Researchers say sensitive information is for sale on two separate underground marketplaces

A breach at online marketplace IndiaMART has leaked the sensitive data of more than 40,000 suppliers.
IndiaMART is a business-to-business e-commerce site, connecting suppliers from across India. Last year, the official app had 10 million downloads.
Researcher Ashok Krishna from threat monitoring platform CloudSEK discovered that data belonging to thousands of suppliers was being sold on online forums.
The same set of information, estimated to be around 44,000 records, appears to be for sale on two separate underground websites.
Krishna investigated a sample of one of the datasets, posted for sale on June 20, and found it contained 44 separate records.
Each record was said to consist of sensitive information including suppliers’ user IDs, full names, addresses, email addresses, and phone numbers.
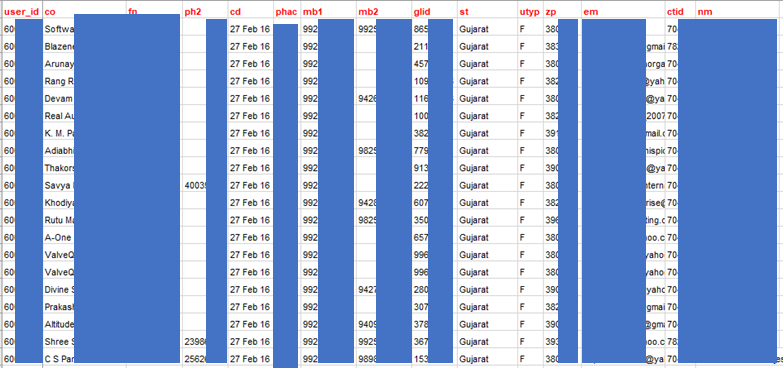 IndiaMART supplier data was found on two underground forums
IndiaMART supplier data was found on two underground forums
Krishna says he used publicly found sources to verify that the data was legitimate. The sample contains records registered in February 2016, primarily from the Indian state of Gujarat.
These details could be used in a number of ways, including being utilized for phishing campaigns, scams, and even identity theft, explains CloudSEK.
“Usually our mobile numbers and email IDs are linked to banking, mobile wallet, and other online accounts,” a blog post explains.
“Having these details makes it easier for threat actors to compromise the victims’ accounts.”
Deepanjli Paulraj, lead cyber intelligence editor at CloudSEK, told The Daily Swig: “We have been able to validate the data. It does belong to active IndiaMART vendors.”
“Whether a bug in the IndiaMART website or an unsecured database, if not remediated, could put six million-plus suppliers on the platform at risk,” the post explains.
Read more of the latest data breach news
The second set of data contains 43,920 records, the person posting it claims, however the researchers were not able to verify this data.
Suppliers using the IndiaMART platform should immediately check whether their accounts have been tampered with, CloudSEK advises.
Other recommendations include reviewing all online accounts and financial statements, cautioning friends and family against anyone impersonating you or your business, and enabling multi-factor authentication.
Researchers also urged suppliers never to share their one-time passwords (OTPs) generated by multi-factor authentication devices.
“While this is a rule of thumb, it is especially relevant in this case, because threat actors already have email IDs and phone numbers. So, the OTP is the only thing standing between threat actors and the victims’ accounts,” reads the blog.
CloudSEK also advised IndiaMART to perform an audit to uncover the full extent of the leak.
IndiaMART told The Daily Swig it was investigating the claims, but downplayed the incident as it says the data was readily available.
“At the outset, we would like to clarify that sellers basic contact information is a public information and is advertised on IndiaMART and other places like a printed directory, other internet portals and search engines.
Neither any sensitive personal information of the suppliers is displayed on our platform nor it is leaked.
Our Cyber Security and Technical Team is evaluating the report of CloudSEK which has been recently notified and is trying to find out the authenticity of the said report wherein it is claimed that the certain basic information like name, email address, contact number etc. of our listed suppliers are leaked.
Accordingly, at present, we are not in a position to acknowledge the authenticity of such a report. In case any leakage of even the smallest level is identified by our cybersecurity team post-investigation, we will take the best possible steps to avoid such repetition in future.”
This article has been updated to include comment from IndiaMART.
READ MORE Bug bounty powerhouse: India takes top spot for Bugcrowd hackers worldwide






