Researcher reveals how chained bugs resulted in complete e-reader takeover

A researcher detailed how he chained a series of vulnerabilities to achieve remote code execution (RCE) on an Amazon Kindle e-reader.
Researcher Yogev Bar-On, of Readlmode Labs, who discovered the now-patched issue, detailed in a blog post published today (January 21) how he was able to access a victim’s Amazon account simply by knowing their email address.
Amazon has released fixes for the bugs, which can be found in Kindle firmware version 5.13.4.
Drip-down effect
The attack – dubbed ‘KindleDrip’ – relied on three vulnerabilities found in the e-reader, Bar-On told The Daily Swig.
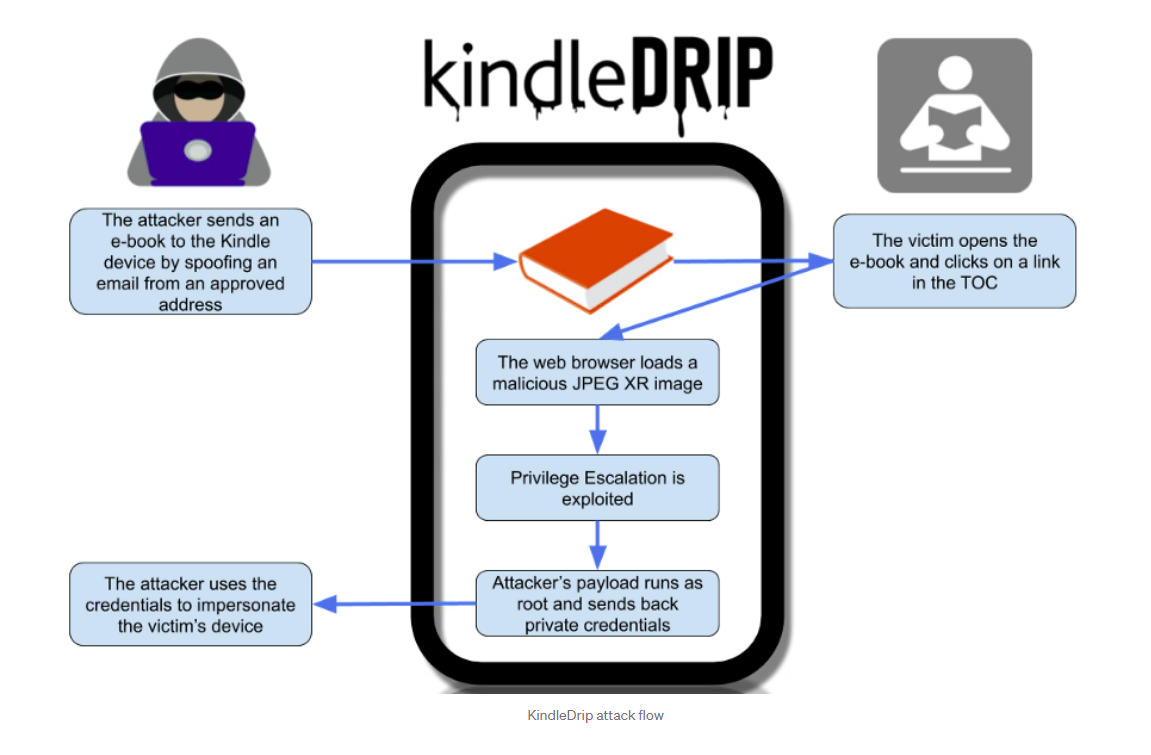
The first bug allowed a spoofed email address to bypass authentication checks, enabling a malicious e-book file to be sent to a victim’s device.
Amazon’s ‘Send To Kindle’ feature gives users the option to send a purchase directly to their device using a list of pre-approved senders such as their Kindle email address, which is automatically generated by Amazon.
Read more of the latest bug bounty news
Bar-On, however, was able to spoof a user’s Kindle email address and send an e-book to their device, bypassing authentication checks.
There was no indication that the e-book was received from an email message, and the e-book also appeared on the home page of the Kindle with a cover image of the attacker’s choice – “which makes phishing attacks much easier”, Bar-On said.
The spoofed email was “specifically the email address Amazon generated for the device”, Bar-On told The Daily Swig. He also noted how this email address can be predicted, since Amazon uses the format name@kindle.com.
The chain
The second issue was a vulnerability in the way that the Kindle parses the image format JPEG XR, which can be loaded via a web browser.
If the user clicks a link in the e-book, such as one in the table of contents, it will open a browser window that contains the malicious JPEG XR image.
The image is parsed and runs arbitrary code under the context of a weak user.
A third vulnerability, a privilege escalation bug, is exploited and the attacker’s payload runs as root.
Chained together, the three bugs could enable the attacker to achieve RCE and send back the private credentials to themselves.
Reward
A proof-of-concept video shows how Bar-On was able to carry out the attack, which concluded by successfully accessing the victim’s Amazon credentials and logging into their account:
Bar-On was awarded an $18,000 bug bounty payout from Amazon, which patched the bug on December 10, 2020, within a 90-day disclosure timeline.
Kindle customers are urged to update to protect against the vulnerabilities.
Amazon was “responsive and cooperative”, the researcher said.
“Finding the vulnerabilities and exploiting them was not easy, but once it was done the exploitation was very simple to execute,” Bar-On added.
YOU MAY ALSO LIKE ‘Train the basics’ – Bug bounty hunter ‘Xel’ on forging a lucrative career in ethical hacking






