Latest findings paint a “bleak picture” for human rights, says Citizen Lab

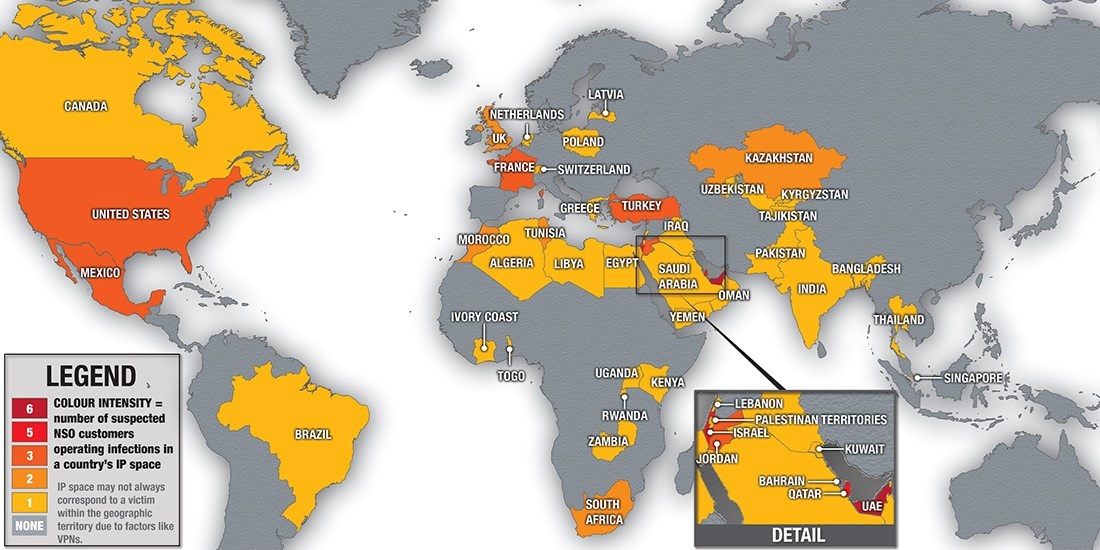
The use of controversial mobile spyware developed by NSO Group appears to be expanding, after researchers developed a new web scanning technique that identified targets in 45 countries.
Citizen Lab researchers, led by Bill Marczak, fingerprinted surveillance infrastructure associated with NSO’s Pegasus spyware before using a combination of TLS and DNS network analysis to profile 36 operators that were utilizing the mobile surveillance suite.
“Between August 2016 and August 2018, we detected 1,091 IP addresses and 1,014 domain names matching our fingerprint,” the researchers said.
“We developed and used ‘Athena’, a novel fingerprinting technique to group most of our results into 36 distinct Pegasus systems, each one perhaps run by a separate operator.
Citizen Lab, an interdisciplinary lab based at the University of Toronto, Canada, identified 45 countries in which Pegasus-related ops were active – although it admitted that the actual locations of surveillance targets is not definitive because factors such as VPNs and satellite internet can muddy the picture.
According to the researchers, at least 10 Pegasus operators were running cross-border surveillance. Six countries with Pegasus operations have previously been accused of abusing the spyware, including Bahrain, Kazakhstan, Mexico, Morocco, Saudi Arabia, and the United Arab Emirates.
Open to abuse
Pegasus is sold to governments and marketed as a lawful surveillance tool for criminal or national security investigations. However, Citizen Lab alleges that the technology is not infrequently abused to spy on members of civil society by various ‘Big Brother’ agencies.
For example, the latest Citizen Lab research has uncovered evidence of three Pegasus operations in Mexico, despite previous abuses two years ago.
The tell-tale signs of Pegasus surveillance also extend into Saudi Arabia despite a recent investigation that showed the technology was used to target an Amnesty International staff member and a Saudi human rights activist.
UAE-based human rights activist Ahmed Mansoor was targeted with NSO Group’s Pegasus spyware after previously being targeted with spyware from FinFisher and Hacking Team.
Citizen Lab exposed an attack against Mansoor using Pegasus that leveraged three zero-day iPhone exploits back in 2016. Security sleuths at the Canadian institution have been actively tracking the technology ever since.
Phishing for targets
Pegasus typically spreads through phishing. Government operators of Pegasus need to trick a target into clicking a specially crafted exploit link. Many of these links have political themes, casting doubt on the official line that Pegasus is restricted to criminal investigations.
Clicking on a link triggers an automated attempt to surreptitiously install Pegasus – sometimes using zero-day exploits.
The spyware is designed to record calls, text messages, or recordings made after covertly enabling a compromised phone’s microphone or camera. It establishes a covert channel to a command and control server, established by operators.
Infected devices contact this system to receive and execute operators’ commands as well as in order to upload compromised data.
Israel-based NSO’s competitors include Gamma International (a German/UK company that markets FinFisher/FinSpy) and Hacking Team (Italy), which itself fell victim to a high-profile breach in 2015.
Martijn Grooten, a sometime security researcher and editor of industry journal Virus Bulletin, told The Daily Swig: “I don’t know whether these are the best known because they’re one of the few ones, because their marketing is good, or because their opsec is bad.”
Sanction the criminals, not the software
Katie Moussouris, a bug bounty pioneer and founder of Luta Security, said that regimes known for human rights abuse using Pegasus is “definitely a problem”, but she argued against developing further regulations to target NSO Group and similar firms.
Instead, efforts should focus on using existing rules to punish or sanction criminals or repressive regimes that are using software to enable human rights abuse, she told The Daily Swig.
“This type of software is already export controlled (aka regulated) in 42 Wassenaar states,” she added. “Even in Israel (not part of Wassenaar), NSO was granted export licenses for this software.”
Following the publication of the Citizen Lab report, NSO Group issued a statement claiming that the list of countries in which the organization has been alleged to sell its products is inaccurate.
“NSO does not sell its products in many of the countries listed,” the company said. “The product is only licensed to operate in countries approved under our Business Ethics Framework and the product will not operate outside of approved countries.”






