Top infosec trends in the social media spotlight

The RSA Conference opened its doors in San Francisco this week, with the event once again offering a packed agenda covering the latest security developments and technologies.
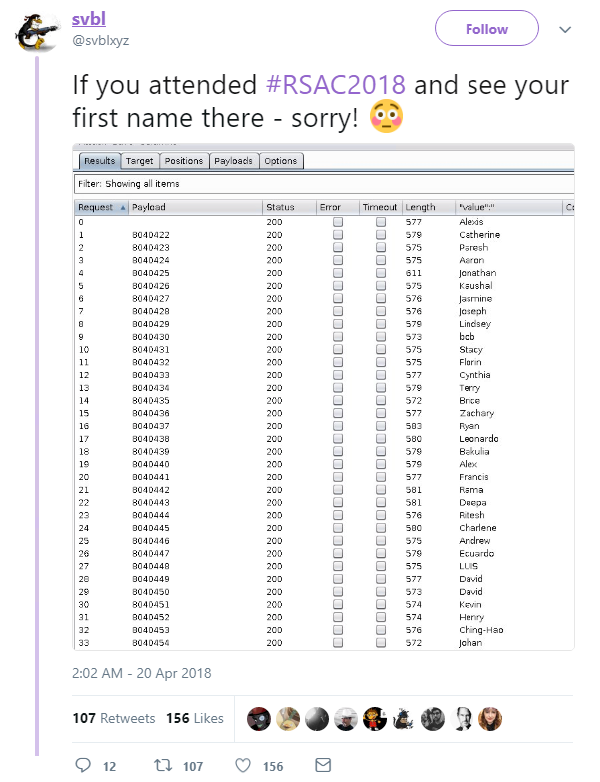
As delegates prepare for the final day of the event, a security engineer with the handle ‘svbl’ has disclosed a flaw in the RSA mobile event app that enabled him to obtain a list of attendees’ names:
Taking to Twitter in the early hours of the morning, the researcher demonstrated how he was able to obtain a list of attendees via the event app’s unsecured, public-facing APIs.
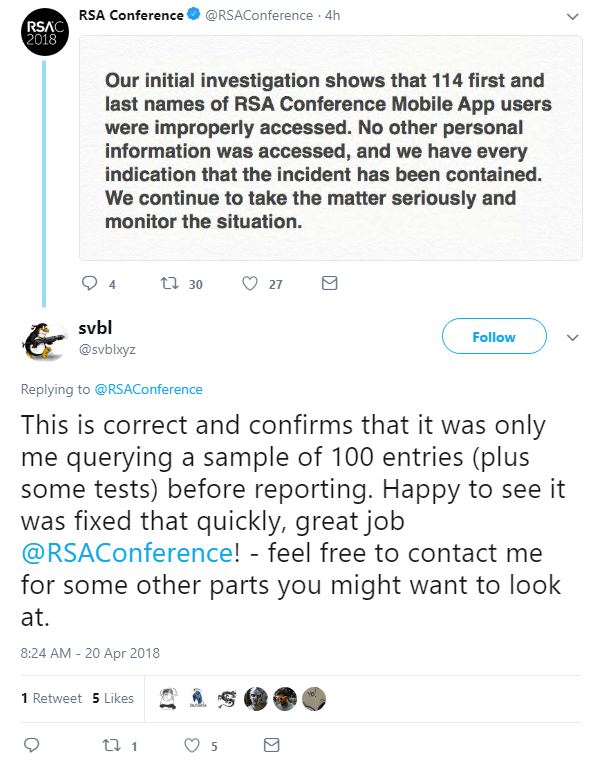
The conference organizers responded with a tweet of their own, confirming that the first and last names of their mobile app users had indeed been improperly accessed:
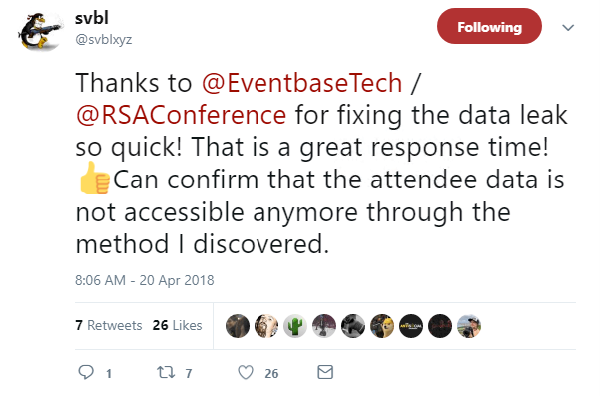
The app’s developer, Eventbase Technology, has been quick to patch the issue, but the irony of a security conference falling victim to a data breach will not be lost on delegates as they head back to the expo center this morning.
