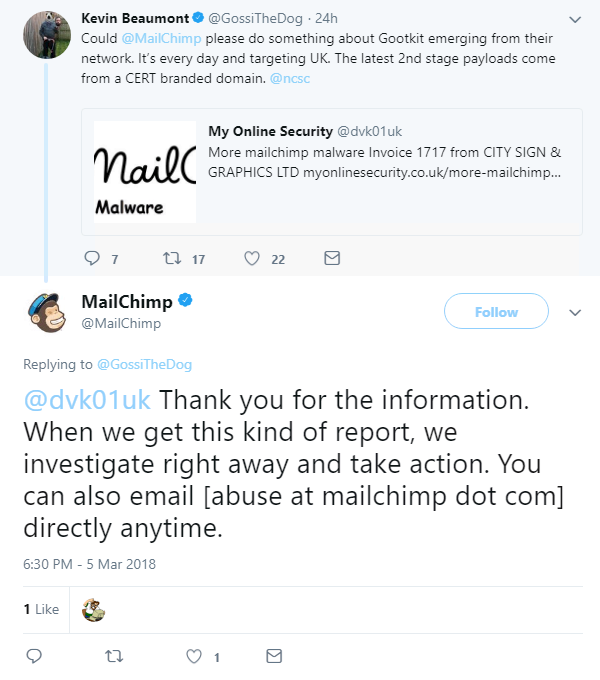
Compromised accounts are spreading malicious software to thousands of subscribers

Inboxes are being hit by a new malware campaign after the login details of some MailChimp account holders were reportedly compromised.
Last month, infosec blog My Online Security reported that MailChimp subscribers were receiving suspicious emails containing links which, when opened, downloaded malware onto their devices.
The emails were from a legitimate company called Oxfordshire Sage Support, and appeared to be an invoice.
But a link in the body of the email contained a malicious JavaScript file, which downloaded the Gootkit banking trojan onto users’ devices.
This malware aims to steal the user’s passwords and financial information, including bank and PayPal details.
The campaign is also understood to be spreading other malware strains designed to take Facebook and social media login details.
Many of the emails also contained ransomware that encrypted the victim’s files and demanded $400 to recover them.
Last night, another fake email surfaced in which attackers used an attachment to entice the victim into downloading the malicious software.
Again, the file appeared to be an invoice.
My Online Security spokesperson Derek Knight told The Daily Swig: “What has happened is that several companies using MailChimp have somehow been compromised, and their login details were used to upload a new massive mailing list that has links to malware, generally a banking trojan, but it can be almost anything.
“Sometimes the initial malware downloader has been delivered via a compromised user’s account on MailChimp.
“In other cases, the actual malware download comes from other compromised servers that are not under the victim’s control on or the MailChimp network.”
It’s a jungle out there
Knight explained that MailChimp users should take the necessary steps to protect themselves by employing two-factor authentication (2FA).
He said: “My advice to any business, charity, company or individual using the MailChimp service is to make sure 2FA is enabled on the account, so that nobody can log in without possession of the 2FA device, which is normally a mobile phone.
“That will stop this sort of campaign dead in its tracks.
“This is unless there is a vulnerability in the actual MailChimp service, in which case the criminals don’t actually need login details.
“Nobody at this time knows whether it was human error and the users have responded to a previous phishing email, unwittingly giving their up details, or whether the fault is at MailChimp’s end.“The gut feeling from most security professionals is that the users have had their log in details stolen somehow.”
Knight also issued advice to would-be victims and urged people not to open any links or attachments without scanning them using Antivirus software.
He said: “My general standard advice applies to all recipients of these or any other emails - be very careful following links.
“Hover over the link and see where it goes. Don’t download or open any files without scanning them with your Antivirus first.”






