Malwarebytes Labs publishes its annual State of Malware report

An annual study on the international cyber threat landscape has shown that businesses are bearing the brunt of increasingly complex forms of malware.
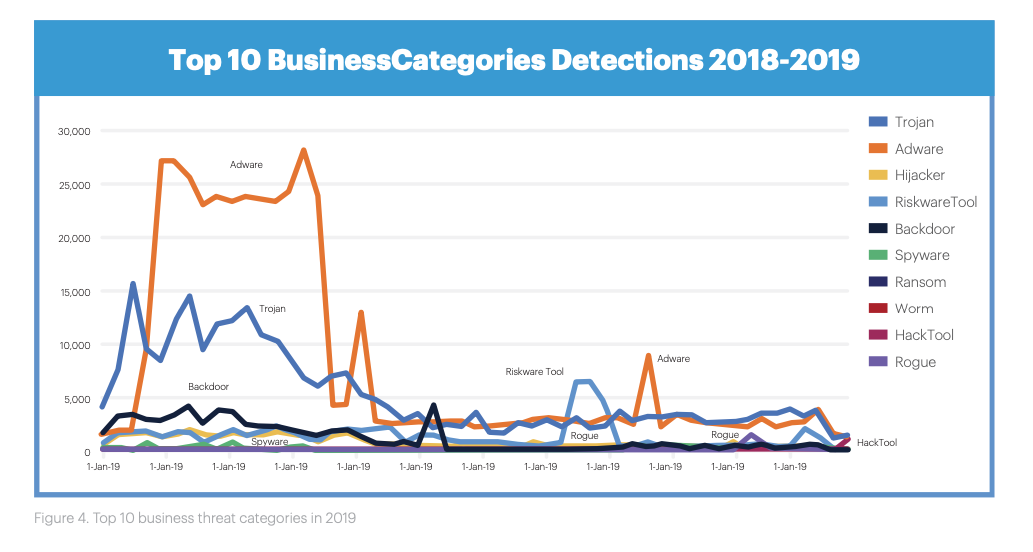
The 2020 State of Malware report, published today (February 11) by cybersecurity firm Malwarebytes, said that attacks on business endpoints have risen by 13% year on year.
The enterprise attack surface continues to be a more lucrative target to cybercriminals, the report says, with sophisticated toolkits including adware, Trojan horse software, and hacking tools being used at an advancing rate.
Much like the previous year, threat actors showed a preference for deploying the evolving Trojans Emotet and TrickBot on businesses. Detections of Trickbot on enterprise networks surged by 52% in 2019, according to Malwarebytes data.
Cases of Emotet, formally one of the top trojans used against consumers, has now become one of the main culprits behind attempts at business intrusion.
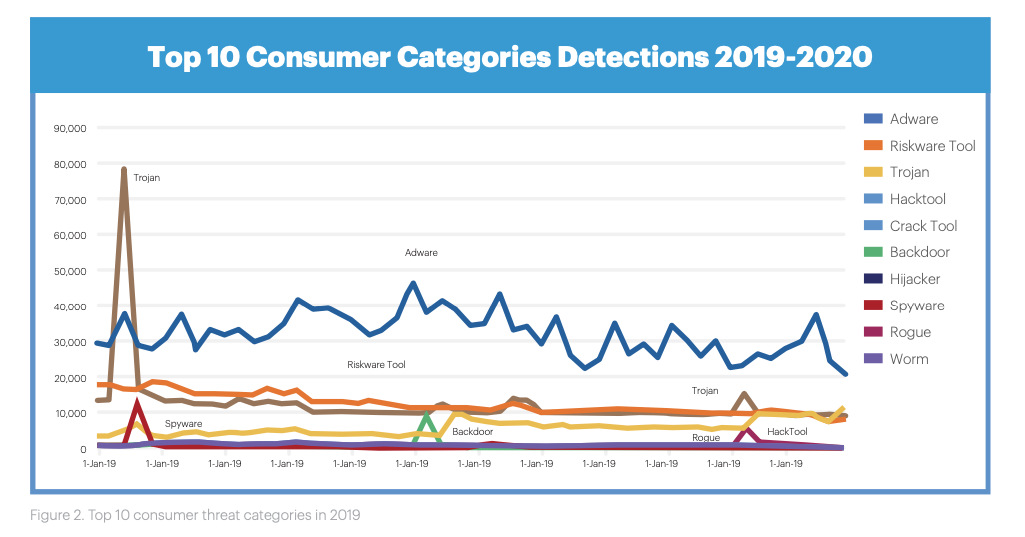
“We expect to see Trojan malware continue to be a problem for consumers in 2020, but less so than other threats, and especially less than in previous years,” the report said, adding that Trojan-fuelled cybercrime activity in the consumer sphere had declined by 7% since last year’s study.
Adware, however, dominated the consumer threat landscape, with Malwarebytes reporting nearly 17 million malicious advertising software detections in 2019, up 13% on the previous year.
The families most deployed were Adware.MindSpark, Adware.InstallCore, and Adware.SearchEncrypt – all are inexpensive and can be used alongside social engineering to steer users to a cyber scam.
“On the consumer side, cybercriminals have stepped back from ransomware and we see more attempts at infecting and spreading adware,” Adam Kujawa, director of Malwarebytes’ Labs, told The Daily Swig.
“And, in some cases, we’re still seeing bitcoin miners, with consumers turning into a commodity for cybercriminals.”
Whodunit
Kujawa said that the availability of open source intelligence was improving the tactics used by cybercriminals, often blurring the lines between attacks conducted by state-sponsored groups and independent threat actors.
This is demonstrated by the targeted attacks on businesses, as opposed to the former “wide net” approach of a cybercriminal sending out phishing emails to an address book en masse, Kujawa said.
“Intelligence collection on the target and trying to gain access is a kind of effort that has, historically, been out of the realm for the regular cybercriminal because of the time and resources,” Kujawa said.
“But over the last year and half we’ve seen plenty of opportunities where this method of attack and intent of operation focus has proven to be valuable and lucrative for the criminals.”
And now for something completely different
New ransomware families also shot up in 2019, attacking critical networks and hogging the spotlight in the major cyber-attacks of last year.
Ryuk and Travelex offender Sodinokibi, in particular, were highlighted in the Malwarebytes report, with detections increasing by 543% and 820% against business endpoints.
Although malware designed for Windows machines does not typically work on the Mac platform, detections on macOS devices increased by more than 400% in 2019.
“Mac users are encountering more garbage than a Windows user would,” Kujawa said.
The services sector, known for its distribution of third-party systems, was the top industry affected by cyber threats in 2019, Malwarebytes said, followed by education, retail, and manufacturing.
RELATED Business malware detections on the rise, report indicates






