DHS and FBI provide details of ‘Fallchill’ malware allegedly used by North Korea

In an effort to help protect government and private enterprises from future cyber-attacks emerging from North Korea, the US Department of Homeland Security (DHS) and FBI have issued a joint technical alert that provides details and methods associated with the proliferation of a malware strain dubbed ‘Fallchill’.
The US government refers to malicious cyber activity allegedly instigated by the North Korean government as ‘Hidden Cobra’, while others have adopted the namesakes ‘Lazarus Group’ and ‘Guardians of Peace’ in their reports.
Whichever nom de guerre you prefer, DHS said North Korean actors have leveraged their capabilities to target and compromise a range of high-profile victims since 2009. Notable attacks linked with Hidden Cobra include those focused on Sony Pictures and other media outlets, aerospace and financial sectors, and critical infrastructure systems around the world.
Now, with the aim of enabling network defenders to identify and reduce exposure to North Koean cyber activity, the US government’s latest technical alert has listed hundreds of IP addresses and other indicators of compromise (IOCs) associated with a remote administration tool (RAT) purportedly used by the North Korean government – commonly known as Fallchill.
“According to trusted third-party reporting, Hidden Cobra actors have likely been using Fallchill malware since 2016 to target the aerospace, telecommunications, and finance industries,” the joint technical report states.
“The malware is a fully functional RAT with multiple commands that the actors can issue from a command and control server to a victim’s system via dual proxies.”
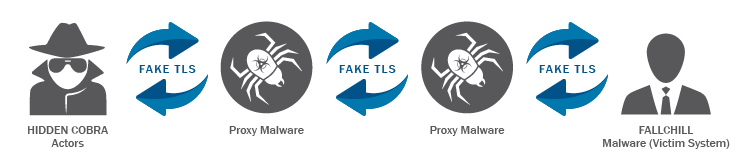
According to DHS, Fallchill typically infects a system as a file dropped by other Hidden Cobra malware or as a file downloaded unknowingly by users when visiting compromised sites.
“Hidden Cobra actors are also understood to be using an external tool or dropper to install the Fallchill malware-as-a-service to establish persistence,” DHS said. “Because of this, additional Hidden Cobra malware may be present on systems compromised with Fallchill.”
A successful network intrusion can have severe impacts, including the temporary or permanent loss of sensitive or proprietary information, disruption to regular operations, financial losses incurred to restore systems and files, and potential harm to an organization’s reputation.
In order to reduce the likelihood of a Fallchill infection, administrators have been urged to use application whitelisting to help prevent malicious software from running; keep operating systems and software up-to-date with the latest patches; maintain up-to-date antivirus software; restrict users’ abilities to install and run unwanted software applications; and avoid enabling macros from email attachments.
“If users or administrators detect activity associated with the Fallchill malware, they should immediately flag it, report it to the DHS National Cybersecurity and Communications Integration Center or the FBI Cyber Watch, and give it the highest priority for enhanced mitigation,” DHS stated.
A downloadable copy of the Fallchill IOCs is available here.






