Top infosec trends in the social media spotlight this week

Chipzilla, Chipgate, Chipocalypse. It’s only the first week of January, and tech journos are already scraping the barrel when it comes to summarizing the revelation that all is not well inside your CPU.
Infosec employees returned to their desks on Tuesday to find the internet buzzing with rumors of a chip-level security flaw affecting modern microprocessors.
Those within the industry were initially having to rely on scattered reports of a major bug in Intel chips that allowed normal user programs to access some of the contents of the protected kernel memory.
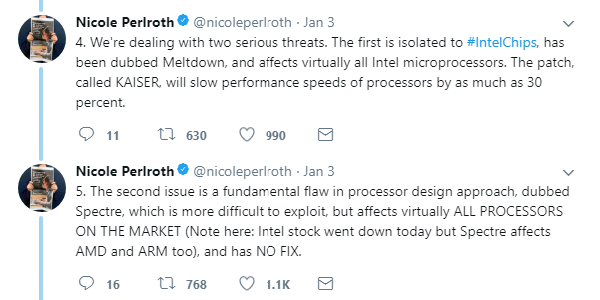
While shares in Advanced Micro Devices (AMD) surged amid rumors that the flaw was isolated to microprocessors developed by its competitor, technical papers released on Wednesday outlined two separate CPU-level vulnerabilities – Meltdown and Spectre – and confirmed that the problem is far bigger than previously thought.
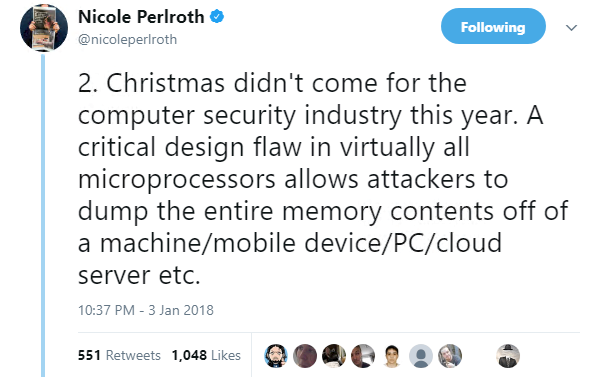
New York Times journalist Nicole Perlroth explains:
Spectre and Meltdown take advantage of flaws related to ‘speculative execution’ – a feature on modern CPUs that helps boost performance by carrying out tasks ahead of time, no matter whether or not they will be needed.
According to researchers, a security loophole could allow unprivileged applications to not only monitor these tasks, which are held in the processor’s cache, but ultimately gain access to full system memory, potentially compromising passwords, encrypted communications, and financial information.
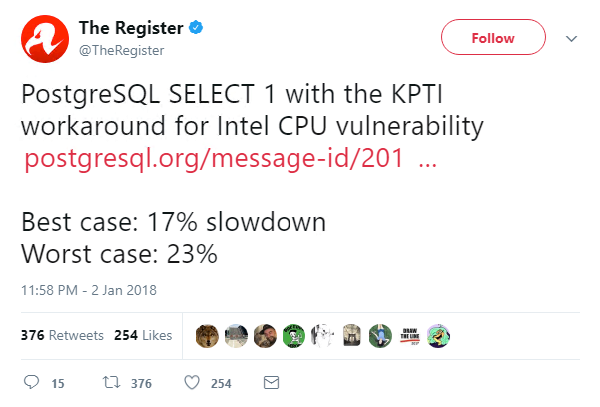
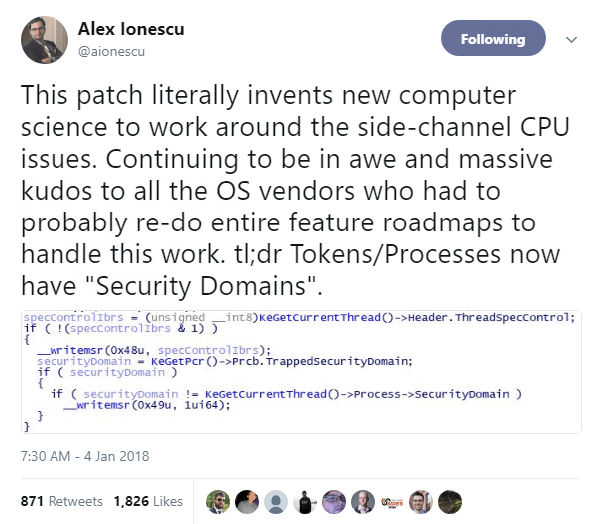
The architecture-level vulnerability cannot be mitigated with a microcode update, leaving OS vendors the unenviable task of devising and pushing through patches that establish a workaround, dubbed kernel page-table isolation (KPTI).
However, some have warned that these fixes – which split kernel and user spaces to prevent information leak – may lead to a drop in CPU performance:
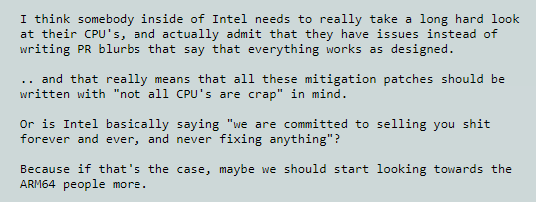
Intel was quick to swat away claims that KPTI will scupper PC, cellphone, and cloud computing speeds, but this didn’t stop Linux mastermind Linus Torvalds from pouring scorn on the Santa Clara tech firm’s “PR blurb” response:
While many within the tech community have said the flaw could linger for decades, there have been two positive takeaways this week.
First, there has been no evidence of attacks successfully utilizing these exploits in the wild – although it should be noted that detecting Spectre- or Meltdown-based hacks will prove extremely difficult, as these techniques leave no trace in traditional log files.
Second, after being faced with the major challenge of patching a problem they played no role in creating, OS vendors, whitehat researchers, and many others in the tech community have proved their ability to collaborate and implement creative fixes in an effort to reduce the likelihood of users being impacted by potentially devastating vulnerabilities.