The implications of ‘Raccoon’ are dangerous, but the real-world threat is minor

Security researchers have released details of a new attack on the TLS protocol that could, under certain conditions, break its encryption and expose web users’ sensitive documents.
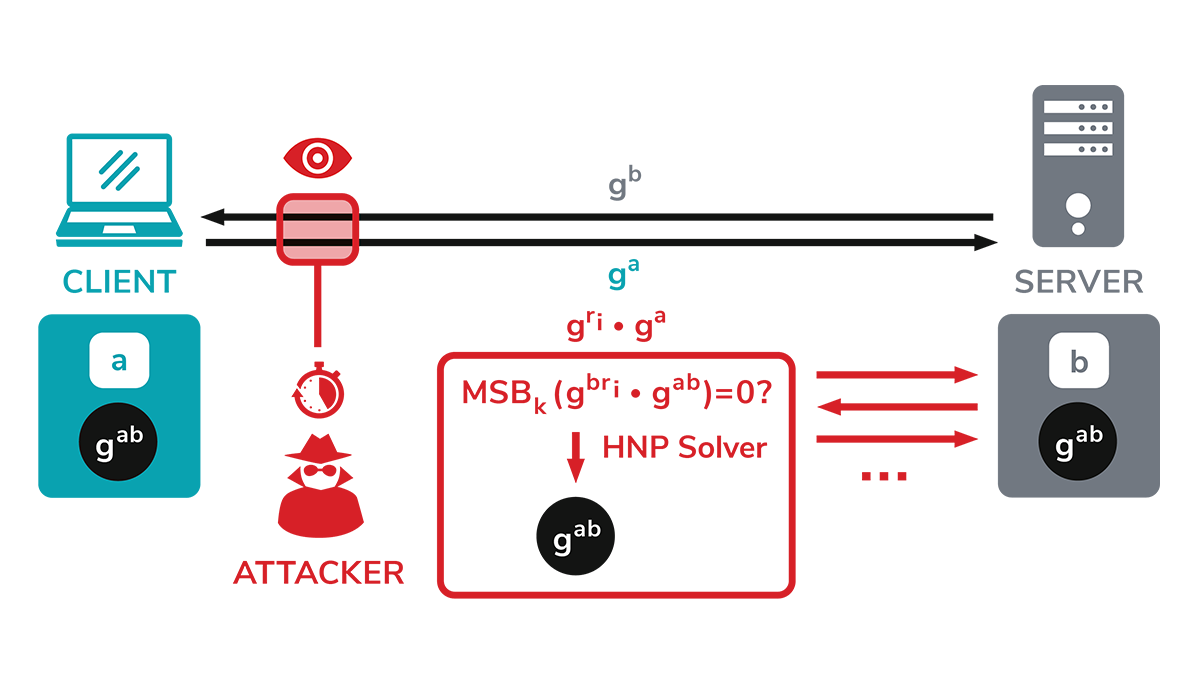
The attack, dubbed ‘Raccoon’, targets the Diffie-Hellman (DH) key exchange, a popular method for exchanging cryptographic keys in TLS connections.
By performing a timing attack on DH, the attacker can recover certain bytes of information, which can enable them to solve the Hidden Number Problem to decrypt the original premaster secret established between the client and server.
The implications of this attack are dangerous: by breaking the encryption TLS provides, a miscreant could access sensitive documents including emails, stored credit card numbers, and more.
Raccoon was discovered (PDF) by a team from Ruhr University Bochum, Germany; the Department of Electrical Engineering in Tel Aviv, Israel; Paderborn University, Germany; and BSI, Germany.
Far from easy
The researchers stressed that although the exploit could have far-reaching implications, the server-side attack could only be carried out in a rare set of circumstances.
There are a number of prerequisites for Raccoon to be successful, a technical blog post reads. These include the server reusing public DH keys in the TLS handshake – which is generally considered bad practice – and whether the attacker can execute precise timing measurements.
Robert Merget of Ruhr University Bochum, told The Daily Swig: “The attack is hard to pull off in two ways. First off, the attack requires that a connection is established using a vulnerable cipher suite.
YOU MAY LIKE TLS certificate lifespan cut short: A win for security, or cause for chaos?
“From an attacker’s point of view, there is not much an attacker can do about that. A study (PDF) in 2018 showed that the cipher suite chosen in a real connection is very often not vulnerable.”
Additionally, Merget noted that the attack requires that the server reuses public keys.
“There is also not much the attacker can do about that,” he said. “The only thing the attacker can influence is the measurements, the noise reduction in the measurements, and their ability to solve the HNP equations.”
 The attack can be executed in rare circumstances, say researchers
The attack can be executed in rare circumstances, say researchers
To patch, or not to patch?
Merget did advise anyone running servers that do reuse DH public keys to patch or reconfigure them, however the attack is not considered to be high risk to the general public.
He added: “A real-world attacker could bring the complexity of the attack down by performing it in a co-located cloud setup, where the attacker can use more advanced techniques like cache-side channels to get more reliable feedback.
“From our side, we will not perform further research in that direction as we are satisfied with our demonstration.”






