Security agency lays Easter egg at RSA
The US National Security Agency (NSA) stole the show at the RSA Conference on Tuesday by making good on its promise to release a suite of reverse engineering tools, Ghidra.
Ghidra is a disassembler that presents the contents of executable files as instructions in assembly code, allowing the analysis of suspicious code samples by security researchers and reverse engineering enthusiasts, among other features.
Senior NSA adviser Robert Joyce offered a presentation on Ghidra prior to the release of the utility.
The toolkit comes with supporting documentation, slides, and exercises. A placeholder repo has been set up on GitHub, in preparation for a full open source release.
The Java-based Ghidra platform runs on a variety of platforms, including Windows, macOS and Linux, and supports a variety of processor instruction sets. A GUI-based front end supports multiple views, while the platform incorporates features geared towards collaboration.
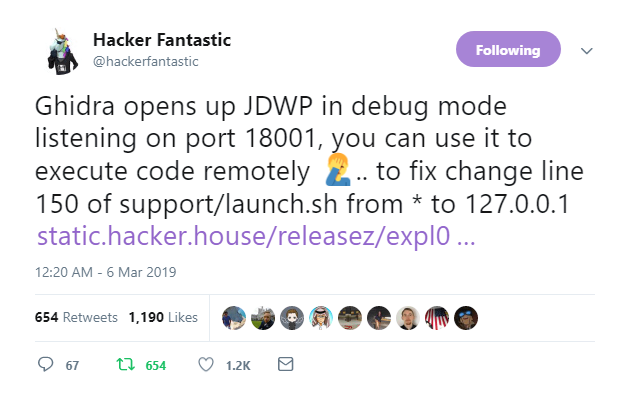
Independent security experts examining the tool for the first time managed to find an insecure configuration option within hours.
Oops.
The insecure config only arises if Ghidra is run in debug mode, and even in that case it's only exploitable in the absence of a firewall.
The researcher who uncovered the flaw, Hacker Fantastic, was quick to state that the presence of the bug isn’t reason in itself to avoid experimenting with the utility.
“Ghidra is a really nice tool addition for reverse engineering, don’t let my observation of an insecure configuration option dissuade you from trying it out,” he said.
Reception from the infosec community has generally been positive with an undercurrent of wariness – evidenced through jokes that the software might have some kind of backdoor.
“My favorite part of Ghidra is the side-by-side disassembler/decompiler,” said Marcus Hutchins, the researcher who discovered the WannaCry kill switch. “It’s a total game changer for those looking to break into the industry.”
Martijn Grooten, editor of industry journal Virus Bulletin and occasional security researcher, joked: “Plot twist: in 2021 someone discovers advanced nation state malware that thanks to an undocumented future in Ghidra shows up as benign when reverse-engineered.”
Ghidra was initially developed more than a decade ago by the NSA before, more recently, it began sharing the tool with other US government agencies. The existence of the tool was publicly exposed in March 2017 after WikiLeaks released Vault7, a collection of internal CIA files.
Commercial reverse engineering tools already exist in the shape of IDA-Pro and r2, among others.
Rob Graham of Errata Security provides a run-down of Ghidra and an explanation of what reverse engineering tools more generally in a Twitter thread.
For those interested in seeing the tool in action, Hutchins has recorded a live stream recording of his explorations of Ghidra and uploaded it to YouTube.