Top infosec trends in the media spotlight this week

Microsoft took center stage this week after confirming it had blocked attempts by Russian-linked hacking group Fancy Bear to launch cyber-attacks on US conservative organizations.
The software company seized six net domains mimicking Republican websites as part of a wider spear-phishing campaign.
Microsoft said the group, also known as APT28, tricked conservative voters into visiting the insecure websites and would then steal their login information.
Days later, the Democratic National Committee (DNC) contacted the FBI to claim it had been hacked by Fancy Bear, after evidence of intrusion into its voter database.
In a rather embarrassing episode though, the DNC was forced to backtrack on its claims, admitting that the ‘hack’ was actually an exercise performed by its own team of pen testers.
It turns out the pen test was organized by the Michigan Democratic Party, which failed to inform the DNC about it.
In other Microsoft news, end-to-end encryption was released for Skype this week in a further effort to enhance security.
Encryption is now enabled through the private conversation mode, available for desktop and mobile.
In other big-name news, Google was discovered to be tracking Google Maps users’ locations – even when they tell it not to.
The internet giant is facing a potential class action lawsuit after a report concluded that users’ locations are being stored despite the location history feature being turned off.
Google has been accused of falsely misrepresented what the term ‘history location off’ means, in a lawsuit filed in San Francisco this week.
Obviously this news sparked an influx of people telling each other to stop using Google Maps.
Others questioned what they expected, when the majority of smartphone users happily hand over their rights to privacy in return for an easier life.
T-Mobile confirmed that two million customers were affected in a hack on Monday, when malicious actors stole personal data from its systems.Details such as names, addresses, phone numbers, account numbers, and account types “may have been exposed”, the carrier said.
No financial information was stolen as a result of the incident.
T-Mobile confirmed that any customers thought to have been affected will be notified via text message.
It is thought that around 3% of T-Mobile’s 77 million customers have been affected.
But the sting felt by the phone company must be particularly painful considering a PR disaster earlier this year.
In April, a Twitter account belonging to T-Mobile Austria said that storing passwords in plaintext was fine because its security is “amazingly good”.
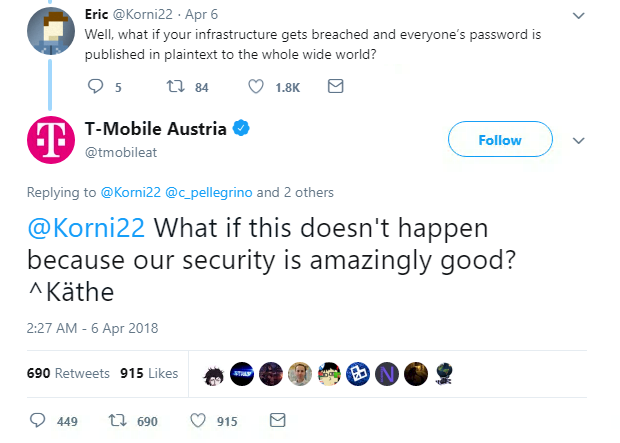
There’s no indication that the recent hack is due to a lack of security on T-Mobile’s part – but we really don’t need to tell you why passwords should never be stored in plaintext.
Finally, a hacker has demonstrated a pretty cool way of bypassing biometrics by recreating a fingerprint on a fake finger.
Wojciech Regula detailed how to clone a fingerprint to bypass TouchID on an iPhone, continuing the rhetoric that biometric passwords may not be as highly secure as some in the security industry make them out to be.
This blog post explains more on how to do it (special credit goes to Lukasz Bobrek and Pawel Kurylowicz for showing Regula how to achieve this).
As Daily Swig regular Dave Lewis has pointed out, biometrics can be a great tool – but only when they’re clearly thought out.