Top infosec trends in the media spotlight this week

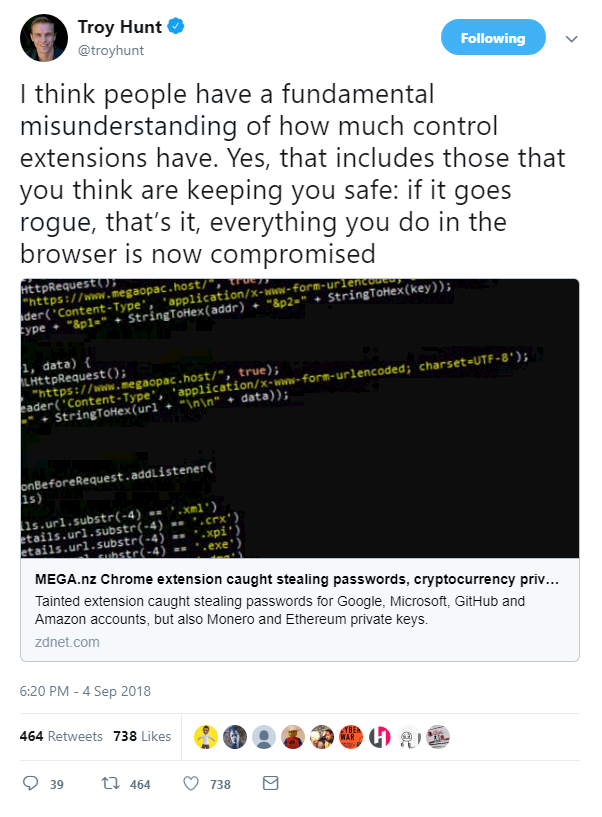
A Chrome extension was discovered to have gone rogue this week, this time silently stealing passwords and cryptocurrency keys from users.
The file-sharing service Mega.nz announced its extension had been compromised by malicious code which could steal usernames, passwords, and other data to allow hackers to login to various websites.
Google swiftly removed the browser extension from the Chrome store, and disabled the extension for users.
A timeline of events can be found here.
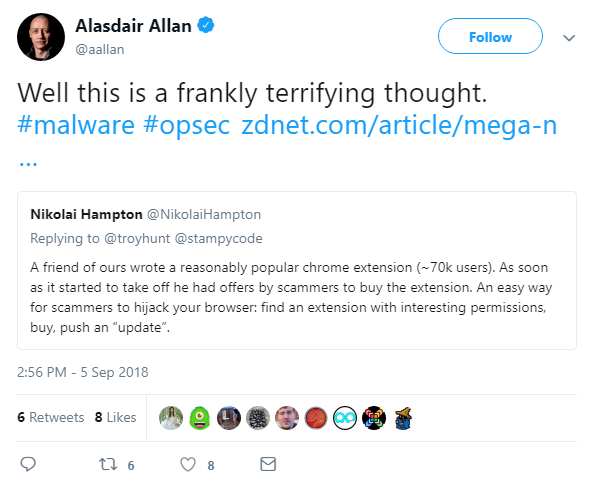
We previously detailed how bought or hacked extensions can be modified by malicious actors to steal data or compromise a system, and the growing market for fake extensions available on the web.
Other infosec thought leaders warned of this worrying trend too.
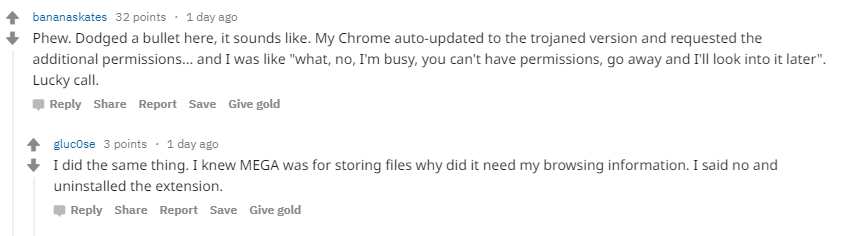
The message here is clear: check permissions when installing browser extensions, check permissions when it comes to updates, and never install anything you think is suspicious.
