Why did billion-dollar affiliate operation shut up shop?
ANALYSIS Earlier this month, the developers of the GandCrab ransomware family announced that they were voluntarily rolling back their malware campaign and heading into retirement.
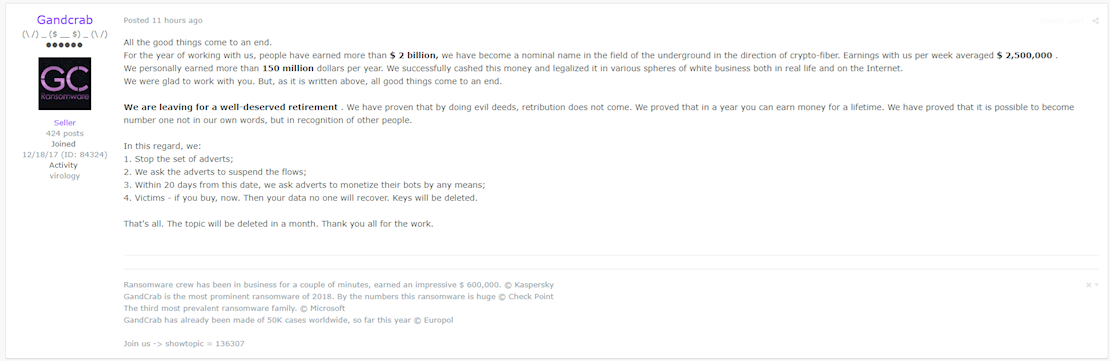
Posting on an underground web forum, the crew said the notorious ransomware-as-a-service (RaaS) operation had generated more than $2 billion in extortion payments for affiliates.
“We personally earned more than 150 million dollars per year,” the post claims. “We successfully cashed this money and legalized it in various spheres of white business both in real life and on the Internet.”
The developers’ attempts to big-up their nefarious exploits is far from an empty boast.
GandCrab exploded onto the ransomware scene in January last year, grabbing the attention of global cybersecurity firms and law enforcement alike. Within two months, more than 50,000 devices had reportedly been infected.
However, contrary to the malware authors’ claims that they were leaving the ransomware sector for a “well-deserved retirement”, a subsequent statement from Europol suggests that external forces played a role in the closure of the operation:
[J]oint efforts have weakened the operators’ position on the market and have led to the demise and shutdown of the operation by law enforcement. This shutdown was a global law enforcement effort supported by Bitdefender and McAfee.
In an emailed response to questions from The Daily Swig this week, a Europol spokesperson declined to explain the conflict between the agency’s statements and those of the GandCrab authors.
However, in a case study presented during the FIRST annual conference this week, Tamas Boczan, senior threat analyst at cybersecurity firm VMRay, provided fresh insight into GandCrab, and suggested that the developers’ involvement in an escalating cat-and-mouse game with security defenders played a key role in the campaign’s demise.
 Tamas Boczan presenting at the FIRST conference this week
Tamas Boczan presenting at the FIRST conference this week
“They implemented a classic ransomware-as-a-service model,” Boczan explained. “This is when the developers of the malware sell it to affiliates, and they share the revenue. In this case about 40% of the profits go to developers, and the affiliates keep the rest.
“In return for 40%, the affiliates get a binary of the malware, and they get access to a web panel, where they get to see information about the victims and have limited control of the malware. This is mainly for adding discounts or creating support for victims who don’t know how to buy cryptocurrency.”
Although GandCrab started out as a relatively simple ransomware variant (with basic encryption functionality and limited data collection capabilities), it still caused enough damage to attract the attention of Europol and security outfits around the world.
It was not long until the first set of decryption tools were released for GandCrab, and this led to a series of back-and-forth actions between the malware authors and Europol’s No More Ransom project.
Fresh decryption tools were swatted away with new and improved ransomware versions, prompting the development of revamped decryption utilities, and so forth.
Reputation is everything
Boczan noted that the GandCrab authors were extremely agile – sometimes pushing out new ransomware versions in a matter of hours. (They also dipped their toe into exploit development, publishing a zero-day against a security tool as part of an antivirus smear campaign.)
However, in the underground marketplace, reputation is everything. And according to Boczan, the continued efforts of Europol and cybersecurity companies served to tarnish the GandCrab name. Affiliates lost trust in the ransomware as an easy way to make a dishonest buck.
“[Decryption keys] are a really effective way to fight ransomware because it makes the ransomware authors lose money,” he told FIRST conference delegates this week.
“If a victim can decrypt the ransom files for free, they obviously won’t pay the ransom. More importantly, it makes the malware authors lose their reputation, and since their whole operation is based around having a good reputation on the forum where they sell the ransomware, if their reputation takes a hit then their operation also takes a hit.”
Boczan added: “This is ultimately what led to the end of the malware. They said that they were retiring because they made so much money that they just don’t need it anymore, but Europol [said] that the malware operation was shut down with the joint efforts of nine law enforcement agencies and two antivirus companies.”
Power vacuum
While Boczan said he expects GandCrab authors to remain true to their word and abandon this particular campaign, he also said there is “probably a new one coming soon”.
In the meantime, rival ransomware developers are likely to be vying for market position.
“[GandCrab’s] disappearance will create a power vacuum,” Boczan said. “This is what happened before GandCrab, which entered [following] the disappearance of the Cerber ransomware two years ago.”
Moreover, in anticipation of a possible return of the GandCrab crew – albeit under a different brand name – any newcomers to the ransomware scene will face added scrutiny from malware analysts around the world.
“Based on what we learned about the [GandCrab] operation, we can set upper and lower bounds to their capabilities,” the analyst said.
“The most important thing that we learned about them is that for the operation to operate successfully, you need a good reputation. Destroying this reputation is what slowly killed the operation, and this was accomplished by decryptors,” he concluded.