HTTPS padlock gives users a false sense of security when downloading files

Chrome will start blocking HTTP downloads started on secure (HTTPS) web pages – so-called ‘mixed content downloads’ – in a phased rollout culminating in October’s release of Chrome 86.
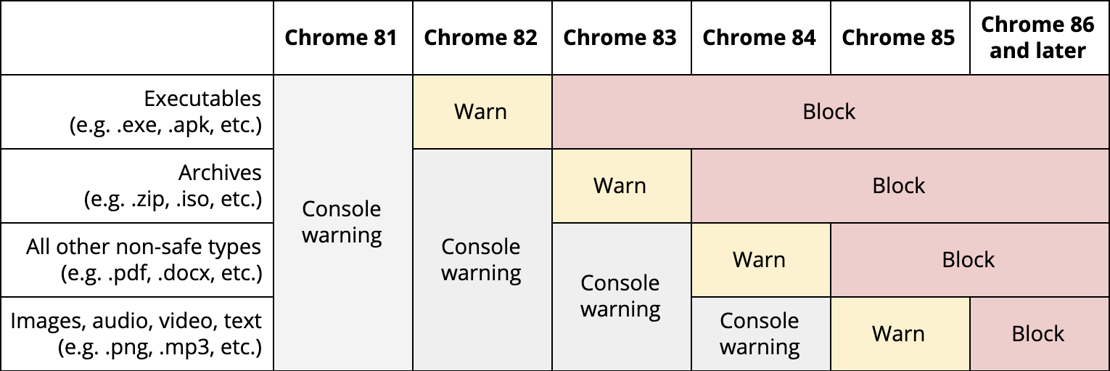
In a post published on the Google Security Blog last week, Joe DeBlasio of Chrome’s security team outlines how mixed content downloads of executables such as .exe – the most common vehicles for malware – would initially be blocked in June’s release of Chrome 83.
The download restrictions, which were first outlined in April 2019, will then widen to include archives (.zip) and disk images (.iso) in Chrome 84, slated for an August rollout, then other mixed content apart from images, audio, video, and text in Chrome 85 in September.
In Chrome 86 and beyond (released October 2020), Chrome will block all mixed content downloads.
 Google is launching a phased rollout of mixed content downloads
Google is launching a phased rollout of mixed content downloads
Positive trust indicators
While encrypted HTTPS sites are inherently more secure than HTTP sites, if they host files that are downloaded using the HTTP protocol they could still be putting users at risk.
Google is acting on concerns that many users will see the ‘HTTPS’ and accompanying padlock in a site’s address bar as indicators that any files available for download on the page will also be secure.
“All insecure downloads are bad for privacy and security,” said DeBlasio in a Twitter thread explaining the move. “An eavesdropper can see what a user is downloading, or an active attacker can swap the download for a malicious one.”
Addressing developers, the security engineer added: “Think of it like mixed content blocking, but for downloads. You can’t load insecure content on your HTTPS page, and you shouldn’t download insecure files either.”
Phased rollout
Chrome 81 (which will also withdraw support for TLS) will usher in the rollout in March with a console message warning against mixed content downloads.
The changes will kick in one release later for mobile platforms Android and iOS, which are said to have “better native protection” against malicious files.
Read more of the latest browser security news
“This gradual rollout is designed to mitigate the worst risks quickly, provide developers an opportunity to update sites, and minimize how many warnings Chrome users have to see,” said DeBlasio.
He also urged developers to “fully migrate to HTTPS to avoid future restrictions and fully protect their users”.
The blog post additionally explains how developers can activate a warning on all mixed content downloads for testing in the current version of Chrome Canary, and how enterprise and education customers can disable blocking on a per-site basis.
RELATED Chrome SameSite cookie change expected to result in ‘modest’ global website breakage






