Five-year-old router bug leaks MAC addresses and other unique identifiers

More than 25,000 Linksys Smart WiFi routers are vulnerable to an information disclosure flaw that gives unauthorized third parties easy access to the MAC addresses of all connected devices, along with a wealth of other details.
The vulnerability was disclosed by Bad Packets Report, a US-based cyber threat intelligence firm, which found that more than 30 Linksys router models were leaking device information across the internet.
Bad Packets’ proof of concept couldn’t be simpler: to exploit the vulnerability, a user simply needs to enter the router’s public IP address in a web browser, open the developer console, find the Network tab, and scroll down to the JNAP package.
A treasure trove of details – including the MAC address of every device that has ever connected to the router, device names, and operating systems – are served up in plaintext:
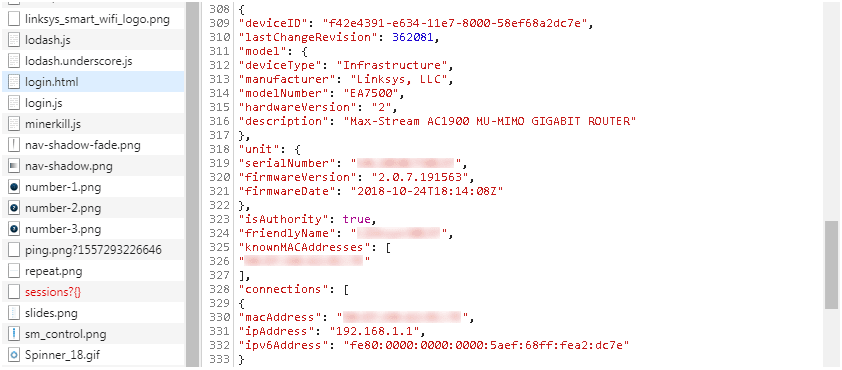
In some cases additional metadata is logged, including device type, manufacturer, model number, description, Bad Packets said.
“This sensitive information disclosure vulnerability requires no authentication and can be exploited by a remote attacker with little technical knowledge,” explains the report’s author, Troy Mursch.
According to the researcher, other sensitive information about the router, such as the WAN settings, firewall status, firmware update settings, and DDNS settings are also leaked publicly.
What’s more, Bad Packets said it would be trivial for any unauthenticated attacker to quickly enumerate which Linksys routers have not had their default password changed.
Gaining administrative access to any of these routers would allow a malicious user to obtain the SSID and WiFi password in plaintext, change the DNS settings to hijack web traffic, and conduct all manner of nefarious network activity.
According to Mursch, the vulnerability in question was flagged (and supposedly patched) five years ago.
“Our findings indicated otherwise,” he said, adding that the Linksys security team determined that Bad Packets’ security advisory was “Not applicable / Won’t fix” and subsequently closed.
He added: “In any scenario, publicly leaking the historical record of every device that’s ever connected to the Linksys Smart WiFi router is a privacy concern that shouldn’t be taken lightly.”
“This information allows attackers to gain visibility inside your home or business network, enabling them to conduct targeted attacks.”
Linksys did not immediately respond to The Daily Swig’s request for comment. This article will be updated as and when we hear back from the vendor.






