Wretched hives of villainy exposed

A study of the digital underground by Trend Micro has revealed that the IoT attacks and services market is rapidly growing and diversifying.
Cybercriminals around the world are actively discussing how to compromise connected devices, and how to abuse these devices to further their moneymaking scams.
Researchers from Trend Micro analyzed forums in the Russian, Portuguese, English, Arabic, and Spanish language-based underground markets in order to get the low-down on how cybercriminals are abusing and monetizing connected devices.
Russian and Portuguese-speaking forums, in which financially-driven attacks are most prominent, turned out to be the most advanced criminal markets in the sample set.
In these forums, cybercriminal activity is focused on selling access to compromised devices – mainly routers, webcams, and printers – to earn a dishonest income from black hat hacking exploits.
“Cybercriminals are well on their way to creating a thriving marketplace for certain IoT-based attacks and services,” said Steve Quane, executive vice president of network defense and hybrid cloud security for Trend Micro.
“Criminals follow the money – always. The IoT market will continue to grow, especially with landscape changes like 5G.
"While IoT attacks are still in their infancy, we also found criminals discussing how to leverage industrial equipment for the same gain," he added.
School for scoundrels
The forums are full of discussions about IoT security-related news and research, hacking tutorials, offers to sell access to pre-hacked devices (mostly routers and IP cameras), and more.
IoT devices have become a platform for botnet attacks over recent years. This is reflected in the forums, with botnet-related chat rife in across several cybercriminal underground communities.
Sharing of Mirai (a notorious strain of IoT malware) modifications was “rampant, at least for the English-speaking underground community”, Trend Micro reports.
Talk surrounding Shodan, the IoT search engine, was also commonplace. “Discussions about Shodan included tutorials for automating searches, Shodan accounts for sale, and even a program that shows canned Shodan searches for several devices,” the researchers found.
Several underground communities offer the sale of bespoke services and programs. These include IoT-based virtual private networks (VPNs), distributed denial-of-service (DDoS) platforms, and DNS services.
“Although the level and structure of monetization for IoT attacks and threats vary across communities, our findings prove that cybercriminals have a definite and diverse interest in IoT-related opportunities,” Trend Micro reports.
“They scope what the IoT has to offer them, as well as future possibilities once new devices hit the market.”
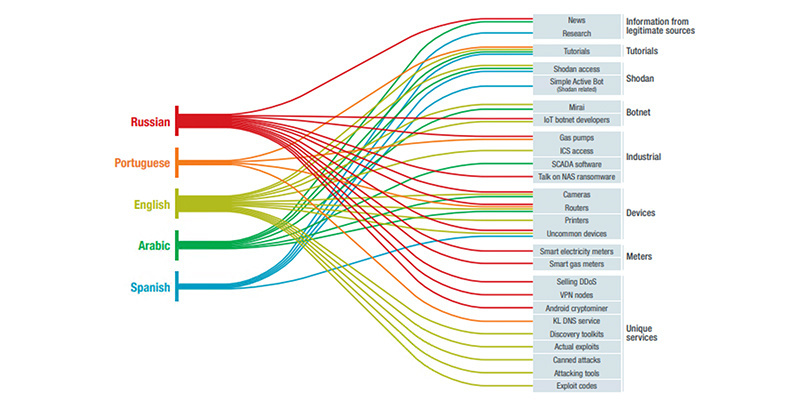 Visual summary of the topics discussed in five underground communities (Image: Trend Micro)
Visual summary of the topics discussed in five underground communities (Image: Trend Micro)
Around the world
One post in a Russian forum offered DDoS services based on infected IoT devices at just $40 per month. Another Russian language ad offered to sell an IoT-based VPN (compromised router with OpenVPN) for $10 per proxy.
The Portuguese-speaking criminal underground offers services that use infected routers and similar devices as a platform for criminal services. This is the case for ‘KL DNS’ – a service sold on Brazilian forums to perform supposedly fool-proof phishing campaigns combined with DNS redirection and, in some cases, SMS spamming.
“‘KL DNS’ services start with a network of infected routers or other home devices,” Trend Micro researchers explain.
“The criminals change the DNS configuration on these devices so that the name resolution is done by a hacker-controlled external server.”
“From that point on, when a computer within the infected device’s network tries to resolve, for example, ‘bank.com’, the browser would instead redirect the request to a phishing site that looks identical to the real bank website.
“The main selling point of this system is that, for it to work, it would not need to infect a victim’s computer, only the internet-connected router.
“The criminals sell these redirection services so that phishers can host copycat web servers and gather stolen credentials and credit card information. Prices are around R$1,000 per week (about $260),” the researchers conclude.
Meanwhile, over in English-language forums, the market focused on IoT malware. Mirai setup was offered at $5, while more serious would-be crooks were offered botnet panel/code for $600.
Illicit Shodan access retails at around $25, Trend Micro’s researchers found.
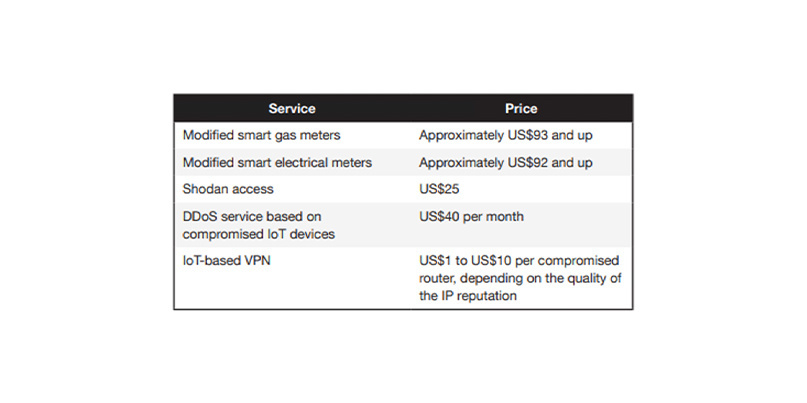 Prices of the services found on Russian forums (Image: Trend Micro)
Prices of the services found on Russian forums (Image: Trend Micro)
Security partnerships needed
Trend Micro found that most conversations and active monetisation schemes at present are focused on consumer devices.
However, discussions on how to discover and compromise connected industrial machinery are also taking place, especially in relation to the programmable logic controllers (PLCs) used to control large-scale manufacturing equipment.
The most likely business plan to monetise attacks against these industrial devices involves digital extortion attacks that threaten production downtime.
Additionally, the report (PDF) predicts an increase in IoT attack toolkits targeting a broader range of consumer devices, such as virtual reality devices. The opportunities for attackers will also multiply as more devices are connected to the internet, driven by 5G implementations.
Manufacturers need to partner with IoT security experts right from the design phase in order to minimise the potential for harm, Trend Micro advises.RECOMMENDED IoT security: India faces growing onslaught of cyber-attacks