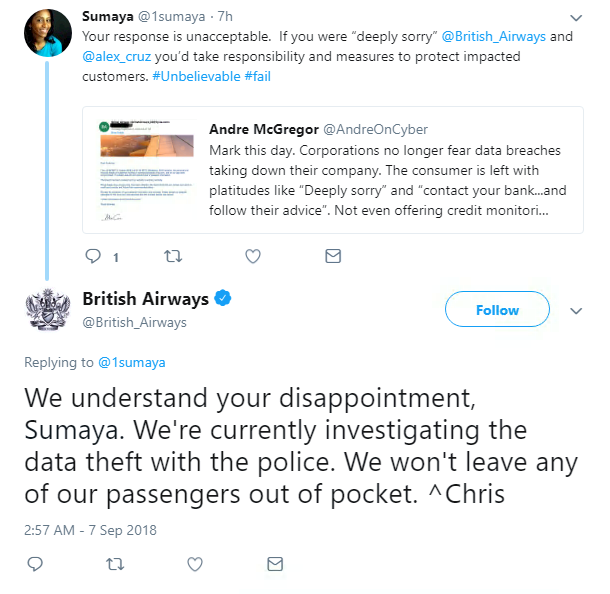
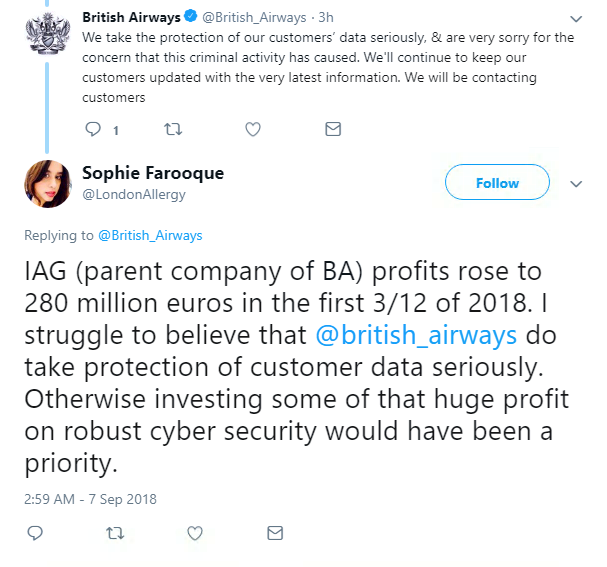
British Airways had a turbulent time this week, after a security breach saw hackers fly away with 380,000 customers’ payment details.
Bad jokes aside, the 15-day incident saw personal and financial data stolen from unidentified malicious actors from just before 11pm on August 21, until 9.45pm on September 5.
The airline was quick to report the hack in the wake of the recently-implement GDPR rules, and urged customers to contact their banks if they think they were affected.
Luckily, travel and passport details were not taken in the hack and BA said it will pay for credit monitoring services.
But customers were still angered by the data breach, which continues to become a common headache for huge companies such as BA.
In fairness to the airline, it responded quickly and included precise details of when the incident occurred – but it still begs the question of how a 15-day hack went unnoticed
The news comes just weeks after Air Canada warned that approximately 20,000 people could have been affected by a security breach that took place between August 22-24.
Twitter and Facebook were given a grilling this week in front of the US Senate Intelligence Committee.
Jack Dorsey, Twitter CEO, and Sheryl Sandberg, COO of Facebook, testified before the Senate Intelligence Committee, which was noticeably shunned by top staff at Google, about what social media bosses were doing to prevent future election meddling.
Dorsey, who has been criticized as of late for his failure to kick conspiracy theorists and Nazis off his platform, was also questioned on whether Twitter was censoring conservative voices.
He claimed they “do not shadow-ban anyone based on political ideology”.
