Top infosec trends in the social media spotlight this week

Corero Network Security this week disclosed the existence of a practical kill switch countermeasure for the Memcached vulnerability to national security agencies.
The company’s announcement came on the heels of this month’s record-breaking DDoS attacks against GitHub and an unspecified US service provider – both of which leveraged flaws in the open-source memory caching system.
The exploit – dubbed ‘Memcrashing’ – works by allowing attackers to generate spoof requests and amplify DDoS attacks by up to 50,000 times, creating an unprecedented flood of attack traffic.
Memcrashing hit the headlines last week after it was revealed that GitHub had been subject to a victim to a DDoS amplification attack, which clocked 1.35Tbps.
However, the record for the biggest-ever DDoS attack was broken just five days later, as Arbor Networks announced that a US service provider had been hit with 1.7Tbps of traffic.
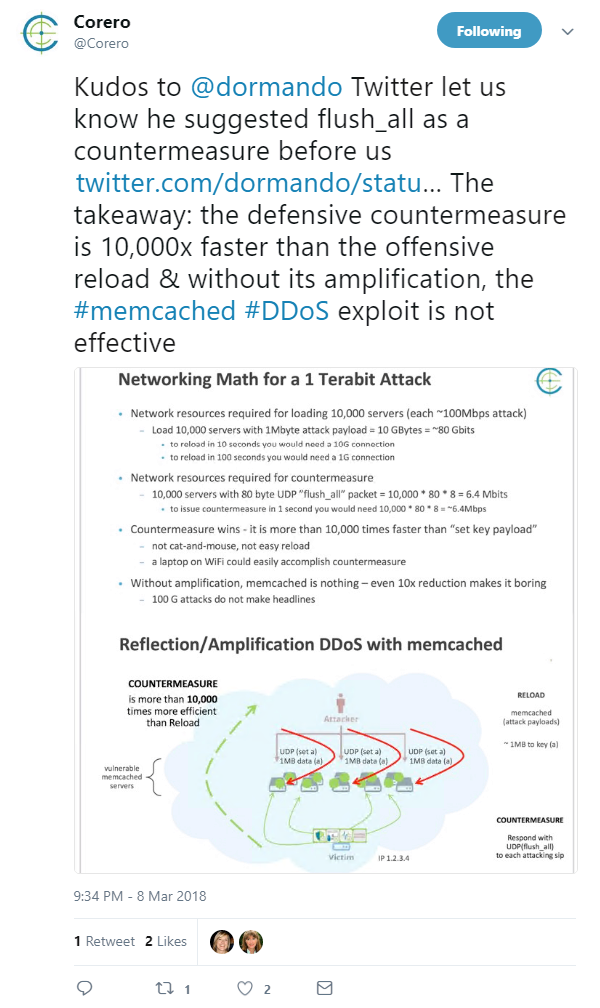
According to Corero, the ‘flush all’ countermeasure invalidates a vulnerable server’s cache by sending a command back to an attacking server to suppress the DDoS exploit.
The discovery of the kill switch could not come at a better time, as the DDoS mitigation firm found that vulnerable Memcached servers could also be coaxed into divulging sensitive information, including confidential database records, website customer information, emails, and API data.
“Memcached represents a new chapter in DDoS attack executions,” said Corero CEO Ashley Stephenson. “Previously, the most recent record-breaking attacks were being orchestrated from relatively low bandwidth IoT devices.
“In contrast, these Memcached servers are typically connected to higher bandwidth networks and, as a result of high amplification factors, are delivering data avalanches to crippling effect. Unless operators of Memcached servers take action, these attacks will continue.”
From attacks designed to cripple web services to a project that aims to improve users’ online experience, Google has just announced plans to pursue a set of future web standards that will support near-instantaneous loading and distribution across multiple platforms:
In a blog post yesterday, Google said it would aim to convince the group in charge of web standards to adopt technology inspired by its open-source Accelerated Mobile Pages (AMP) framework.
“The standardization work motivated by AMP is well under way through various WICG projects,” the company said.
“Google’s goal is to extend support in features like the Top Stories carousel to AMP-like content that meets a set of performance and user experience criteria and implements a set of new web standards.”
On Tuesday, meanwhile, bug bounty hunters welcomed the news that Kaspersky Lab had upped the reward for those who discover severe flaws in its products.
The antivirus company is now offering $100,000 to researchers who can identify remote code execution vulnerabilities through the database update channel.
Kaspersky’s bounty hike follows last week’s announcement that Sony has launched its own bug bounty program, in partnership with HackerOne.
However, as previously reported in The Daily Swig, there is a distinct lack of information with regard to exactly which properties are covered under the Secure@Sony initiative.
Finally, March 8 marked International Women’s Day, with thousands of people taking to social media to help celebrate the social, economic, cultural, and political achievement of women.
Despite the fact that women have been making waves in science and technology for decades, this year’s International Women’s Day took place amid reports that females are still highly unrepresented in the cybersecurity sector.
In a special feature this week, The Daily Swig spoke to some of the most ground-breaking female security experts to find out what needs to be done to redress the gender imbalance: