Site admins urged to remove Captcha, despite fix
The owner of the Captcha plugin for WordPress has reportedly been blocked from publishing updates to the extension’s source code without review, after researchers found a backdoor that allowed the author to gain unauthorized administrative access to websites running the add-on.
With more than 300,000 active installations, the Captcha plugin is pegged as a “super security” verification tool that protects website from spam by requiring users to complete simple mathematical equations when they want to login or post comments.
However, after noting the plugin had recently been removed from the WordPress repository, security researchers at Wordfence decided to dig around in the source code to see if there was any evidence of foul play.
“Whenever the WordPress repository removes a plugin with a large user base, we check to see if it was possibly due to something security-related,” said Matt Barry, lead developer at Wordfence.
The researchers found code that triggers an automatic update process. A Zip file containing small code changes from that which appears in the Captcha plugin repository was found to contain a file called plugin-update.php, which is a backdoor.
“This backdoor creates a session with user ID 1 (the default admin user that WordPress creates when you first install it), sets authentication cookies, and then deletes itself,” Barry explained. “The backdoor installation code is unauthenticated, meaning anyone can trigger it.”
Following a trail of domains associated with Simplywordpress, which obtained ownership of the Captcha plugin three months ago, Wordfence said the extension is now linked to an individual who has a history of purchasing plugins in order to place cloaked backlinks on users’ sites.
“He then uses these backlinks to increase page rank in search engine results pages, since only web crawlers such as Googlebot can read them,” Barry said.
Wordfence identified five other plugins owned by Simplywordpress – Covert me Popup, Death to Comments, Human Captcha, Smart Recaptcha, and Social Exchange. All five plugins were found to contain the same backdoor installation code.
Since its discovery of the vulnerability, Wordfence said it partnered with the WordPress.org plugins team to release a patched version of Captcha (4.4.5). This version is now available, and over the past weekend more than 100,000 sites running the plugin were automatically updated.
While Wordfence said the Captcha author has been blocked from publishing future updates to the plugin without review, it is now questionable whether site admins would wish to continue to use the extension following the discovery of the backdoor.
Indeed, the fact the plugin has been restored on the WordPress repo didn’t escape the attention of some forum members: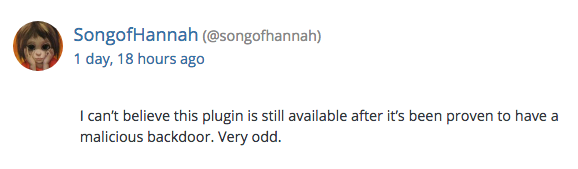
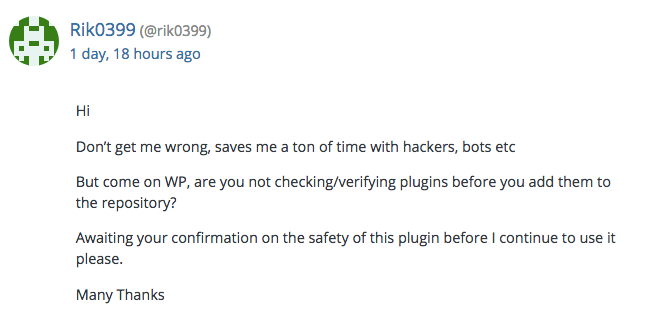
Following its investigation, Wordfence urged users to steer clear of the add-on altogether.
“We recommend that you uninstall the Captcha plugin immediately from your site,” Barry said. “Based on the public data we’ve gathered, this developer does not have user safety in mind and is very likely a criminal actor attempting yet another supply chain attack.”






