Malicious servers churned out error messages directing users to backdoored downloads

UPDATED At the height of the Electrum Bitcoin Wallet malware campaign, more than 70% of the entire network was being controlled by attackers, new research reveals.
The Electrum project hit the headlines in December, as reports surfaced on social media of a large-scale hack impacting users of the open source crypto-wallet.
It was subsequently confirmed that Electrum client versions 3.3.3 and earlier were vulnerable to an attack in which malicious servers were leveraged to throw up an error message to users making a bitcoin transaction.
These pop-ups would direct the wallet holder to deceptive sites that offered seemingly legitimate Electrum client upgrades.
However, the binaries in these downloads contained a backdoor that was used to siphon more than 200 BTC – $750,000 at today’s rate – from users’ accounts.
Dominant position
Nearly two months after the campaign first came to light, Coinbase blockchain security engineer Peter Kacherginsky has offered fresh insight into the attack against Electrum, and how criminals were able to exploit the network’s trust model in order to flood it with malicious servers.
In a blog post earlier this week, Kacherginsky discussed how attackers had modified the open source ElectrumX server software to throw up arbitrary error messages, which directed users to the malicious download pages.
“The ElectrumX servers form their own distributed network to increase resiliency to individual nodes going offline or falling behind the blockchain,” he explained.
“As Electrum Wallet discovers new servers and their peers, they are added to the local storage, and depending on a user configuration may be used the next time the client connects to the network.”
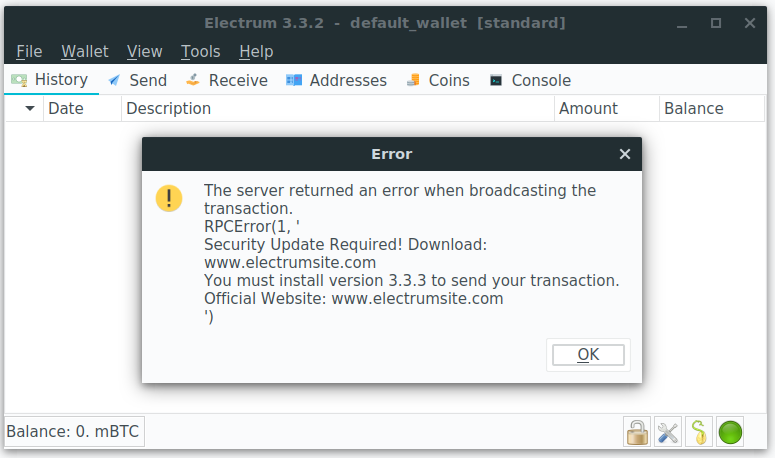
Screenshot of the Electrum transaction ‘error message’ used in the malware campaign
According to Kacherginsky, a user’s Electrum wallet attempts to maintain connections to a randomized selection of discovered servers. In order for the pop-up dialog box to be triggered, he said, the wallet would have to discover and connect to a malicious ElectrumX server.
“The more malicious ElectrumX servers in the network, the higher the chance that a wallet will be attacked,” said Kacherginsky, who went on to explain how attackers were able to skew the odds of a successful connection in their favor.
“Using randomly generated subdomains as aliases to a single domain is a clever exploit of ElectrumX’s peer verification process, which simply verifies that the advertised hostname resolves to the originating IP address,” he said.
“As a result, it is possible to flood peer tables with these ghost servers to perform a Sybil attack, where an attacker attempts to fill the network with servers they control to increase their chances to connect with Electrum clients.”
After having mapped the Electrum network during the attack, Kacherginsky paints a bleak picture of the compromised network.
“Based on the automated scanning for phishing messages, I observed more than 471 confirmed malicious servers out of a total of 657 active nodes,” he said. “That’s a staggering 71% of the entire scanned network being controlled by attackers.”
Following the publication of this article, Electrum founder Thomas Voegtlin called this data into question.
“The reported number of 71% does not really make sense,” he told The Daily Swig. “The attackers used thousands of names, but they were not active simultaneously.
“Moreover, that number suggests a 71% chance of connecting to a phishing server, which is inaccurate, because these servers were not seed servers. Traffic is not distributed uniformly across servers.”
Active steps to recovery
In his analysis, Kacherginsky made a distinction between two separate threat groups that were said to be targeting ElectumX servers.
One of the groups has apparently discontinued its campaign, but the researcher told The Daily Swig that the actors behind Campaign #1 are “alive, well, and highly professional at maintaining their infrastructure”.
“They keep on updating their phishing sites (as I auto-report them) and malware samples (when a new wallet release comes out),” he said.
While Kacherginsky noted that the Electrum development team have taken “active steps” to defend the network, he said it was clear that it is “under a persistent attack from one of more determined actors”.
“Remaining vigilant and downloading software only from trusted sources will remain the best advice for users of Electrum Wallet,” he said.
On the developer side, Electrum client versions 3.3.3 and above include mitigations against the attack. A new version of the ElectrumX server software has also been launched, which blacklists malicious servers.
“The real challenge for us is not to fix the wallet, but to have users upgrade their software, and to protect those who have not upgraded.” Voegtlin told The Daily Swig.
“Electrum does not have an automated update, therefore users need to actively install the update (and that is how it should be; automated updates would put us in a position where we have the power to steal users funds, which nobody wants).”
Unfortunately, users running Electrum versions earlier than 3.3.3 are still vulnerable to the pop-up scam. One GitHub user claimed they had lost funds via this method as recently as 13 days ago.
Interestingly, in order to reach users who are yet to upgrade, Electrum has deployed a “white hat attack” that uses the same vulnerability and directs them to the correct download page.
“The incentive for the Sybil attack will go away once the vast majority of users have upgraded their software,” said Voegtlin. “So we hope that the current blacklisting will only be temporary.”
This article has been updated to include comments from Thomas Voegtlin at Electrum.






