Zero-day requires attackers to have author status
Millions of websites are at risk of being compromised by malicious authors, researchers have warned.
Security analysts at RIPS Tech said yesterday that WordPress sites are susceptible to being overtaken by malicious authors, due to a bug found within the core of the popular content management system (CMS).
Core files, which decide the appearance and functionality of the WordPress site, can be deleted. By deleting specific files, anyone with access to an author account can take over the site.
The zero-day vulnerability – originating with the PHP function used to delete thumbnails of images – was reported to WordPress seven months ago, according to the RIPS Tech team.
WordPress acknowledged the problem at the time and estimated in January that it would take 6 months to fix the problem.
RIPS Tech decided to make the vulnerability public after the CMS consistently failed to patch the issue or provide any update.
Writing on the RIPS Tech blog, researcher Karim El Ouerghemmi said: “Exploiting the vulnerability grants an attacker the capability to delete any file of the WordPress installation (+ any other file on the server on which the PHP process user has the proper permissions to delete).
“Besides the possibility of erasing the whole WordPress installation, which can have disastrous consequences if no current backup is available, an attacker can make use of the capability of arbitrary file deletion to circumvent some security measures and to execute arbitrary code on the webserver.”
An attacker, however, is required to have author status in order for the exploit to be effective.
While the need to gain access to a site’s privileges perhaps puts the vulnerability at a lower risk, an attacker only needs to compromise a low-level user to conduct the exploit.
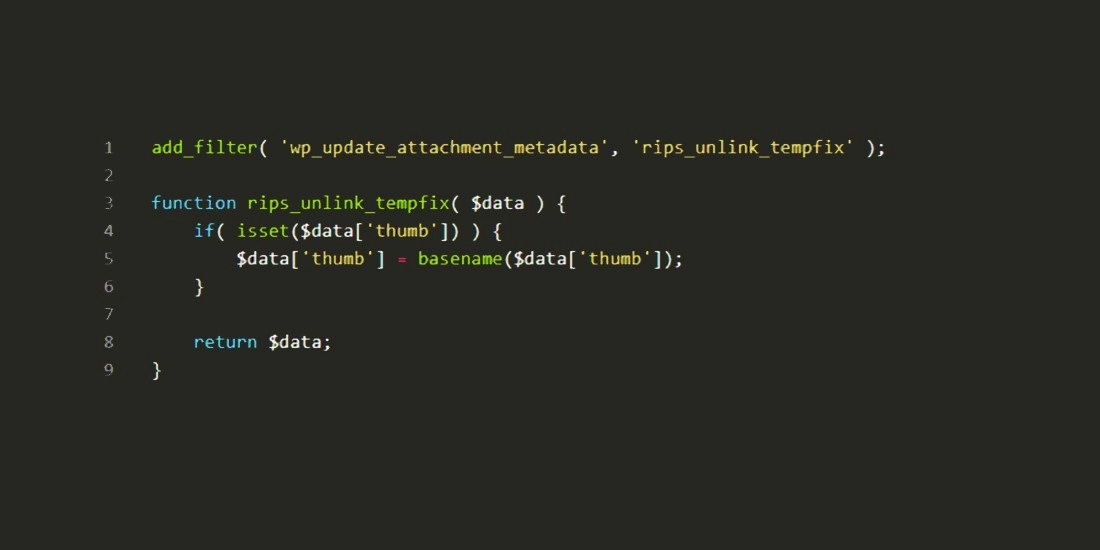
RIPS Tech has created a temporary fix to prevent attackers leveraging the exploit.
The Daily Swig has reached out to WordPress for comment.






