Research gives fresh technical insight into stealth malware claimed to be targeting industrial control systems

December 23, 2015, marked a watershed moment for those tasked with securing critical infrastructure systems, as the first known successful cyber-attack on a power grid left some 230,000 Ukrainians without electricity for up to six hours.
This landmark attack was attributed to the advanced persistent threat (APT) group known as BlackEnergy, which gained a foothold in Ukraine’s energy infrastructure through spear-phishing emails loaded with malware.
Although the BlackEnergy blackout impacted just 0.5% of Ukraine’s population, it demonstrated the potential for hackers to wreak havoc on critical infrastructure, leaving many to wonder when – and where – the next attack would take place.
Strangely, however, following the Ukrainian power grid takedown, BlackEnergy went dark.
“That was the last known use of the BlackEnergy malware in the wild,” said European cybersecurity firm, ESET.
While the apparent disappearance of the hackers left security experts scratching their heads, Slovakia-based ESET recently published new research claiming to provide details of APT group’s successor.
“Around the time of that breakthrough incident, when around 230,000 people were [temporarily] left without electricity, we started detecting another malware framework and named it GreyEnergy,” the company said in a threat update.
“It has since been used to attack energy companies and other high-value targets in Ukraine and Poland for the past three years.”
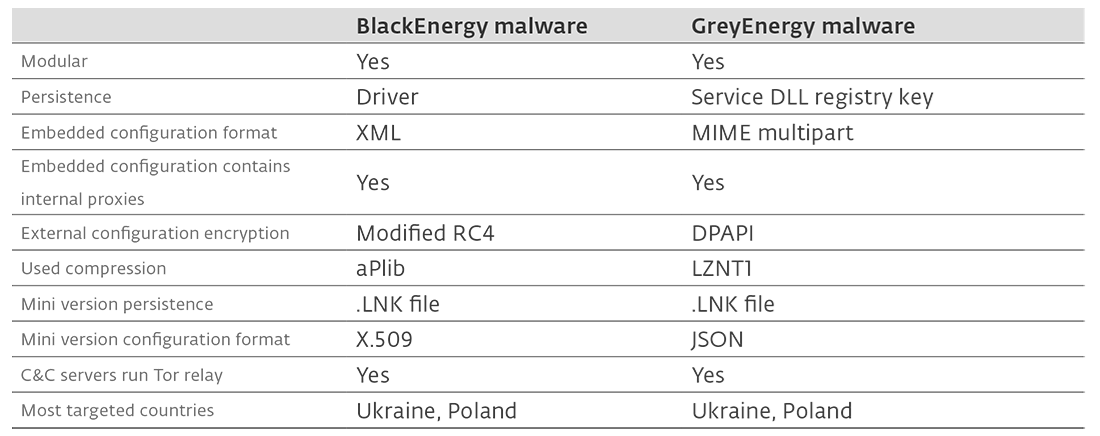
According to Anton Cherepanov, author of the GreyEnergy White Paper (PDF), the malware has been used in targeted attacks against critical infrastructure in central and eastern Europe, and exhibits “many conceptual similarities with BlackEnergy”.
Although security researchers have said there is not enough evidence to independently verify the claims that Grey is the new Black, new technical insight shows that those behind this new strain of malware are going to great lengths to mask their campaign.
Moreover, with attackers able to add new functionality to the malware at any time, is GreyEnergy the likely candidate for future cybersabotage operations against critical infrastructure?
From maldoc to backdoor
In November, Alessandro Di Pinto, researcher at Nozomi Networks, brought forward fresh technical analysis that acts as further confirmation that the malware’s architects are going to great lengths to smuggle GreyEnergy onto systems – and more importantly, to keep it hidden there.
“The GreyEnergy malware uses a common infection method: phishing emails with infected documents,” Di Pinto said. “However, the malware’s code is anything but common – it is well written and smartly put together and is designed to defeat detection by cybersecurity products.”