Elsewhere, Ondrej Vlcek, executive vice president and general manager of Avast, has revealed details of the company’s investigation into last year’s hack against CCleaner, a popular system cleanup and optimization tool.
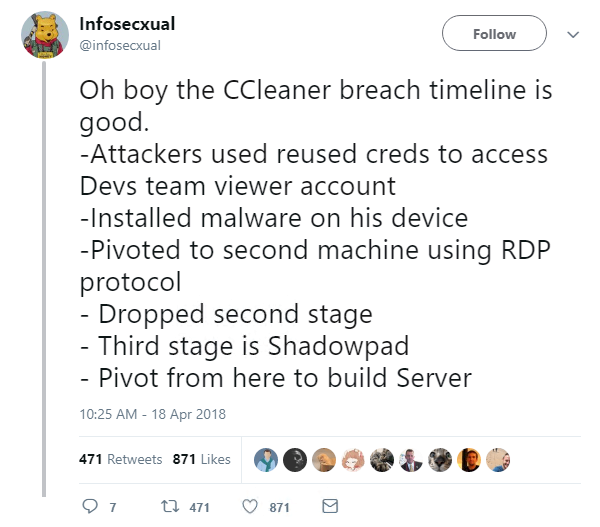
In his post-mortem of the attack, Vlcek said the threat actors first accessed Piriform’s network on March 11, 2017, four months before Avast acquired the company, using TeamViewer on a developer workstation.
“They successfully gained access with a single sign-in, which means they knew the login credentials,” he said.
“While we don’t know how the attackers got their hands on the credentials, we can only speculate that the threat actors used credentials the Piriform workstation user utilized for another service, which may have been leaked.”
According to Vlcek, the attackers were in the Piriform network five months before they snuck the malicious payload into the CCleaner build.
Avast acquired Piriform on July 18, 2017, and the first CCleaner build with the malicious payload appeared on August 2, 2017.
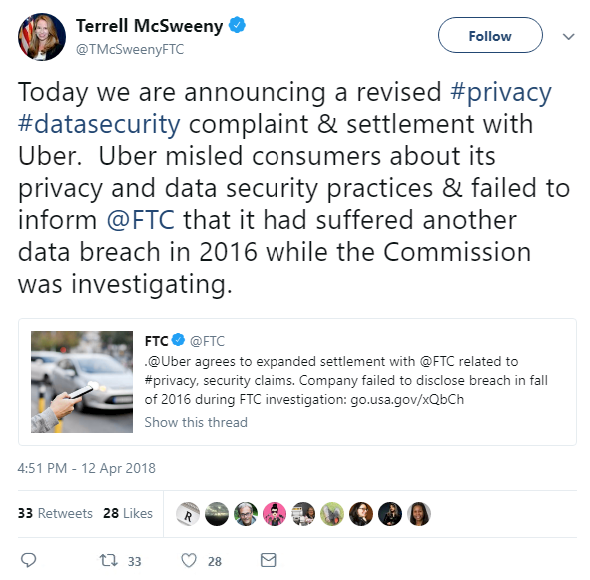
In legal news, Uber has agreed to expand the proposed settlement it reached with the US Federal Trade Commission (FTC) last year over charges that the ride-sharing company deceived consumers about its privacy and data security practices.
Following the announcement of last year’s proposed settlement, the FTC learned that Uber had failed to disclose a significant breach of consumer data that occurred in 2016.
“Due to Uber’s misconduct related to the 2016 breach, Uber will be subject to additional requirements,” the FTC said.
The revised settlement could subject Uber to civil penalties if it fails to notify the commission of certain future incidents involving unauthorized access of consumer information.
And finally, LinkedIn’s CISO Cory Scott has offered some insight into his role at the professional networking site:
In a blog post earlier this week, Scott noted that the role of chief information security officer has gained “substantial visibility” over recent years, and that his own role has changed in response to an “ever-pervasive” threat landscape.
“It is important for us to remain consistent in how we protect and use member data,” he said. “With the number of product and engineering initiatives going on at any one time, my team provides a navigational compass to inform decision makers on the direction of our roadmap.
“In my role, I have to make a lot of decisions every day, and the smaller number of blind spots in my knowledge, the better decisions I can make. The key is knowing what you don’t know and what you’re going to do address that gap in the best way possible.”