Password protection survey shows every little helps

Even basic steps in improving online account security can go a long way towards thwarting hijacking attacks, according to new research from Google.
Using physical security keys is considered best practice but even basic forms of two-factor authentication (2FA) work against everyday phishing attacks.
Google found that simply adding a recovery phone number to your Google Account and turning on 2FA can block up to 100% of automated bots, 99% of bulk phishing attacks, and around 76% of targeted attacks.
On-device prompts – a more secure replacement for SMS – helped prevent 100% of automated bots, 99% of bulk phishing attacks, and around 90% of targeted attacks, the same study found. The figures for successful hacks are approximate only because statistical caveats apply.
Weaker knowledge-based challenges, like asking users to give their last sign-in location, throw off bots but are almost useless against phishing attacks, only working 10% of the time.
“The same vulnerability exists for targeted attacks,” Google explains in a blog post. “That’s because phishing pages and targeted attackers can trick you into revealing any additional identifying information we might ask for.”
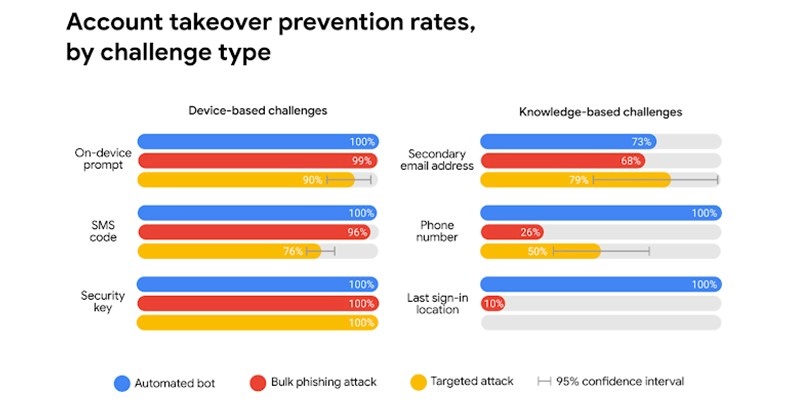
The figures come from a year-long study where Google teamed up with researchers from New York University and the University of California, San Diego. The findings were presented at The Web Conference last week.
Challenging users beyond asking for a password confers security benefits, but Google has decided not to mandate it because of usability and customer support drawbacks.
Even sending something to a secondary email address – more effective than simply asking for their last log-in location – can be problematic.
“Challenges introduce additional friction and increase the risk of account lockout,” Google’s Kurt Thomas and Angelika Moscicki write.
“In an experiment, 38% of users did not have access to their phone when challenged. Another 34% of users could not recall their secondary email address.”
Team Google investigated the emerging “hack for hire” criminal groups – those that offer to break into a single account for a $750 fee – in developing its figures.
Activists, journalists, political campaign teams, and the like who are targets of state-backed groups face an even bigger threat. Organizations like human rights charity Access Now provide cybersecurity advice in this arena while Google is also keen to do what it can to help.
Google continues to recommend that high-risk users enroll in its Advanced Protection Program and adopt security keys.
The Daily Swig recently reviewed the effectiveness of physical security keys, finding an immature market where support by browser makers and websites lags far behind the availability of the technology.
Even websites that support hardware tokens offer a fall back to less secure means of login in the absence of such tokens, a potential weakness that more determined and resourceful attackers might seek to exploit.
Google’s Advanced Protection Program locks down accounts and insists on the presence of pre-enrolled hardware key before letting users into accounts, a much more secure approach that has some convince and usability drawbacks that mean it isn’t suitable for everyone.
Google’s top tips offer further general advice on account security.






