As the number of entries in the CVE database surpasses the 100,000 mark, board members Chris Levendis and Kent Landfield take stock of the program’s journey to becoming the world’s de facto vulnerability identification standard
For the past 20 years, the Common Vulnerabilities and Exposures (CVE) list has been synonymous with security – and for good reason.
Since 1999, the industry initiative – overseen by the CVE board and maintained by Mitre Corporation – has been providing common identifiers for publicly known cybersecurity vulnerabilities, including everything from relatively minor flaws, such as missing HTTPOnly flags, all the way to headline-hitting exploits such as EternalBlue (CVE-2017-0144).
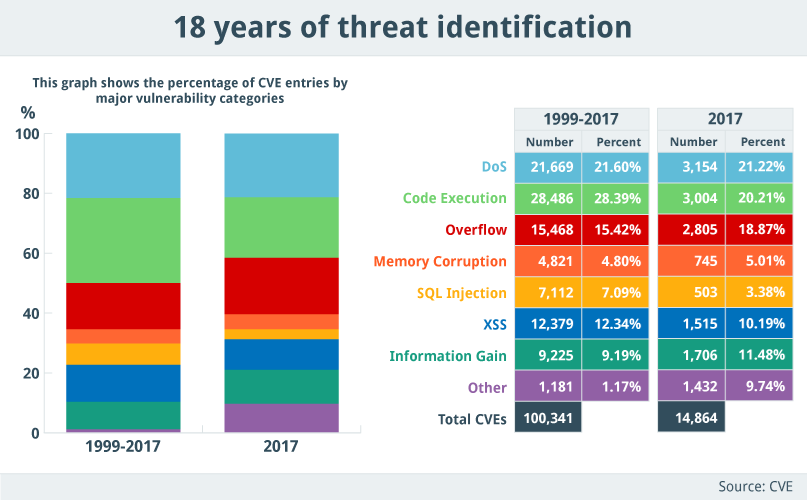
If ever proof were needed that the security industry is evolving at a rapid pace, the CVE program recently announced that the CVE list had surpassed 100,000 entries – a dubious milestone that demonstrates the program’s diligence, while hammering home the sheer scale of the threat landscape in 2018.
With an average of 40 new entries being added to the database per day, the CVE initiative is now more vital than ever, as it provides those in the security community with a single point of reference when it comes to identifying and mitigating threats.
The seemingly never-ending wave of software flaws and threats is compounded by the rise of new technologies – including mobile, cloud, and IoT – each of which has its own unique vulnerability profile.
In light of these projections, the CVE program has recently been ramping up the number of CVE Numbering Authorities (CNAs), each of which is authorized to assign CVE IDs to vulnerabilities affecting products within their distinct, agreed-upon scope.
And for the CVE board, the addition of new CNAs has set the CVE initiative firmly on the path to a federated structure, as security experts look ahead to the next 20 years of threat identification.
Identity parade
“CVE was started as a community back in 1999,” explains Chris Levendis, CVE program lead. “At that point there were different product vendors and different vulnerability databases.
“Everyone was using their own vocabulary, so that when two or more people were discussing a vulnerability you just had to work through the problem of knowing that you were using a different vocabulary when talking about the same vulnerability.”
“And so what CVE does is identifies and names those vulnerabilities and has essentially evolved into the de facto standard for doing so, over the last 20 or so years.”
Kent Landfield, chief standards and technology policy strategist at McAfee and CVE board member, notes that issues surrounding vulnerability identification go far beyond that of vocabulary.
“I’ve been around for the entirety of the program, and when we originally started this, part of the real problem we had was operational,” he told The Daily Swig.
“Let’s say you had an intrusion detection product in place in your security operations, and something would trigger on a threat that’s coming in.
“Each product would have their own name for it, so if you happened to have a defense-in-depth strategy, where you would have two, three, or four different products, you ended up with a situation where you were chasing your tail, because there was no way to correlate that these were all the same vulnerability.”
Safety in numbers
The Mitre Corporation is an independent third-party, funded by the Department of Homeland Security to operate the CVE program. This is a little misleading, however, as recent years have seen a proliferation in the number of CNAs, who have been brought on board to assist with the program.
“When you look at our program’s structure, we have the CVE board, which is comprised of industry, academics, and government stakeholders from all over the world who provide absolutely essential strategic, operational, and governance advisory functions,” said Levendis.
“But we now have 87 CNAs in the program, who are all involved in the assignment process and help chart the path forward.”
Given the rapidly evolving threat landscape, Levendis said the role of the CNAs is only going to become more vital in the years to come. “The CNAs are going to be the primary means by which we scale the CVE program,” he stated.
“They are going to play an absolutely essential role going forward, as they have been playing since around 2005, when we first came up with the concept of the CNA and have been growing it from there.
“As far as onboarding CNAs is concerned, the program will strategically look to target certain organizations to fulfil different kinds of roles. We have open and transparent rules for the requirements to become a CNA.”
He added: “To become the numbering authority you have to demonstrate a mastery of the ability to assign CVEs consistent with the established guidelines, and then you have to be willing to operate within the program’s structure and the rules that govern our program – all of which are available to the public online.”
Industry touchstone
Nineteen years is a long time in the security world, but the CVE program’s focus is still set squarely on vulnerability identification.
Times change, however, and as the organization looks ahead to the next two decades, the CVE board is currently looking to expand into what Landfield called a “total federated architecture” – and CNAs will sit at the heart of this evolution.
“From a program perspective, we would much rather have the ‘source of truth’, when it comes to vulnerabilities coming from the vendors,” he noted. “They are the ones who know their software the best.
“The problem is that we have yet to figure out how to write secure software on a consistent basis. So programs like CVE are going to be vital for making sure that that kind of information is made available.
“During the next year or so, we’re going to be putting in place lots of different pieces and parts to ensure that federated environment actually occurs, and that we have set ourselves up for the next 20 years.”
According to Landfield, automation is a key action point for the CVE initiative. “We have built working groups into the program that allow the board members, the CNAs, and the public to participate in trying to develop some of that automation,” he said.
“CVE is really a fundamental piece of our security defense mechanisms. This information is used in security advisories, vulnerability databases, vulnerability assessment automation, remediation, intrusion detection, intrusion monitoring – it goes on and on and on.
“But this is not just a Mitre program,” he added. “I would like to stress the sheer number of external participants who take part in this program. CVE is vital to the security industry, and vital to our ability to defend ourselves.”






