Google’s elite security team looks for new ways to predict cyber-attackers’ behavior

The best way to combat the exploitation of zero-day vulnerabilities is by predicting attackers’ movements, Google’s Project Zero technical lead told delegates at the FIRST Organization’s annual conference yesterday.
Presenting at the event, which was held online this year, Project Zero technical lead Ben Hawkes revealed that Google’s elite bug-hunting team is looking to build a “crystal ball” for forecasting miscreants’ behavior based on expert forecasts from cybersecurity professionals.
Project Zero is Google’s in-house research team responsible for tracking zero-day bugs and coordinating fixes with vendors.
In the six years since its inception, Project Zero has discovered 1,800 zero-day vulnerabilities according to Hawkes, reporting an average of five to six bugs per week.
90-day disclosure standard
Hawkes told FIRST conference attendees during his keynote speech that the methodology behind Project Zero’s coordinated disclosure timeline has been “scrutinized” over the past few years.
“You might say critiqued,” he said.
The team currently works to a 90-day disclosure deadline, meaning that vendors have just under three months to apply the necessary fixes before the issue is made public.
The Google Project Zero team initially worked with vendors on a coordinated disclosure basis, however the results “weren’t fantastic”, Hawkes admitted, with patches sometimes taking up to six months to be released.
Read more of the latest Google security news
A 90-day disclosure timeline was therefore enforced, which Hawkes said the team is “pretty happy with”.
He explained: “We’ve gone from a world where just a small proportion of our bugs are fixed [within] the 90 days to a world where 98% or thereabouts of our discoveries are now fixed within the disclosure deadline.”
The cybersecurity industry has largely warmed to the 90-day vulnerability disclosure timeline, and many would argue that this has become something of industry standard.
However, as Hawkes noted, the journey to implementing this on a large scale has been decades in the making.
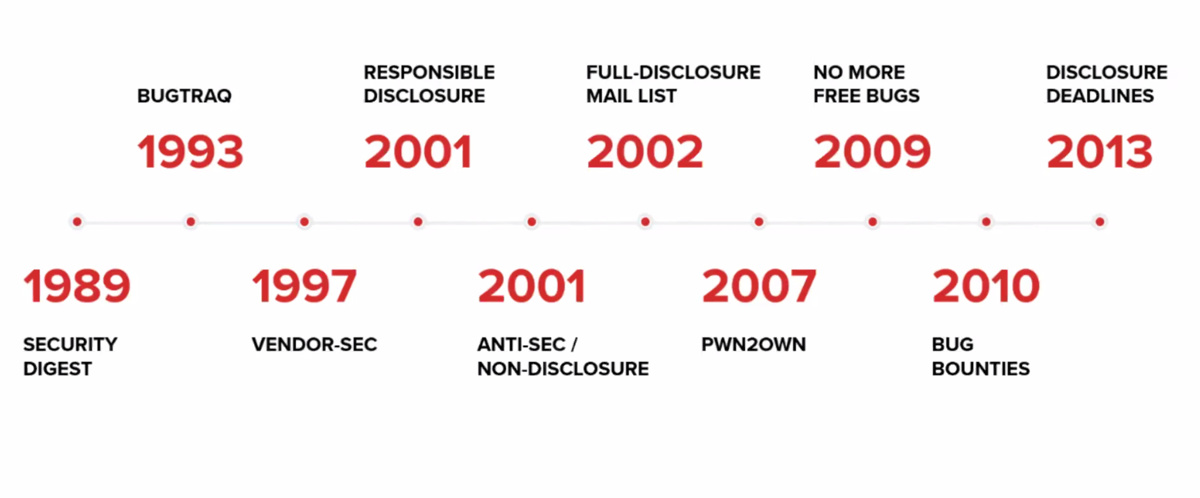 A timeline shows the evolution of vulnerability disclosure since 1989
A timeline shows the evolution of vulnerability disclosure since 1989
Hawkes presented a timeline (above) showing the various policies related to vulnerability reporting over the years – from the 1989 Zidar Security Digest mailing list, to the introduction of bug bounties and coordinated disclosure guidelines.
“It’s a long, winding path to where we’re at today and throughout all of this time we have debated back and forth about which disclosure process was the best.”
Predicting attackers’ behavior
While Hawkes noted that the debate surrounding the best vulnerability disclosure method may not come to an end any time soon, he moved on to discuss an issue that’s arguably even more important: how to predict attackers’ next move.
“We need to build a model for attacker behavior,” he urged.
“That means building some sort of description of the different classes of attack [and] of the different types of attacker that are active at any given moment.
RELATED Microsoft unveils plans for Project Zero-style Chromium research program
“And so that means estimating their overall resources… understanding how the attacker prioritizes their work, their level of risk tolerance, where their funding comes from, their ability to do in-house research and development versus having to outsource a lot of the technical work, and so on.
“And it means doing all of this with a global perspective.”
Projection Zero?
Hawkes pointed to a 2019 Medium blog post by security researcher Ryan McGeehan, in which he details a study undertaken to forecast future cyber-attacks.
McGeehan asked a panel of cybersecurity experts to predict whether the high profile Bluekeep vulnerability would be exploited in the wild. The researcher then tracked the panel’s responses to determine whether or not they were accurate.
While the forecast wasn’t expected to be successful, by predicting an attacker’s moves defense teams can “unify” their understanding of the behavior of miscreants and, in turn, improve the disclosure debate, according to Hawkes.
Therefore, Project Zero is looking to “scale up” this study by creating a panel of experts focused on predicting how malicious actors will respond to the shifting vulnerability landscape.
“This is a new goal we have, and something that we’re exploring at Project Zero and looking at funding, but the pandemic has slowed this down a little bit.
RESEARCH Cybercrime isn’t the exciting career it’s cracked up to be, say academics
“But I’m happy to say that the initial interest is very high and we’re hoping to have something up and running next year,” Hawkes revealed.
“What we want to build is a crystal ball for vulnerability disclosure, and that’s [through] the expert panel based qualitative forecasting.
“So, we’re going to ask questions like, ‘Will this proof of concept be observed in active attacks in the next month? Will these vulnerability details released today be turned into an exploit in the next week? Will a zero-day vulnerability in a certain product be found in active exploitation in the wild in the next quarter?’”
“We fully expect to get these predictions wrong a lot as a panel, [but] by asking these questions, we’re aiming to unify our understanding of attacker behavior, and by doing so we’re aiming to improve the disclosure debate.”
To find out more about the forecast panel and how to get involved, contact Project Zero.
READ MORE Project Zero relaxes 90-day vulnerability disclosure deadline to boost patch adoption