After reverse engineering the GreyEnergy maldoc, Di Pinto found that the attacker is using a packer to obfuscate the malicious code, in an attempt to avoid the pattern-based detection that forms a component of many cybersecurity products.
In addition, it was found that the malware features anti-forensic techniques, such as the wiping of memory strings, and also created a peer-to-peer network between infected systems.
This means that only a single node contacts the C&C remote server for updates, thus decreasing the possibility of raising security alerts.
“The guess is that the GreyEnergy authors were concerned about having several nodes connecting to the internet at the same time and decided to implement that solution to limit the number or nodes talking outside,” Di Pinto tells The Daily Swig.
GreyEnergy could also survive a system reboot, making it persistent on the target system.
Once installed, ESET said, the malware spies on compromised systems (taking screenshots, recording keystrokes, and lifting passwords). It also comes with built-in update functionality and the ability to run secondary malware.
Specifically targeting ICS?
According to ESET, the transition from BlackEnergy to GreyEnergy happened at the end of 2015.
And although the security firm said it hasn’t observed any modules that specifically target industrial control systems (ICS), the company said GreyEnergy operators have been “strategically targeting ICS control workstations running SCADA software and servers”.
“According to our research, the GreyEnergy actors deploy this backdoor mainly on two types of endpoints: servers with high uptime, and workstations used to control ICS environments,” Cherepanov said.
While both ESET and Nozomi’s research shines new light on a particularly stealthy and persistent malware campaign, Jake Williams, founder and president of Georgia-based cybersecurity firm Rendition Infosec, said there is insufficient data available to independently verify whether GreyEnergy is the successor to BlackEnergy, or indeed whether it’s explicitly targeting ICS.
“I ran a SANS cyber threat intelligence course the week the ESET report was released,” Williams told The Daily Swig.
“For the capstone exercise, I asked them to perform an ACH assessment of whether – based on available data, not ESET’s assessment – GreyEnergy was the obvious successor to BlackEnergy and whether it was designed to target ICS (like CrashOverride).
“Six individual teams reached the same conclusion: ESET does not provide enough data to independently validate their claims. While most believed ESET had sufficient data to make their claims, they concluded that ESET’s proprietary targeting data alone makes the ICS connection.”
Following his own analysis of the GreyEnergy maldoc, Di Pinto was also reticent when it came to explicitly defining GreyEnergy as ICS malware.
“During our analysis we didn’t find any specific ICS-related indicator,” he said. “Technically, it could be used in attacks against other sectors like finance or government.”
Despite this lack of evidence, however, the researcher said it’s possible that GreyEnergy could evolve to include modules capable of damaging critical infrastructure in the future.
“The threat actors behind GreyEnergy have tried to stay under the radar, focusing on espionage and reconnaissance, quite possibly in preparation of future cybersabotage attacks or laying the groundwork for an operation run by some other APT group,” Di Pinto said.
“The attacker can add new functionalities anytime and even after months since the malware has been installed. Once the first stage of the malware is installed inside a victim’s system, the threat actor is able to deploy new modules increasing the basic capabilities.
“A new version of the threat is probably under development, and understanding how the current version works could be really useful trying to protect proactively against new versions.
“The main purpose of our research was focused on understanding the techniques involved in the newest incidents in order to maximize our technical capabilities to defeat this kind of threats in the future.”
GreyEnergy protection
As organizations – and particularly ICS operators – await further insight, Di Pinto said enterprises can take numerous measures to mitigate the chance of a GreyEnergy infection.
“The most important action to take is to teach employees about the cyber threats and common techniques used by attackers to gain access to the systems,” he told The Daily Swig.
“In the scenario we covered, the main attack vector was a malicious Word document attached to a phishing email, so staff training would be enough to avoid the incident.
“It is also really important for technical staff to keep all the systems up-to-date with the latest security patches – especially if they are public-facing servers.”
ESET did not respond to our request for comment.






