Red teamers have a new tool in their post-exploitation arsenal
In the post-exploitation phase of an attack, red teamers will typically monitor compromised machines to determine the value of the data they contain, and whether this data can be used to further compromise the network.
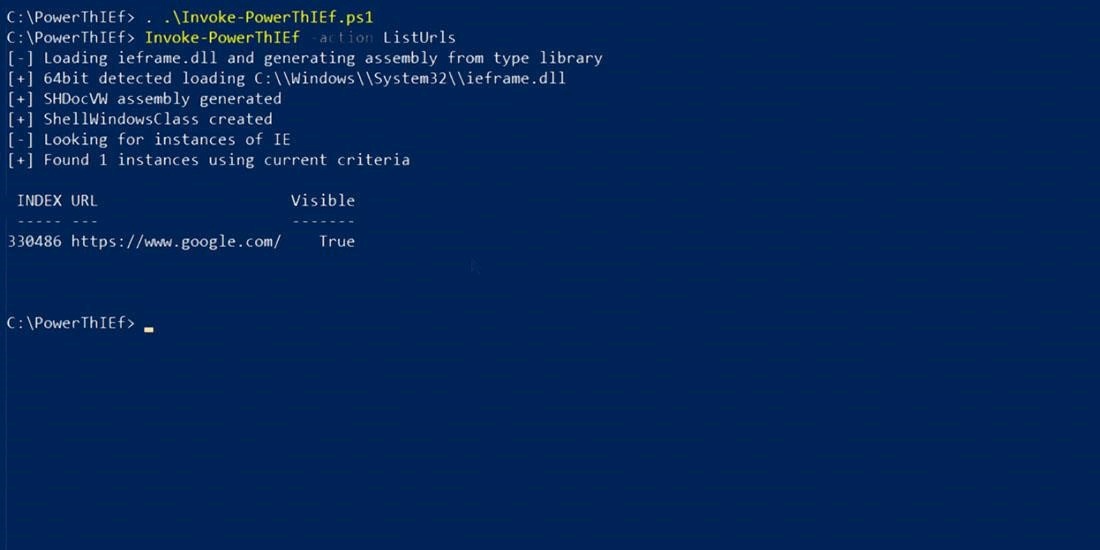
Ethical hackers now have a new tool in their arsenal during this critical period, following the release of PowerThIEf, a new library that uses Microsoft’s Component Object Model (COM) interface to expose the currently active Internet Explorer windows and tabs.
The tool can also be used to capture user credentials and other secrets – even if they are using a password manager.
PowerThIEf was developed by Rob Maslen, principal security consultant at Nettitude, who presented the toolkit at this year’s SteelCon event in the UK.
“During some of our red team engagements, we quite often find that Internet Explorer is still being used as the business browser of choice,” Maslen explained. “We have also found that quite a lot of intranet sites and internal business applications mandate its usage.
“Consequently, a lot of targets we need to access during engagements either have their credentials inputted into or have session cookies stored within an Internet Explorer session.”
Launched by Microsoft in 1993, COM is a core component of Windows that allows structured communication and interoperability between subsystems.
While the interface allows interoperability between these components, Maslen drew on previous research to develop a new technique that uses COM to enumerate all the Internet Explorer windows on a machine; capture credentials in transit; inject JavaScript into any running IE window; view and edit the DOM; and force IE to load any DLLs of an attacker’s choosing.
“Despite the programming constructs and some of the techniques being well documented, there didn’t appear to be a library out there which brought it all together in order to help a red team,” Maslen said in a recent blog post that introduces the post-exploitation toolkit.
According to the security consultant, PowerThIEF can be used to steal user credentials even if they are using password managers, which render traditional key-logging ineffective.
Of course, the caveat here is that PowerThIEf is only useful against compromised targets using Internet Explorer.
But despite the fact that the market share of Microsoft’s now-decommissioned browser now trails behind many other platforms, Maslen said it remains ubiquitous in the business world – and therefore still a highly valued target.
“Unfortunately, web applications for business are still generally accessed by Internet Explorer,” he said during SteelCon. “It still seems to be the business browser of choice.”
“I started thinking about this functionality and the fact that within a red team engagement we are looking to target people who are probably using IE, and that this might make a handy library. So here it is: PowerThIEf.”






