Impacted by Yatron and FortuneCrypt? Get your files back without paying crooks anything

Kaspersky has released free decryptor tools for two newly discovered ransomware strains – Yatron and FortuneCrypt.
Both decryptors were made publicly available on Wednesday (September 25) after the Russian cybersecurity firm found weaknesses within the code and cryptographic scheme of each malware.
Yatron, a less technically advanced Ransomware-as-a-Service (RaaS) utility that surfaced earlier this year, is reckoned to make use of well-known exploits EternalBlue and DoublePulsar in order to spread. The malware targets Windows machines.
According to Kaspersky, Yatron malware is built, in part, via code from another piece of ransomware – a open source trojan called Hidden Tear, which Kaspersky reports as active predominately in Germany, China, Russia, India, and Myanmar.
Groups slinging the ransomware has released multiple variants since its first arrival in 2015.
“Among the numerous modifications of Trojan-Ransom.MSIL.Tear, this one can be distinguished by the extension .Yatron that’s appended to encrypted files,” Kaspersky said in a blog post.
“However, using third-party code without checking it raises the risk of critical vulnerabilities affecting the overall effectiveness of the program.”
A lack of attention paid to secure development best practices and reliance on third-party code meant Yatron was easy for Kaspersky to reverse engineer.
The cybersecurity firm was then able to produce a key to release files impacted by Yatron, which it has now added to its RakhniDecryptor tool. A separate decryptor for Hidden Tear has been available since last year.
Kaspersky said: “There are two common scenarios behind the creation of this kind of malware: in one, the criminals prefer to just reconfigure existing malicious source code; in the other, they choose to write their own ransomware, sometimes even using very specific languages.”
BlitzRAID
A decryptor published for FortuneCrypt – ransomware that has claims victims in Russia, Brazil, Germany, South Korea, and Iran – highlights this second scenario.
“FortuneCrypt is the first ransomware we’ve seen that’s written in Blitz BASIC,” Kaspersky said.
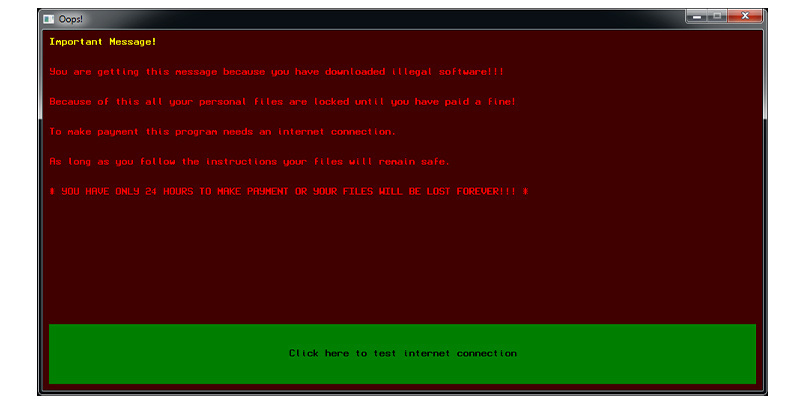 A screengrab of the FortuneCrypt ransom note (image credit: Kaspersky)
A screengrab of the FortuneCrypt ransom note (image credit: Kaspersky)
It appears that a weak cryptographic scheme within FortuneCrypt, overall, allowed the cybersecurity firm to produce the “unique decryptor.”
Ransomware decryptors have burst onto the scene to assist victims in recovering their files following attacks, but are by no means the best much less only solution to ransomware recovery.
“So many times we see organizations recovering, reinstalling, moving on, and they don’t realize that something like Trickbot [banking trojan] is still on the system,” said Sherri Davidoff, CEO of LMG Security and BrightWise Inc, during a recent Black Hat webcast on ransomware network behavior and defense.
“Often there is a really big lag time,” she added, urging organizations to look for signs of infection on backups before using them to restore systems.
“Trojans can be hanging out on systems that were not encrypted and a lot of people don’t look at these because they weren’t taken down with ransomware,” Davidoff said.
The Kaspersky tools for decrypting Yatron and FortuneCrypt are also available through the No More Ransom project.
YOU MIGHT ALSO LIKE French authorities publish free PyLocky decryptor






