CISA and MITRE’s latest CWE shakeup reveals the most severe threats impacting enterprise software today
MITRE has published the 2022 CWE most dangerous software bugs list, highlighting that enterprises still face a raft of common weaknesses that must be protected from exploitation.
The 2022 Common Weakness Enumeration (CWE) Top 25 Most Dangerous Software Weaknesses list was made public last week. The CWE Top 25 is the work of the Homeland Security Systems Engineering and Development Institute, sponsored by CISA and operated by MITRE.
The list attempts to provide a comprehensive guide for developers, researchers, and executives in prioritizing and mitigating risk regarding exploitable software issues.
The CWE Top 25 list uses datapoints from CVE data in the NIST National Vulnerability Database (NVD), Common Vulnerability Scoring System (CVSS) scores assigned to new CVE records, and information from the CISA Known Exploited Vulnerabilities (KEV) catalog.
“Often easy to find and exploit, these can lead to exploitable vulnerabilities that allow adversaries to completely take over a system, steal data, or prevent applications from working,” CISA says.
CWE Top 25 – movers and shakers
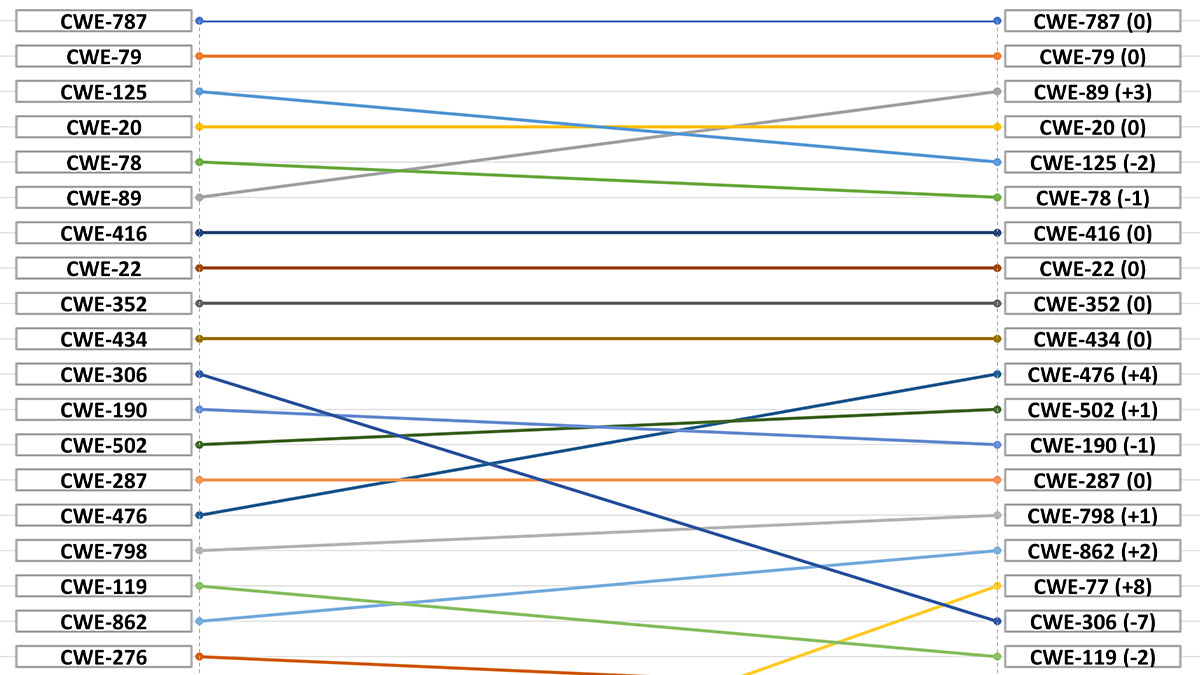
This year’s submission contains 37,899 CVE records gathered over the past two years. The top 10 software issues included in the list are below:
- CWE-787 – Out-of-bounds Write
- CWE-79 – Improper Neutralization of Input During Web Page Generation (Cross-site Scripting)
- CWE-89 – Improper Neutralization of Special Elements used in an SQL Command (SQL Injection)
- CWE-20 – Improper Input Validation
- CWE-125 – Out-of-bounds Read
- CWE-78 – Improper Neutralization of Special Elements used in an OS Command (OS Command Injection)
- CWE-416 – Use After Free
- CWE-22 – Improper Limitation of a Pathname to a Restricted Directory (Path Traversal)
- CWE-352 – Cross-Site Request Forgery (CSRF)
- CWE-434 – Unrestricted Upload of File with Dangerous Type
Out of the movers and shakers in the top 10 most dangerous software weaknesses, MITRE has bumped SQL injection risks up three places compared to 2021. However, out-of-bounds read and OS Command Injection have dropped in detection and severity.
Currently in 11th place is NULL Pointer Dereference, which occurs when a pointer expects to be valid but causes an application to crash or exit. This has crept up four places since 2021 and we may expect this type of software vulnerability to earn a top 10 place in future lists if it continues to climb.
Authentication issues persist
Authentication and authorization issues continue to plague the Top 25 list with the appearance of improper authentication, missing authorization, and the use of hardcoded credentials.
However, it does appear that enterprises are beginning to take data protection more seriously.
For example, the exposure of sensitive information to those without authorization has dropped from number 20 to 33; insufficient credentials protection has moved from the 20th spot to number 22, and the incorrect assignment of permissions to critical resources has moved from number 22 to 30.
Read more of the latest information security industry news
New entries into the Top 25 include CWE-362, Race Conditions, moving from spot 33 to 22; CWE-94, Code Injections, from number 28 to 25; and CWE-400, Uncontrolled Resource Consumption, from spot 27 to 23.
According to MITRE, there is a general transition from class-level, or ‘abstract’ weaknesses to base-level issues, which are “typically associated with groups of specific languages, technologies, or resources.”
“With viruses, phishing and data theft surrounding us all, web security threats can cause huge disruption to business operations, from malware infecting networks to being able to delete data or hold it to ransom,” said Jake Moore, global cybersecurity advisor at ESET, a cybersecurity firm.
“Businesses must follow simple yet effective standards, such as ensuring all devices and software are up-to-date, enabling multi-factor authentication and creating offline and online backups – not to mention testing them – to prepare for the worst eventuality.”
The Daily Swig has reached out to MITRE and we will update when we hear back.
READ MORE HTTP/3 evolves into RFC 9114 – a security advantage, but not without challenges






