Image/script duality trickery
Cybercriminals have started using so-called ‘polyglot images’ to disguise malvertising attacks.
Polyglot exploits center around malicious payload files that can be interpreted as either an image or a piece of JavaScript.
The tactic – spotted in the wild by researchers at ad fraud prevention firm Devcon – has been adopted by a group hoping to pass off malicious JavaScript as artwork.
The approach is apparently motivated by an attempt to foil the scanning of JavaScript files for malicious content by ad networks.
Black hats have manipulated file headers so that a payload file can be interpreted as either a BMP image or JavaScript, Devcon researchers said.
The latest versions of popular browsers such as Chrome and Firefox enforce content type, so this kind of trickery will fail in many cases.
Surfers still using Internet Explorer, however, are still at risk of attack from polyglot-based exploits, which offer crooks advantages over what might be possible using standard steganographic attacks.
In this scenario, additional JavaScript outside the image that knows the patterns and offsets in order to unpack malicious code would be needed. No malicious external script is necessary to extract the payload associated with polyglot exploits.
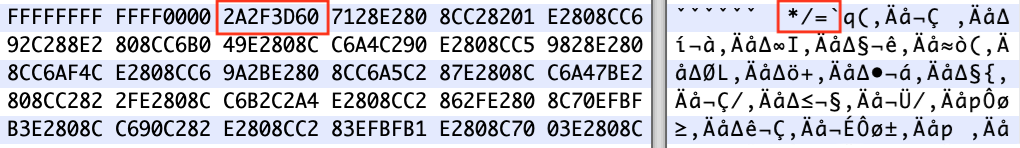 Turning a BMP file into a JavaScript variable
Turning a BMP file into a JavaScript variable
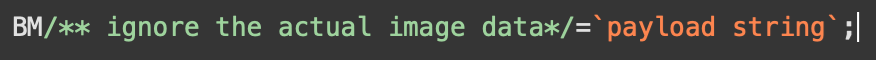
The attacker here has changed the size of the image so that the value matches character codes for /** – a combination of characters that creates a JavaScript comment.
JavaScript comments are used to make the JavaScript Interpreter ignore everything in-between these characters. i.e /* ignore me */, as Devcon explains in a blog post.
“The JavaScript Comment is terminated with */. The attacker then adds the characters = and `. This turned the file type BM (BitMap) into a JavaScript variable and set it to another heavily obfuscated payload,” the company said.
 How the file is interpreted by the browser
How the file is interpreted by the browser
Devcon added: “The attack we found loads what looks like a normal BMP file but when loaded in the browser as JavaScript it will load the BM variable into memory. Later parts of the image file contain a decoder script that is also highly obfuscated JavaScript.
“This attack has many layers and new techniques to attempt to hide what it’s true nature is and to hinder white hat reverse engineers from figuring out exactly how it works.”
The attack vector at the heart of this trickery is not that new. According to Devcon, these types of techniques have been “well known to security researchers and pen testers to execute shell code and deploy server-side attacks”.
JavaScript/GIF polyglots are a known way to work around a server’s Content Security Policy to execute cross-site scripting attacks, for example, as well as in similar attack scenarios (PDF).
The significance of the latest attacks is that it provides evidence that more advanced groups are now moving into the ad fraud space to exploit users, Devcon warns.






