Scripts exploiting browser login managers found on 1,100 websites

Digital ad targeters are exploiting an 11-year-old vulnerability in web browsers’ built-in password managers to track users’ online behavior.
New research coming from Princeton University’s Center for Information Technology Policy shows how third-party scripts in web ads are being used to track users, even after they clear their cookies, switch devices, or use private browsing mode.
The below image illustrates the exploit, which begins when a user fills out a login form on a page and asks the browser to save the details. After navigating to another page on the same website, the tracking script inserts an invisible login form, which is autofilled by the browser’s password manager.
The third-party script then retrieves the user’s email address by reading the populated form and sends the email hashes to third-party servers.
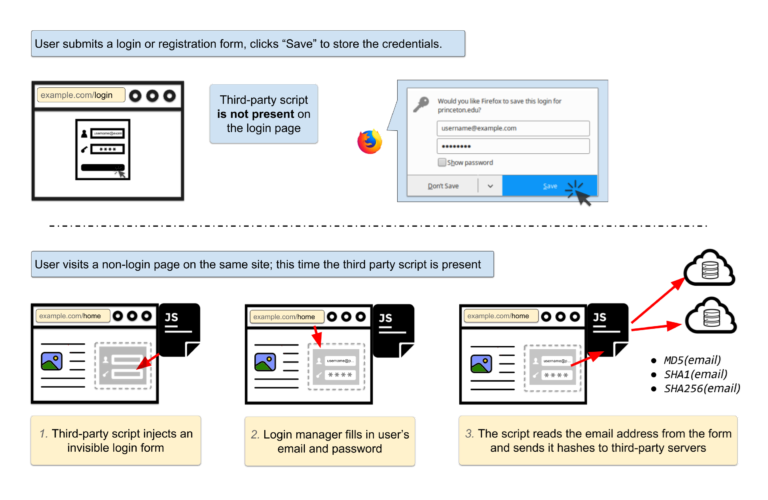
While the Princeton researchers found no evidence of actual password theft, they said the exfiltration of “unique and persistent” email hashes allow third parties to covertly build detailed user heatmaps and “connect the pieces of an online profile scattered across different browsers, devices, and mobile apps”.
Big Data
Although attacks of this nature have been discussed for at least 11 years, password manager scripts such as Adthink and OnAudience are fairly new to the scene, as marketers scramble to gain an edge over their competitors by building increasingly detailed user profiles.
Regardless, in their large-scale study of 50,000 sites, the researchers found third-party password manager scripts to be present on 1,100 of the Alexa top one million properties.
While publishers can take steps to prevent autofill data exfiltration by isolating login forms on a separate subdomain or implementing frameworks such as Safeframe, consumers shouldn’t hold their breath, as these methods require additional engineering.
For now, at least, it seems the best form of defense against invasive third-party scripts is to install ad blockers or tracking protection extensions.
“Browser vendors should reconsider allowing stealthy access to autofilled login forms in the light of our findings,” the researchers concluded. “More generally, for every browser feature, browser developers and standard bodies should consider how it might be abused by untrustworthy third-party scripts.”






