‘Multi-perspective’ assurance method reduces the risk of certs being mistakenly issued to fraudsters

Let’s Encrypt has started rolling out a new multi-perspective domain validation system to tackle the nascent challenges posed by Border Gateway Protocol (BGP) hijacking.
Last week, the non-profit certificate authority (CA), a provider of free SSL/TLS certificates, said in a blog post that the new service switches domain validation from one verifiable instance to multiple perspectives.
Domain validation is used to vouch for an applicant when they request a certificate, building a level of trust based on the evidence that the applicant controls the domain for which they have requested a certificate.
Without extensive validation checks, including whether or not an applicant is able to place a file in a particular domain path, fraudsters may be able to obtain certificates for domains they do not own in order to use them for malicious purposes.
However, the domain validation process itself is vulnerable to Man-in-the-Middle (MitM) attacks, in which a cyber-attacker can secretly capture, alter, and relay communications between a CA and a client who mistakenly think they are communicating over a secure link.
This can result in a CA issuing security certificates to fraudsters.
What is BGP?
Border Gateway Protocol is a standardized networking technology that’s used for exchanging preferred routing path information between carriers and ISPs.
The technology’s insecurity has been a problem for years, with problems often stemming from either route leaks or equipment misconfiguration.
It’s suspected that nation-states have abused BGP inherent insecurity to re-route and snoop upon internet traffic although the extent of such suspected abuse is unclear.
Traffic hijacking attacks
Research conducted by Princeton University academics Henry Birge-Lee, Yixin Sun, Anne Edmundson, Jennifer Rexford, and Prateek Mittal has demonstrated how vulnerabilities in the Border Gateway Protocol (BGP) can be used to conduct traffic hijacking attacks (PDF), a threat Let’s Encrypt wants to counteract.
“Such attacks are rare today, but we are concerned that these attacks will become more numerous in the future,” the non-profit says. “We don’t want to wait until we can depend on BGP being secure.”
By now validating from multiple perspectives as well as Let’s Encrypt data centers, the CA authority says that BGP hijacking is made more difficult as attackers must compromise three different network paths at the same time – not only the data center channel, but also at least two out of three different traffic paths.
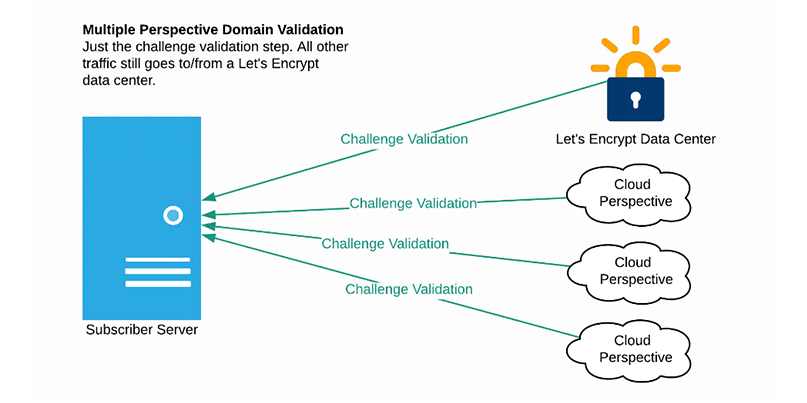 Let’s Encrypt is now validating from multiple perspectives to make BGP hijacking more difficult to pull off
Let’s Encrypt is now validating from multiple perspectives to make BGP hijacking more difficult to pull off
Let’s Encrypt is currently serving more than 190 million websites, most of which will benefit from the new system immediately. The organization believes it is the first CA to implement multi-perspective validation at scale.
The approach is designed to reduce risk of attacks that redirect network traffic during the domain validated certificate issuing process.
Speaking to The Daily Swig, a Let’s Encrypt spokesperson said Amazon Web Services (AWS) is currently being used for all three additional perspectives, but the company plans to move one of the perspectives to Google Cloud and another to Microsoft Azure.
“All websites go through a domain validation process in order to get a certificate,” the spokesperson added.
“Most will start using the new multi-perspective validation system immediately. The rest will start in June as some our subscribers needed a bit more time to make the transition.”
Let’s Encrypt will continue to work with Princeton University to refine the technology.
Princeton Professor Prateek Mittal told us that the system’s deployment is a “significant and critical milestone for security” and the main area for future improvement will be the expansion of Let’s Encrypt deployment to include more diverse and numerous perspectives, further mitigating the risk of successful BGP attacks.
RELATED BGP: Internet observatory gives visibility to routing problems






