Fresh fuzzing technique might outfox censors

Websites and online services can help circumvent state-run internet censors without requiring any efforts on the part of users, security experts at the University of Maryland have discovered.
In a paper (PDF) presented at the SIGCOMM 2020 conference, the researchers introduced multiple server-side packet manipulation techniques that leverage genetic algorithms to evade internet censors in various countries.
Client-side vs. server-side censorship evasion
Most existing censorship evasion techniques require client-side action, such as installing a VPN application, the Tor browser, or network packet obfuscation software on the user’s device.
“Unfortunately, active participation on the part of clients can limit the reach of censorship evasion techniques. In some scenarios, installing anti-censorship software can put users at risk,” the researchers explain.
In some cases, the anti-censorship tools themselves might be blocked. In others, the users might not even be aware that they are being censored.
The idea behind the work of the researchers at the University of Maryland was to find a way for servers to alter their traffic in a way to bypass censorship regimes and provide their content to users without requiring additional software installations.
Censors are usually triggered by a request sent by the client, which makes it very difficult to develop server-side censorship evasion techniques.
Genetic evasion
To discover server-side censorship evasion, the researchers used Geneva, short for “genetic evasion” – a genetic algorithm that combines various techniques to exploit bugs in censorship technology or through use of censorship evasion strategies.

Geneva was jointly developed by researchers at the University of Maryland and the University of California, Berkeley, in 2019, but was primarily used for discovering client-side techniques.
“Geneva is a general tool, and can be seen as a sort of network fuzzer – it has found bugs in Scapy, off-the-shelf firewalls, and most recently we developed a new fitness function that allows us to use Geneva to find new DoS amplification attacks (in a work currently under submission),” Kevin Bock, researcher at the University of Maryland and co-author of the paper, told The Daily Swig.
“Server-side evasion was something we hadn’t considered trying until we had seen the variety of strategies Geneva had found from the client side.”
Read more of the latest data privacy news
The researchers repurposed Geneva to run from servers, and in five months, they were able to develop a total of 11 server-side censorship evasion strategies on five protocols (HTTPS, HTTP, DNS, FTP, SMTP). These techniques were applied against the censorship technologies of four countries: China, India, Iran, and Kazakhstan.
For instance, where a censor would expect a server-side SYN/ACK packet from the server followed by an ACK and a query from the client containing a censored keyword, the server sends a double SYN/ACK, which confuses the censorship technology and allows the connection to go through.
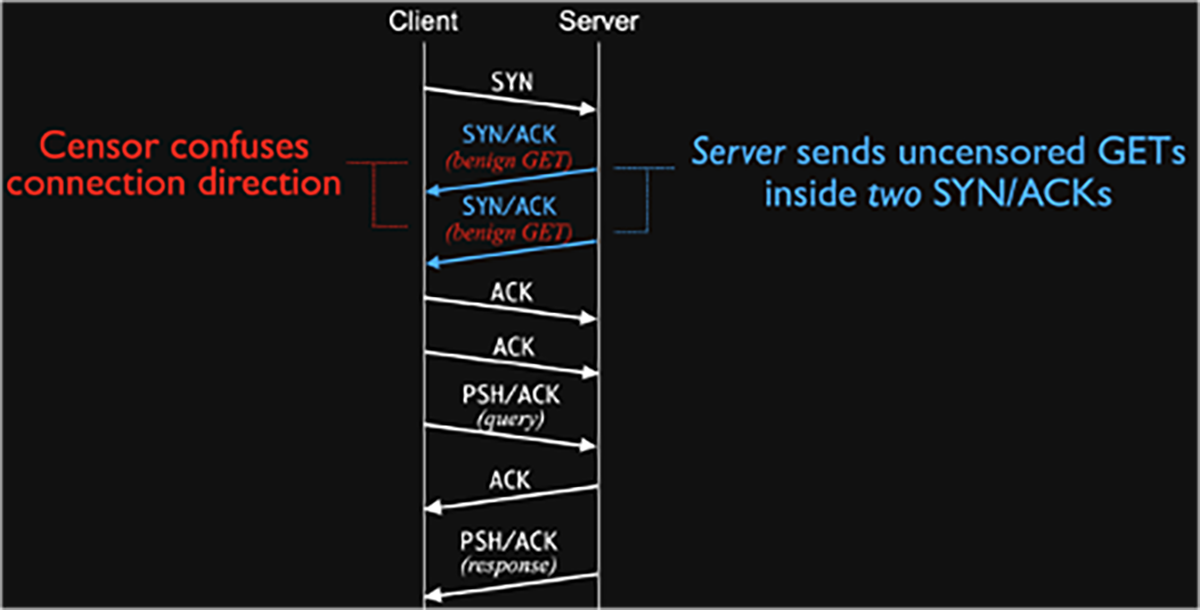 Server side censorship evasion
Server side censorship evasion
The techniques work on deep packet inspection-based censorship, where the client and server can communicate, and the censor will jump in and tear down the connection if it detects forbidden content.
“The alternative form of censoring (outright blocking some IP addresses or simply shutting down the network) are beyond what something like Geneva can do,” Bock says.
A cat-and-mouse game
“I think these tricks are fantastic and very interesting; having a server act to confuse the censor firewalls is certainly a newer approach that will work for a little while,” Adam Kujawa, director of Malwarebytes Labs, told The Daily Swig.
Kujawa added a caveat noting that censorship evasion is, like malware detection, a constant competition. “So, to that end, this initial study is a great find and an interesting concept, but the censors will be updated and will find a way to detect this kind of misdirection.”
The security researcher also pointed out that while the server-side evasion techniques will give users access to individual websites, users will still need tools like Tor and VPN to traverse the internet completely unblocked.
“I guess it comes down to what the user wants to do; if they just want to access this one site unblocked by the censor and that site is utilizing these tricks, it’s a win,” Kujawa explained.
READ MORE SymTCP – a new tool for circumventing deep packet inspections
“However, if the user wants to do more than just visit sites where the servers have deployed this trick, or they want to maintain their own anonymity, they will still need to do things the current way.”
Other experts also praised the work will noting its potential limitations.
"It’s really cool that they have a genetic algorithm that can do what is fuzzing on the censoring middleboxes,” Jon Callas, directory of technology projects at the Electronic Frontier Foundation, told The Daily Swig.
“However, like all exploits found by fuzzing, they can still be fixed. Assuming that the censors have the devotion to find and fix the errors in their censorboxes, they win over time.”
Callas also noted that if different censoring countries cooperate by sharing fixes, they get synergies in improving censorship. “Nonetheless, this is really cool but ends up being a cat-and-mouse game,” he said.
“With a genetic algorithm automating the mice, advantages are to the mice and the cat needs dedication."
Long is the way, and hard...
Bock acknowledged that work on censorship evasion is an ongoing effort.
Geneva is still in the research phase and the researchers are working with a few groups to integrate the methodology and techniques into their products.
“The current focus of our development is extending Geneva to work at the application layer,” he said.
“Currently, it’s been limited to modifications at the TCP/IP layers, so we’re adding new primitives and code so it can modify the application layer as well, starting with HTTP and TLS.”
The team of academics has had some encouraging initial results in Kazakhstan, but the system is still under development.
They’re also using the technology as a tool for rapid response to new censorship events.
“In February, we discovered a new form of censorship in Iran and defeated it in a matter of hours. Similarly, in July, China rolled out a new censorship system to block the use of ESNI [Encrypted Server Name Indication], which we also defeated in hours,” Bock said.
RELATED Cat and mouse: Privacy advocates fight back after China tightens surveillance controls






