Affected users notified via email

Video-sharing platform Dailymotion has suffered a credential stuffing attack, warning users that the incident is “ongoing”.
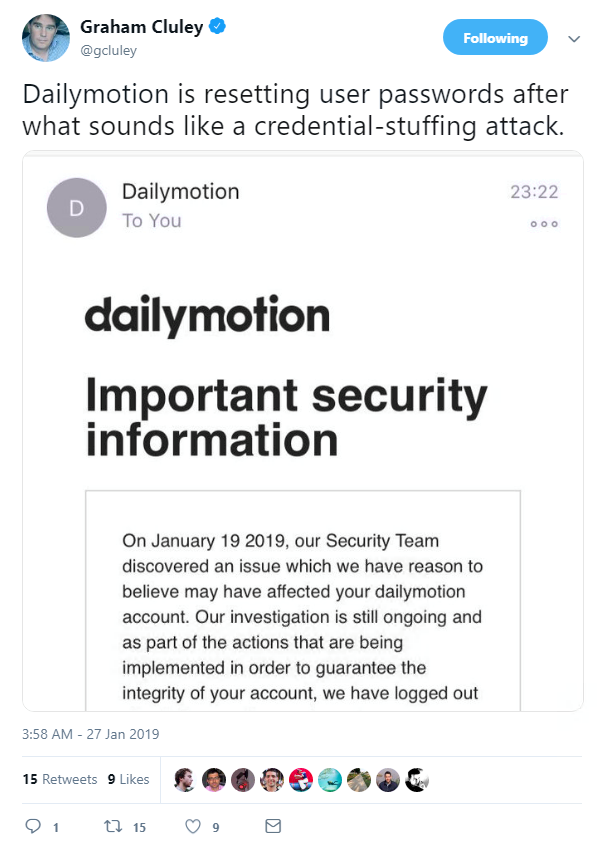
The website confirmed that the attack began on January 19 and is “still ongoing”. Hackers were able to access a limited (unspecified) number of accounts using leaked credentials from third-party breaches.
Dailymotion said its security team became aware and blocked all attempts by the hackers.
It also applied a force password reset on the accounts of targeted users.
A press release read: “Potentially impacted users have been contacted directly by dailymotion (sic) to inform them and provide them with personalized support. The CNIL (French Data Protection Authority) has also been notified of the attack.
“The attack consists in ‘guessing’ the passwords of some dailymotion accounts by automatically trying a large number of combinations, or by using passwords that have been previously stolen from web sites unrelated to dailymotion.
“The dailymotion teams are actively working to end the attack and reinforce the protection of its user data.”
Security expert Graham Cluley posted a screenshot of an email sent by Dailymotion to victims.
Credential stuffing is when hackers take previously-breached combinations of usernames and passwords from other sites, and use them to log in to different websites.
These credentials can be sourced from security breaches, providing login credentials are either directly exposed or can be brute forced from leaked password hashes.
Leaked password hashes can be broken by brute-force using lookup tables but only in cases where sites fail to use up to date hashing algorithms and salting.






