DOM-based XSS and CORS protections among mooted changes
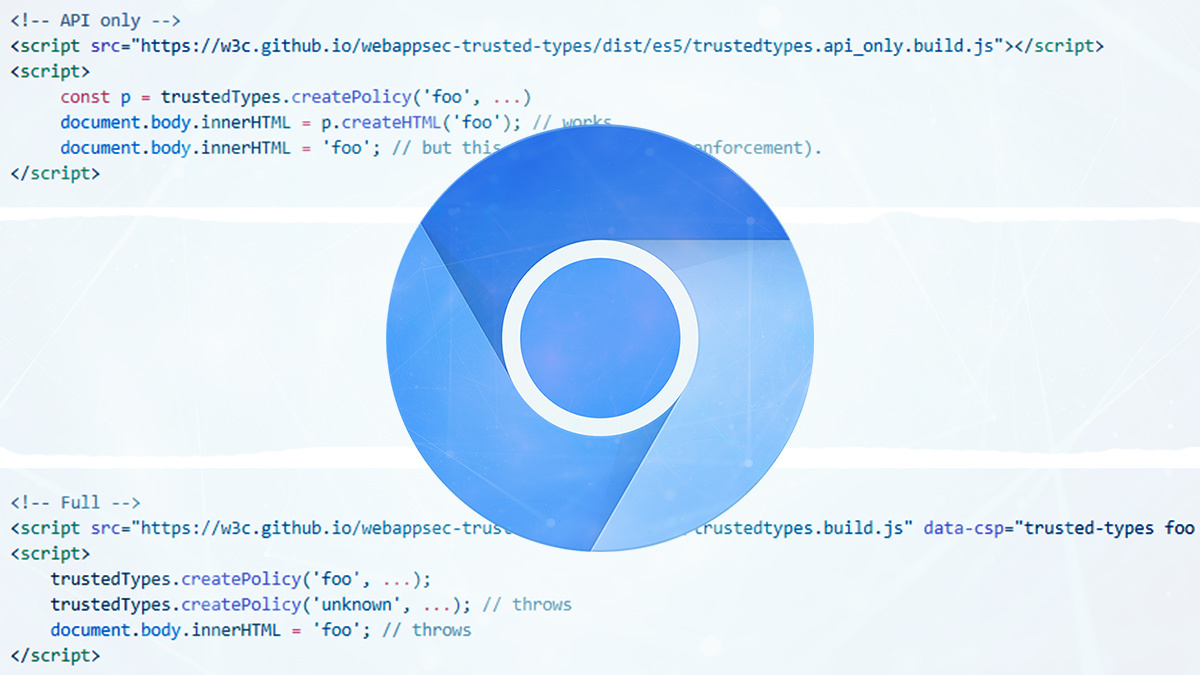
A new technology that secures “dangerous” web APIs against DOM-based cross-site scripting (DOM XSS) vulnerabilities is one of several new security features mooted for Chrome 83.
The forthcoming release of the popular web browser will also feature cross-origin resource sharing (CORS) safeguards that block side-channel attacks like Spectre, according to a post on the Chromium blog.
In Types we Trust
Currently in beta, Chrome 83 is due to land on users’ desktops from May 19, complete with the Trusted Types browser API.
Trusted Types is designed to foster the development of applications that are free of DOM XSS flaws, which are widespread and sometimes introduced unintentionally.
Google technical writer Joe Medley, who authored the post, said users could set a content security policy instructing Trusted Types to cause a script to generate an error if, say, Element.innerHTML – which can open sites to harmful HTML manipulation – was used.
Side-channel attacks, meanwhile, could be mitigated by putting sites into cross-origin isolated status using two HTTP headers: Cross-Origin-Embedder-Policy (COEP) and Cross-Origin-Opener-Policy (COOP).
Using COEP and COOP web pages can securely use privileged features like Performance.measureMemory() and JS Self-Profiling API and prevent modifications of document.domain.
Polished Chrome
Also planned for Chrome 83 is new functionality that will result in downloads in sandboxed iframes being blocked by default to restrict malicious or abusive downloads.
HTML form controls have, meanwhile, been revamped in collaboration with Edge to improve the appearance and function of HTML form controls.
Other features include a Barcode Detection API – available on devices with Google Play Services installed but not uncertified devices – that decodes image barcodes, thereby removing reliance on performance-sapping external libraries.
Google’s latest announcement may assuage fears that browser security is being neglected during the Covid-19 pandemic.
The outbreak has prompted the major browser players to put releases on hold, and delay plans to abandon support for TLS 1.0 and 1.1.
Google is rolling back Chrome SameSite cookie changes due to the coronavirus.
A scaled-down, delayed version of Chrome 81 landed last week, with two use-after-free bugs and an out-of-bounds read flaw in WebSQL among 32 vulnerabilities fixed.
However, the release schedule is now skipping Chrome 82 entirely due to coronavirus-related development pressures.
RELATED We want options: Google answers call for full URL presentation in Chrome