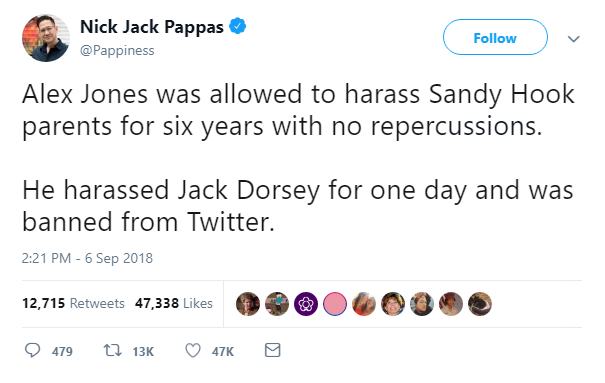
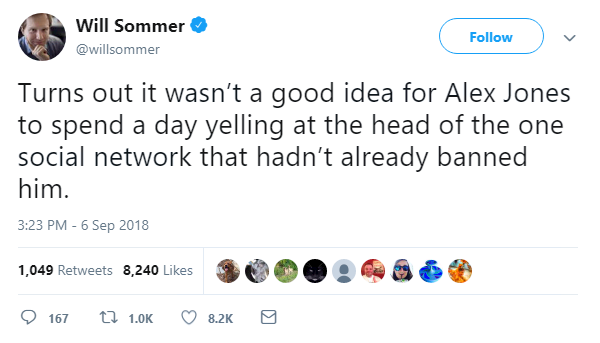
However today, InfoWars leader Alex Jones – who claimed the Sandy Hook elementary school shooting was a hoax to influence tighter gun controls – was banned from Twitter and its video-streaming platform Periscope.
It comes after he sat in the public gallery of the hearing, allegedly harassing Dorsey, reporters, and government representatives.
Dorsey was previously slammed for failing to shut down Jones’ accounts.
Sandberg was there to represent Mark Zuckerberg – who was slated for crumbling in front of the Senate earlier this year, after the Cambridge Analytica scandal.
She admitted that Facebook was “too slow” in tackling election meddling, after claims Russian-linked actors spread misinformation and propaganda on Facebook during the 2016 presidential election.
Finally, WannaCry was back in the headlines this week, as the US Justice Department charged a North Korean computer programmer with being behind the widespread ransomware attack.
On Thursday, Park Jin Hyok was charged with one count of conspiracy to commit computer fraud and abuse, and one count of conspiracy to commit wire fraud.
He is accused of being behind the 2017 WannaCry attack which crippled universities, hospitals, and banks worldwide, as well as the 2014 Sony hack, and the 2016 Bangladesh Bank hack which saw $81 million stolen.

Park is currently thought to be in North Korea, and has been charged despite his absence.
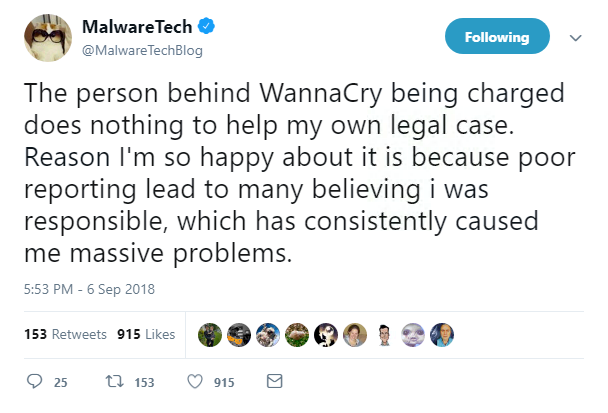
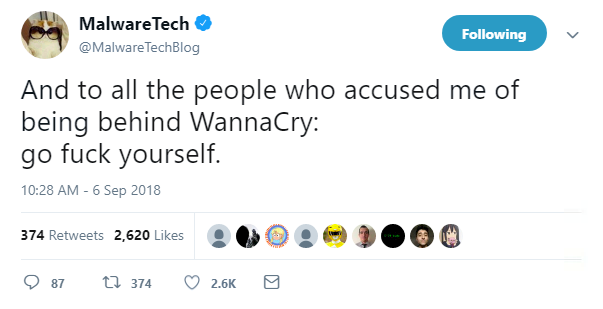
The news wasn’t just welcome to the US government, but also to Marcus Hutchins, the researcher who discovered the kill switch for WannaCry.
British citizen Hutchins was praised for shutting down WannaCry when it attacked the UK’s National Health Service back in May 2017.
But according to Hutchins, “poor reporting” led to him being accused by some as being behind WannaCry.
Hutchins is currently being held in the US after being accused of writing the 2014 Kronos banking malware.