More than half of 28 PDF readers tested were susceptible to newly discovered hacking technique – including Adobe Acrobat and Foxit Reader
Security shortcomings in the ‘interactive forms’ feature of the PDF file format allow attackers to add invisible, malicious content to documents, then reveal it after the signing process, academic researchers have discovered.
Of 28 PDF applications subjected to three distinct types of attack, 15 were vulnerable to at least one, including Adobe Acrobat and Foxit Reader, two of the most popular readers.
All three Shadow Attack exploits were mounted successfully against 11 applications, according to researchers from the University of Ruhr, in Bochum, Germany.
Manipulate any document
The attack is “very easy” to pull off, requiring just a text editor and knowledge of how PDFs work, Vladislav Mladenov, one of the researchers, told The Daily Swig.
If successful, attackers can manipulate any PDF document, such as a “contract, agreement, a permission slip, or a bank form”.
The potential dangers of this technique are even more pronounced as digitally-signed PDFs have become a widely accepted, legally enforceable substitute for traditional, written signatures in the US and Europe, as well as in certain Asian and South American countries.
Adobe Cloud processed eight billion digital signatures in 2019, while DocuSign handled 15 million documents a day.
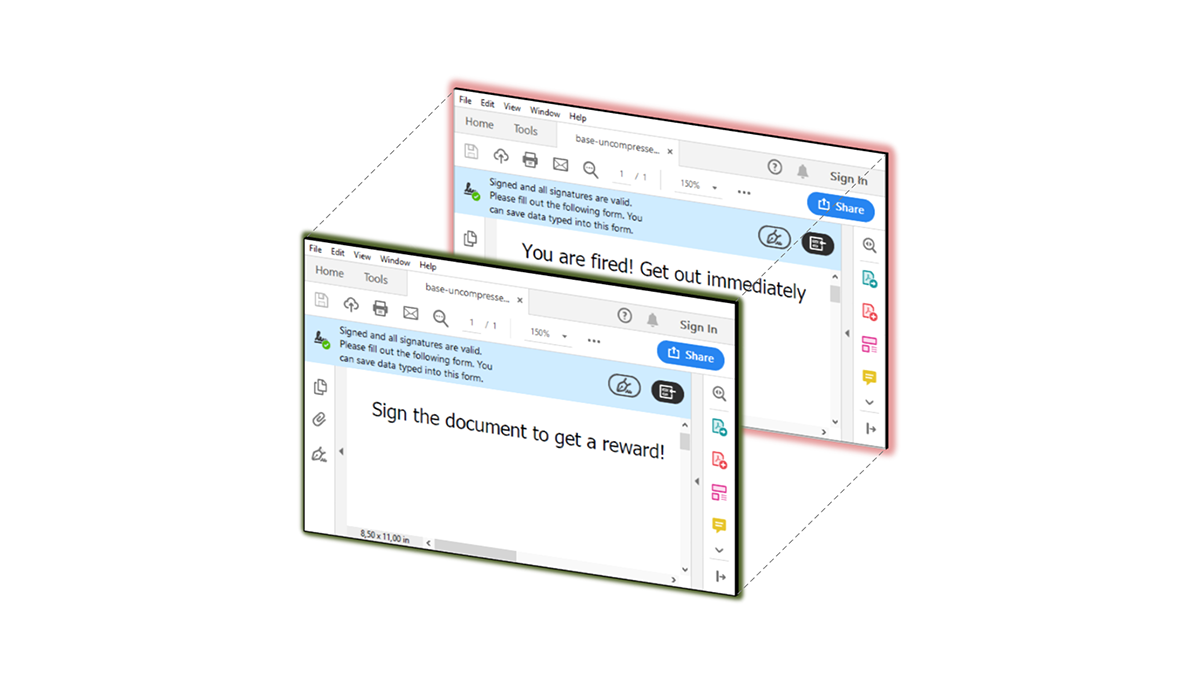 Attackers can make modifications to the document and change the visibility of the hidden content
Attackers can make modifications to the document and change the visibility of the hidden content
How Shadow Attacks work
Contracts or agreements are routinely prepared by one employee before being reviewed and signed by an authorized, more senior party or parties.
Attackers can exploit this process by first preparing a PDF document containing ‘invisible’ content.
When a person or cloud signing service reviews, signs, and returns the document to the attacker, they are then able to “make modifications to the document and change the visibility of the hidden content,” the researchers explain.
All of this is done without invalidating the digital signature or leaving any obvious evidence of manipulation.
When the victim receives the modified signed document, they “see different content than the signing entity”, but are none the wiser.
Hide and replace
The researchers describe three Shadow Attack techniques.
‘Hide’ attacks, conceal content from victims behind a visible layer. Attackers can then “manipulate the signed document in such a way that the picture is no longer rendered by the viewer application.”
This could be used to maliciously redirect a payment.
Secondly, ‘Replace’ attacks exploit the visual properties of text fields in interactive PDF documents in order to exchange form content.
Here, an attacker could manipulate a signed invoice or donation form to include their own bank account details.
Finally, ‘hide and replace’ attacks proved to be the “most powerful” of the three methods tested, since the document’s entire contents can be exchanged, including “text content, forms, fonts, and annotations”.
Are you vulnerable?
Most PDF reader vendors “closed the reported vulnerabilities promptly” with the help of the researchers and CERT-Bund, Germany’s Computer Emergency Response Team.
However, four vendors – eXPert PDF Reader, PDF Editor, PDFelement, and Perfect PDF – failed to respond to multiple contact attempts.
You can check whether your PDF reader is vulnerable to Shadow Attacks and update if necessary.
If your PDF viewer is not on the list, you can download the exploits used by the researchers and test it yourself.
A more detailed analysis of the flaws (CVE-2020-9592 and CVE-2020-9596) is available (PDF) on the Ruhr University website.
This isn’t the first time researchers have discovered security deficiencies in the PDF file format.
The Daily Swig revealed last year that researchers from the same university said they had broken the PDF encryption standard, and in 2018 detailed how flaws in Adobe Reader and Microsoft Windows could be exploited to plant malware on victims’ machines.
Researchers at Ruhr-University Bochum also demonstrated how to spoof PDF signatures in 2019.
RECOMMENDED Roundcube XSS vulnerability opens the door to email account takeover






