Top infosec trends in the social media spotlight this week

The chief executive of Supermicro this week came forward with details of an independent investigation into claims that malicious chips were being added to its motherboards.
The result? According to CEO Charles Liang, there was “absolutely no evidence” of these chips on any of the manufacturer’s products.
It’s now been more than two months since Bloomberg Businessweek published its explosive report accusing the Chinese government of sneaking hardware-based spyware components onto Supermicro-made motherboards.
Yet despite continued calls for the news outlet to present concrete evidence to support its claims, the publication has thus far failed to deliver.
This latest investigation adds further weight to the repeated denials made by Supermicro, along with high-profile customers including Amazon and Apple.
And while some Bloomberg boardroom executives might be hoping for this whole episode to be quietly swept under the rug, it’s clear that the security community won’t be dropping the matter any time soon:
From software supply chain attacks to technical post-mortems, the US House of Representatives Committee on Oversight and Government Reform this week released a report based on its 14-month investigation into the Equifax breach.
Following a review of more than 120,000 pages of documents and interviews with former Equifax employees, the 100-page report (PDF) slammed the credit rating agency for its failure to implement adequate security measurements ahead of the breach.
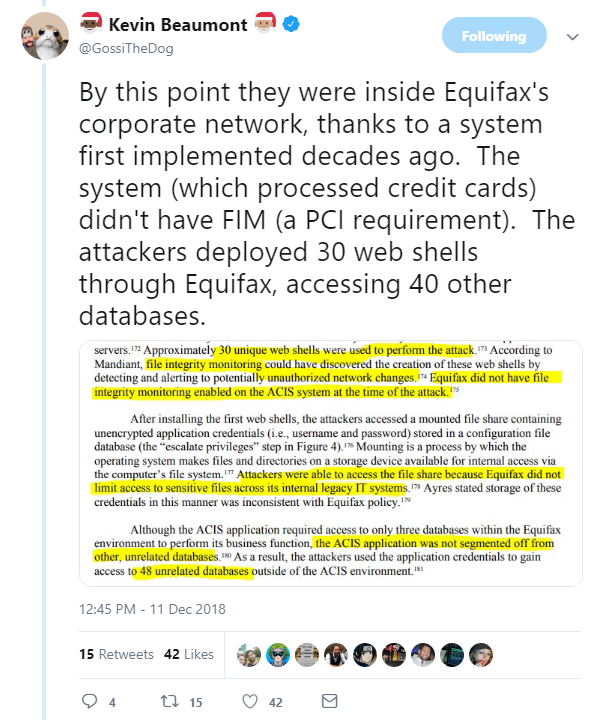
Digging into the report, security specialist Kevin Beaumont picked out some of the more interesting technical tidbits that highlight the many shortcomings in Equifax’s handling of an Apache Struts vulnerability, which was eventually exploited by attackers.
Elsewhere, a discussion heated up on the Netsec subreddit this week, following the news that Certificate Authorities (CAs) might not be as secure as previously thought.
As reported in The Daily Swig, a team of security researchers including Elias Heftrig recently discovered that five out of 17 CAs were susceptible to IP fragmentation attacks.
“The attack exploits DNS Cache Poisoning and tricks the CA into issuing fraudulent certificates for domains the attacker does not legitimately own – namely certificates binding the attacker’s public key to a victim domain,” the researchers explained during this year’s Black Hat Europe.
And finally, it seems British policymakers are intent on dragging the NHS into the 21st century, after it was announced that the country’s healthcare IT staff will be banned from purchasing any more fax machines from next month.
According to the BBC, some 9,000 fax machines were still in use across NHS facilities in England this summer, prompting serious questions surrounding the security of sensitive documents being sent with this outdated tech.
“We constantly receive faxes meant for other places in error, but this is never reported,” Rebecca McIntyre, a cognitive behavioral therapist from Manchester, told the BBC.