Tor users are being duped by doppelgänger domains
Cybercrooks may be making a small fortune by typosquatting .onion domains and scamming dark net market users.
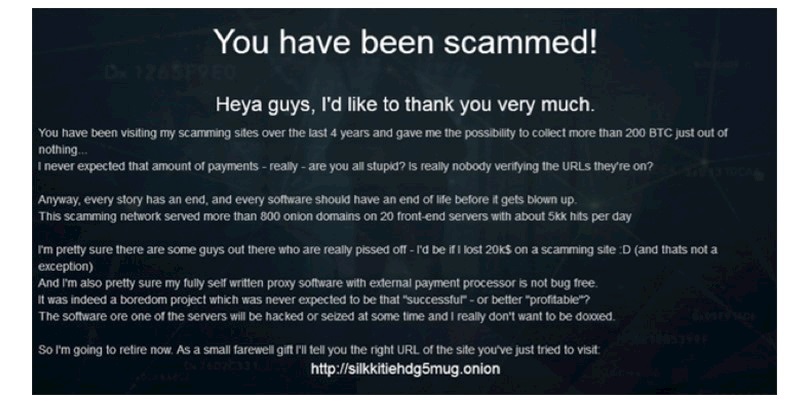
One group of cybercriminals boasted that they were retiring from the practice after making 200 BTC ($760,000) over four years from Tor-based typosquatting.
Although claims made by criminals should always be viewed with skepticism, threat intel firm Digital Shadows reckons that the 800 domains the fraudsters claimed to have in their network is plausible, based on the frequency of the appearance of a sign-off note from the scammers on confirmed typosquatted domains.
That’s Shallot
Creating a typosquat domain for a clear web site is fairly straightforward: Miscreants use a variety of techniques, ranging from using similar looking characters – such as a lowercase ‘L’ to replace a capital ‘i’ – or registering domains with Punycode characters that, when rendered in a browser, look similar to the Latin alphabet.
However, it’s much more difficult to create a typosquat lookalike version of a dark web site, due to the process of creating a .onion domain.
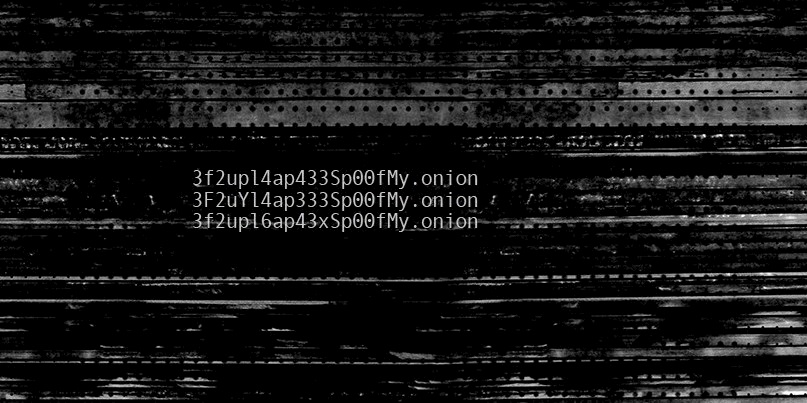
Onion addresses are generally long strings (between 16 and 56 characters) featuring numbers and letters – resembling something closer to a hash value rather than a regular surface web address.
While these domains are derived from the private key that’s generated when creating the service, tools such as Shallot allow attackers to generate multiple private keys over and over again, in an attempt to match a specific .onion domain output.
For example, if someone wanted a .onion domain to include the word ‘test’, Shallot would generate many different private keys until the associated domain includes ‘test’ at the beginning of the string.
The length of time taken to generate a matching key is dependent on how many characters a user is seeking to match in the resulting domain.
The technique opens the door to brand impersonation and domain squatting on the dark web.
Crouching tiger, hidden fraudster
Researchers at Digital Shadows have repeatedly stumbled across typosquat domains on the dark web while using the company’s Shadow Search investigation tool.
The threat of typosquat domains is significantly higher for criminal markets on the dark web, in particular, because .onion domains for these sites are intentionally complex and complicated. They’re called “hidden services” for a reason.
For example, a legitimate domain for the Tochka/Point Marketplace – tochka3evlj3sxdv.onion – had a doppelgänger typosquat domain at tochka3evevasc32.onion.
This is far from an isolated example. Digital Shadows reports that dark web hidden services like AlphaBay, Hidden Answers, Valhalla, Grams, Hansa Market, and several others have all been the target of typosquatting at one time or another.
Content on the dark web is volatile (sites go up and down all the time) while some sections are gated or apply access controls.
Several directory sites for hidden services exist which attempt to collect the various domains for these services, but these lists might easily be contaminated with illegitimate links (like typosquats).
“Scammers can monetize their typosquat domains in a variety of ways including advertising through web traffic driven to the site, harvesting credentials to sell or reuse in other fraud attacks, or directly from purchases made on these sites with no actual product being delivered,” according to Digital Shadows.
“Additionally, we’ve observed some of the sites using their own bitcoin wallets to accept donations for providing the service – a common practice for dark web sites.”
“Though we cannot confirm that the scammer operating this typosquat network was able to get the amount of Bitcoin that they claim, they mention utilizing a self-made payment processor on the sites, indicating that some form of purchasing was occurring,” it adds.
A blog post by Digital Shadows’ Harrison Van Riper covering typosquatting on Tor, along with the extent of the phenomenon on the surface web and the need for brands to monitor for typosquats, explains the issue in greater depth.






