‘Motivated attackers are still winning the war – whether they are bad actors or security professionals’

HD Moore, one of the security industry’s most famous white hat hackers, transformed the world of penetration testing as the founder of the Metasploit Project.
Since leaving Rapid7 (the firm behind Metasploit) in 2016, Moore has turned his attention towards the use of active scanning for network discovery and asset inventory purposes.
The Daily Swig recently caught up with Moore to talk about his research interests, bug bounties, and the current operational environment for security researchers.
Most people in infosec will know you as the developer of the Metasploit Project, but what are your current research interests?
HD Moore: I am focused on remote device fingerprinting and protocol analysis as part of my work on Rumble.
Rumble provides network discovery and asset inventory via unauthenticated active scanning. It came out of my experience building security tools and realizing that nobody really does the discovery side well.
Doing it right means investing the same level of effort as unauthenticated vulnerability scanning, but using the results for device identification instead of security scanning.
In a lot of ways, this is the same work I have been doing for the last 20 years: using research, internet-wide scans, and data analysis to extract useful information from the network without credentials.
RECOMMENDED Bug Bounty Radar // The latest bug bounty programs for March 2020
My view is that active unauthenticated scanning is still the easiest way to provide instant visibility, but it requires a lot of research and optimization to get right.
Our public research in this space has included some neat DNS tricks, useful data gathering from SNMP v3, and some fun information leaks in the SMB v2 protocol.
In addition to my work on Rumble, I still help with R&D, penetration tests, and security assessments at Atredis Partners.
I like how consulting and product development feel complementary and keep me focused on solving real-world problems.
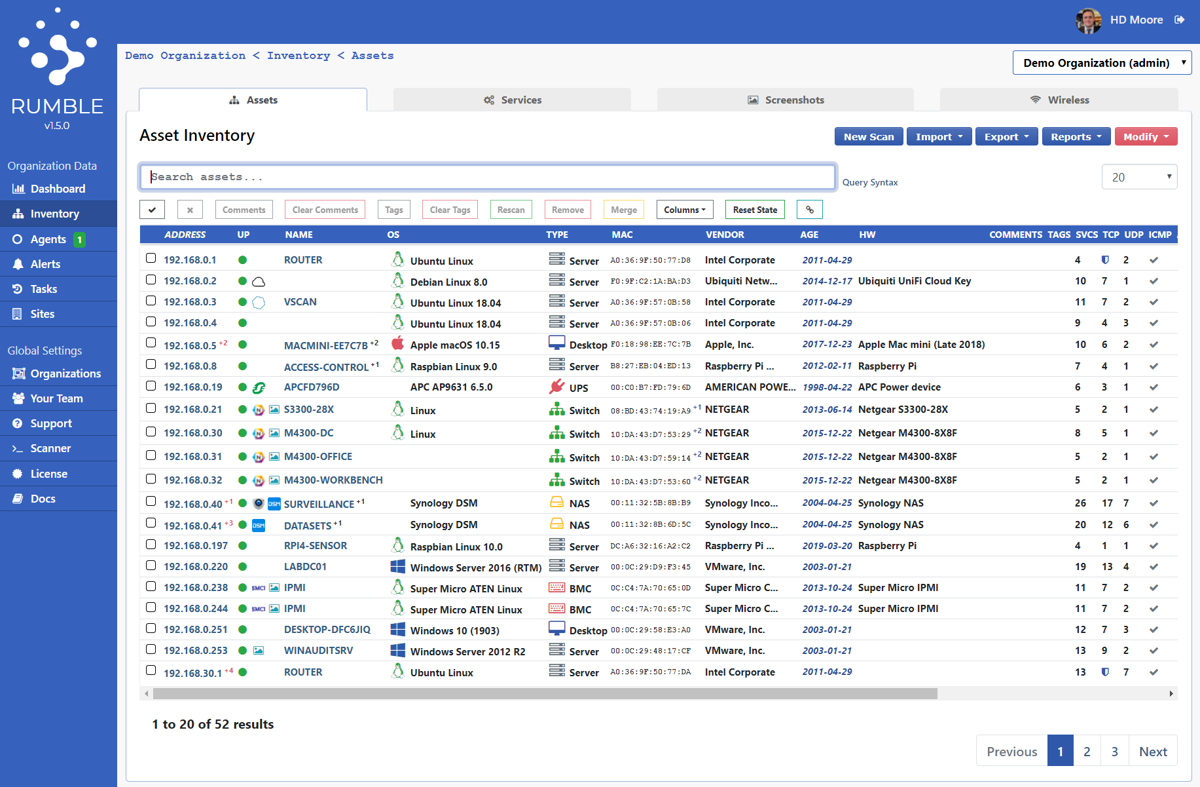 Rumble works without the need for span ports, dedicated credentials, or privileged network access
Rumble works without the need for span ports, dedicated credentials, or privileged network access
The Daily Swig writes quite a lot about bug bounties, so we’re interested in getting your perspective on these programs as a well-known security researcher. Do you think defenders are getting better at collaborating, or are they still been outpaced by the bad guys, a criticism you've made in the past?
HDM: Bug bounties, from the perspective of a 90s hacker, are absolutely amazing. Not only do tons of companies allow you to test their security without any pre-approval, but they actually pay for it if you find something!
Bug bounties have helped with skill-building across the security community in a way that we could have only dreamed about 10 years ago.
[But] motivated attackers are still winning the war – whether they are bad actors or security professionals.
We are still see zero-day bugs being exploited by attackers prior to the good guys knowing about them (recently, Microsoft’s Type-1 Font issue from March 2020).
I don’t think this balance will change anytime soon. Instead, I believe defenders will continue to improve their infrastructure and response capabilities, but will always be on the back foot.
What are your thoughts on the current operational environment for security researchers? In the past you’ve warned that security laws have been misapplied to target security researchers, so I was wondering whether or not we’re over that?
HDM: The legal environment for security research seems to be improving.
Bug bounties and internet-wide scanning have reduced the number of cases for ‘hacking attempts’; the volume alone makes filtering the good from the bad more difficult; and prosecutions have been moving towards cases that involve clearly bad intentions, as opposed to just scary-looking network traffic.
That said, the laws haven’t actually improved, and are still easy to abuse, especially in high-profile cases that embarrass powerful organizations. I believe we still need a comprehensive reform of our computer security laws.
 HD Moore founded the Metasploit Project
HD Moore founded the Metasploit Project
What changes do you think the current coronavirus pandemic and the greater use of remote working might have on the world of cybersecurity over the next two or three years?
HDM: The Covid-19 pandemic is reshaping the corporate security model and accelerating the BYOD [Bring Your Own Device] and zero-trust trends already in motion.
Remote access services are more exposed than ever as organizations struggle to support the increase of work-from-home staff. Home environments are also receiving scrutiny as employees try to adapt to remote work.
I believe we are going to see an increase of endpoint security issues, including malware, ransomware, and compromised consumer networking equipment involved in data breaches as a result.
YOU MIGHT ALSO LIKE Latest web hacking tools – Q1 2020






