Inside the incident response to a MegaCortex attack
Cloud desktop and hosting provider iNSYNQ has offered a post-mortem on a ransomware attack that left accountants and small businesses temporarily unable to access accounting data and other files for several days last month.
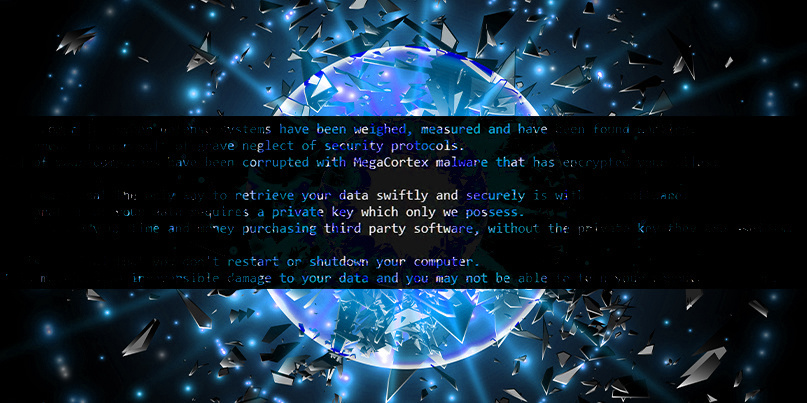
In a post-attack statement, published on August 12, around three-weeks after the malware struck, iNSYNQ said that it had been hit with a “previously unseen variant of the virus known as MegaCortex”.
It blamed the breach on a “targeted attack” by a cybercriminal group that had first infiltrated its systems a month before it “remotely triggered a highly-targeted, carefully planned ransomware attack on one of our primary data centers”.
The gang also hit backups even though these are kept on separate servers, pointing towards a deep penetration of iNSYNQ’s systems.
Citing the results of a preliminary investigation, iNSYNQ said it had “no evidence indicating that our customers’ data was exfiltrated (i.e. taken) or accessed as a result of this incident”.
iNSYNQ, a cloud hosting provider typically used to run either QuickBooks or Sage, goes on to justify its handling of the breach and explain why its backups were also affected by the assault.
“Our backups are on separate servers,” it said.
“The attackers targeted those servers that included backups in addition to the other servers. We had to turn all servers off when the attack occurred.
“While we were able to preserve the majority of our customers’ data and worked with Crowdstrike to ensure there was no lingering malware present, re-stabilizing systems proved to be an incredibly time-consuming process because of the need to rebuild thousands of customer’s desktops one by one,” it added.
iNSYNQ said that attackers demanded an unspecified payment after the attack. The company refused to pay, citing ethical reasons.
In addition to the incident response blog post, iNSYNQ also published a customer-orientated FAQ, offering answers to questions that came up during a recent webinar.
MegaCortex is a known ransomware strain associated with targeted attacks that rely on first breaking into networks and planting trojans (backdoors) and other network hacks and typically lying in wait for days or weeks before the main malware payload is triggered.
MegaCortex first surfaced in 2019. The gang behind the malware have upped the ante in recent weeks and are now demanding up to $5.8 million in ransom following a successful attack, according to Accenture.
Investigative reporter Brian Krebs adds that the attack on iNSYNQ began with a targeted phishing email.
This remains unconfirmed by iNSYNQ, which said it remains in the middle of an ongoing criminal investigation.
RELATED iNSYNQ begins cautious recovery from ransomware infection






