Is that all it’s got? That’s not the half of it, researchers warn

A new Linux trojan targeting servers – including AWS-hosted machines – is being harnessed in an ongoing hacking campaign initially aimed at cryptocurrency mining.
As-yet unidentified hackers are using a recently patched vulnerability in the ThinkPHP framework to hack into vulnerable servers and plant the backdoor trojan, dubbed ‘SpeakUp’ (a reference to one of its command and control names).
The backdoor is currently being used to spread the XMRig crypto-miner, according to security researchers at Check Point.
Experts at the security firm warn that the malware payload could easily be switched to more damaging code that doesn’t simply siphon off resources to mine cryptocurrency.
According to XMRHunter, wallets linked to the hack hold a total of 107 Monero coins (equivalent to $4,600) – a modest return thus far.
The attack is gaining momentum and targeting servers in East Asia and Latin America, including machines hosted by Amazon Web Services (AWS).
Check Point warns the malware poses a threat beyond the initial servers it infects. SpeakUp also comes with a worm-like Python script which allows the backdoor to scan and infect more Linux servers within its internal and external subnets.
ThinkPHP global installation data (Shodan)
The malware uses a predefined list of usernames and passwords in an attempt to login to admin panels via a brute-force attack as well as attempting to exploit vulnerabilities in JBoss, Oracle WebLogic Server, and other middleware in its attempts to spread.
“SpeakUp acts to propagate internally within the infected subnet, and beyond to new IP ranges, exploiting remote code execution vulnerabilities,” according to Check Point. “In addition, SpeakUp has the ability to infect Mac devices with the undetected backdoor.”
“SpeakUp’s obfuscated payloads and propagation technique represent a significant threat, beyond deploying basic crypto-mining malware,” it added.
The CVE-2018-20062 vulnerability in ThinkPHP is being abused by hackers to upload a PHP shell that serves and executes a Perl backdoor.
The sample analyzed by Check Point was observed targeting a machine in China on January 14, 2019, and was first submitted to VirusTotal on January 9, 2019.
The vulnerability at play – rated critical – was discovered in November and allows “remote attackers to execute arbitrary PHP code via crafted use of the filter parameter” and get a shell.
One of a pair of ThinkPHP exploits discovered over recent weeks is likely the vector of the attack.
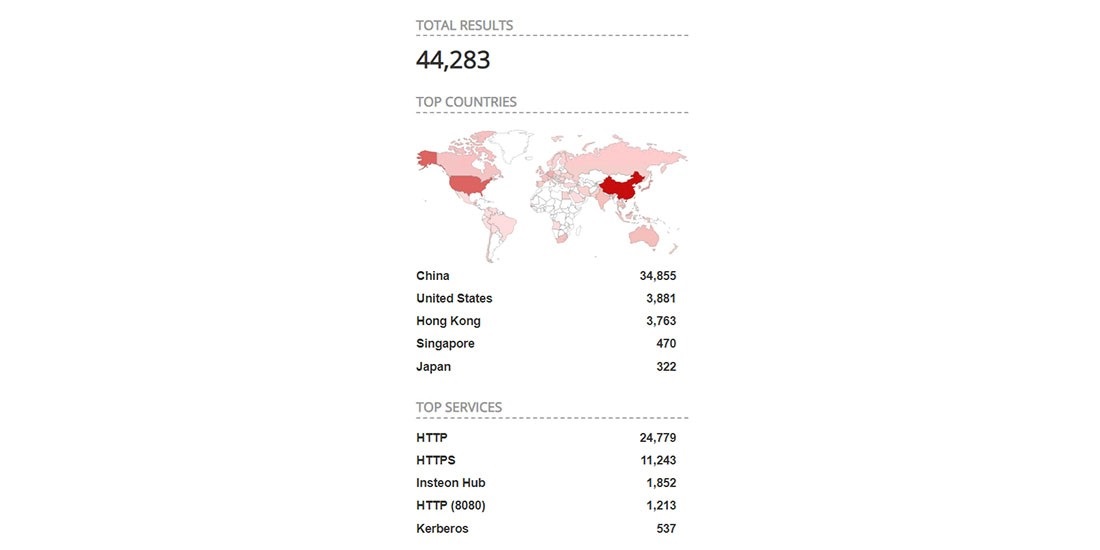
ThinkPHP is widely used in China, according to Shodan, and moderately well used in some of the worst affected countries of South America, such as Brazil.
The technology also widely used in the US, but that country has not been touched by what, for now at least, remains a low impact threat.
The campaign has the potential to evolve into something bigger and potentially more harmful, Check Point warns.
“SpeakUp’s obfuscated payloads and propagation technique is beyond any doubt the work of a bigger threat in the making,” Check Point concludes.
“It is hard to imagine anyone would build such a compound array of payloads just to deploy few miners. The threat actor behind this campaign can at any given time deploy additional payloads, potentially more intrusive and offensive.”






