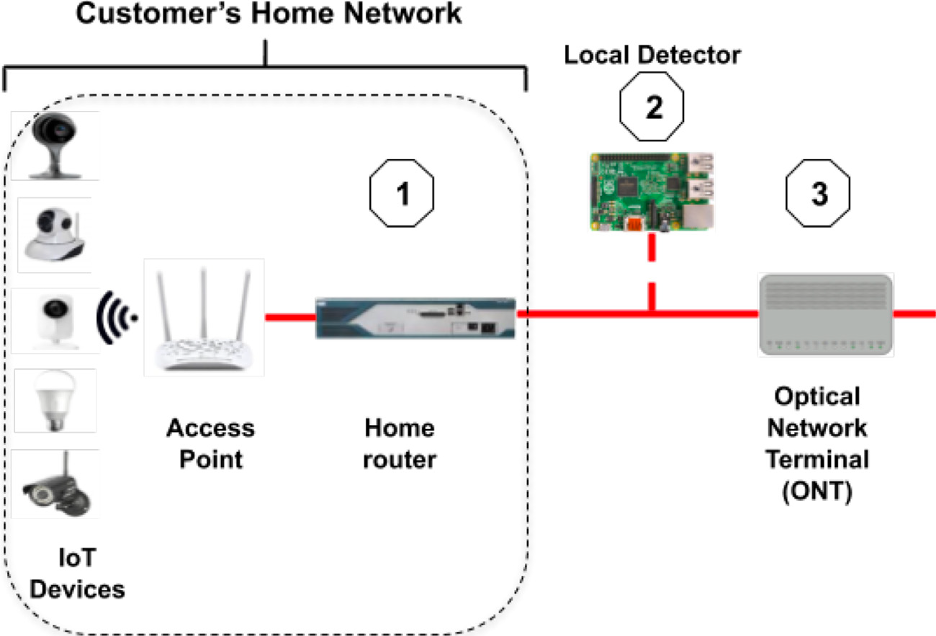
One of the key challenges of detecting vulnerable smart home devices is that they’re hidden behind a network address translation (NAT) router and share a common IP address outside the home network, which makes it hard for the telco to tell them apart.
YOU MAY LIKE Adversarial attacks against machine learning systems – everything you need to know
One workaround is to use deep packet inspection (DPI). But DPI is both computationally expensive and puts the private communications of ISP customers at risk.
And with most internet traffic being encrypted, DPI becomes virtually impossible unless telcos take more privacy-intrusive methods such as installing monitoring devices inside customers’ home networks.
Instead of packet inspection, the researchers at Ben-Gurion and Singapore National universities use supervised machine learning to identify NATed devices by performing statistical analysis on the router’s outbound traffic.
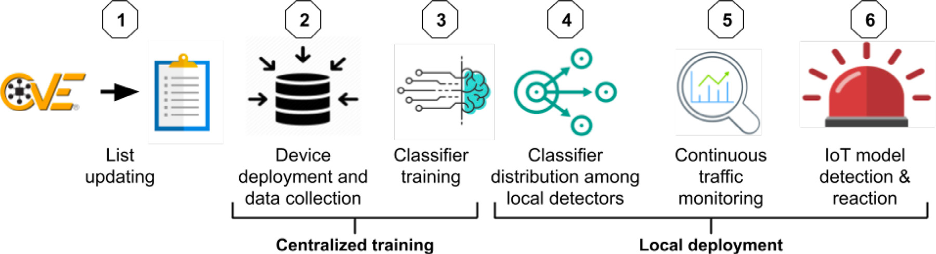
Training and deploying the machine learning model
The proposed method uses the CVE and NVD lists as a source for vulnerable home IoT devices. To create the detector, telcos must set up a lab home network in which they install various IoT and non-IoT devices. The network also includes instances of vulnerable IoT devices.
The machine learning detector is trained on NetFlow data collected from the router to detect known patterns of vulnerable IoT devices.
In short, the detector will look at the outgoing traffic of a router and let you know if a known type of vulnerable IoT device is behind it.
The model is trained on normal network traffic, which means it can detect vulnerable devices even if they haven’t been compromised and aren’t engaged in malicious activity.
 Artificial intelligence can be used to help protect against DDoS attacks
Artificial intelligence can be used to help protect against DDoS attacks
Setting up the lab and training the machine learning model will cost telcos several thousand dollars. But the cost is considerably lower than the consequences of a DDoS attack, Meidan points out.
“Such an attack is likely to cause internet service downtimes, which might translate into customer churn as well as long-term damage to the telco’s reputation and its ability to compete with other telcos in terms of the increasingly important QoE (Quality of Experience) measure.”
Read more of the latest IoT security news
To cut costs, Meidan says, telcos can train their detector “on a small, yet effective subset of IoT models, i.e. the specific IoT models that are found vulnerable to botnet infections and have the largest install base”,
The trained detector model can run on a low-cost computer such as a Raspberry Pi, which allows for a decentralized deployment model where local detectors are installed between customers’ home routers and the optical network terminal.
Once a vulnerable device is identified, telcos can reroute the traffic, apply virtual patching, or notify the customers to take the proper measures.
 Low cost options can be used to help identify vulnerable home devices
Low cost options can be used to help identify vulnerable home devices
“We plan to broaden the evaluation to a larger variety of IoT models from various manufacturers, and also evaluate the method’s resilience to adversarial attacks,” says Meidan, adding that the researchers are considering expanding their work beyond smart home devices to other sectors where the method might be feasible and beneficial.
READ MORE DDoS attacks continue to surge during coronavirus pandemic






