Platform aims to shore up lax wireless security and eradicate WiFi spoofing attacks

A new platform designed to detect WiFi hijacking devices has been released to the open source community.
The system, dubbed ‘Nzyme’, has been published under the v1.0 moniker ‘Kyle Canyon’ on GitHub.
Nzyme is the result of three years’ worth of “weekend hacking” by developer Lennart Koopmann and is described as a “free and open WiFi defense system that detects and physically locates threats using an easy to build and deploy sensor system”.
WiFi attacks
There are a variety of ways to defend today’s wireless networks, including enabling WPA2 encryption, changing default password setups, and enabling firewalls. Wireless intrusion detection systems (IDS) can also be used to monitor external entry attempts.
However, the developer says that current IDS solutions “fall short and are easily spoofed”, and could be broken by out-of-the-box, commercially available hacking tools.
“Existing tools are focusing a lot on signature-based detection,” Koopmann told The Daily Swig. “They look for anomalies and outliers, but I found that WiFi communication is almost effortless to spoof, and anomaly detection has very high false-positive rates, especially in wireless environments.”
To combat these devices, including but not limited to offerings such as the WiFi Pineapple and Pwnagotchi, Nzyme – which can be used as a portable tracker device – has built-in definitions for “out-of-the-box bandit” devices that will detect them the moment they are “powered on and in range”, the developer says.
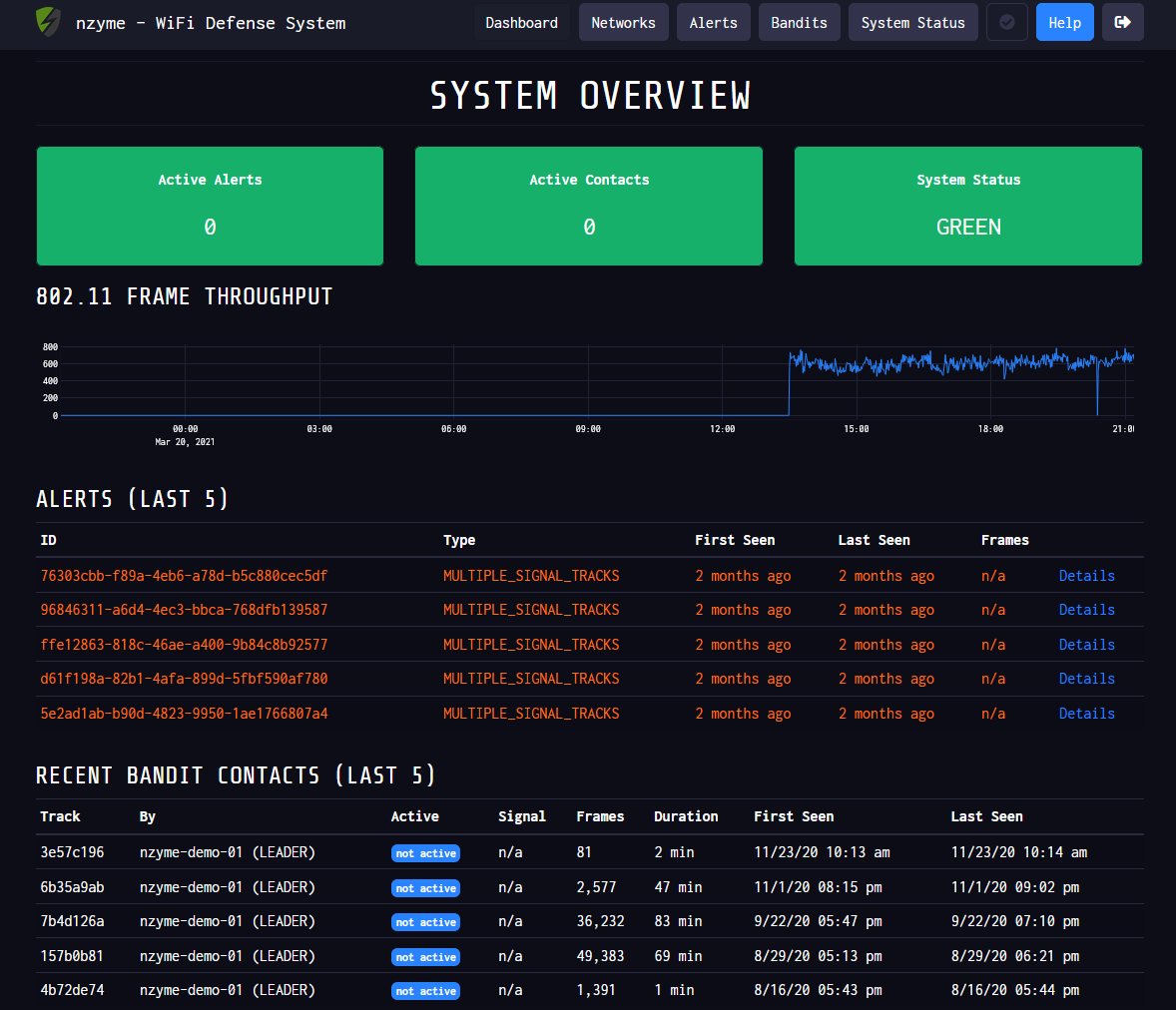 Nzyme monitors the entire WiFi spectrum in the hunt for so-called ‘bandit’ devices
Nzyme monitors the entire WiFi spectrum in the hunt for so-called ‘bandit’ devices
Under the HUD
The platform’s overview screen includes system status, active alerts, timestamps for intrusion or anomalies detected, probe logs, channel traffic monitoring, and fingerprint records.
“Nzyme and its ‘bandits’ concept can detect many of these platforms the moment they power on, often even before an attack is executed, and then even track specific devices,” Koopmann explained.
“This ability massively increases your security posture in a notoriously under-secured and easy-to-attack environment like WiFi.”
RECOMMENDED Centris helps prevent supply chain attacks by flagging modified open source components
Nzyme can be tailored to use built-in definitions or custom alerts, although bandit definitions considered to be too wide-ranging may result in false positives.
“A Nzyme tracker device can be used to physically locate the source of specific WiFi frames and play a big role in actively defending your perimeter,” the developer added, noting this concept is currently being explored through both LoRa and 802.11 WiFi standards.
Active development
When queried over the potential use of clone SSID denial-of-service (DoS) techniques in the future – or keep the software’s capabilities to alert-only – Koopmann said there are no plans, at present, to introduce “fire back” options, but the callback system for alerts will soon be upgraded to trigger local scripts which will extend Nzyme further.
As a new project now in active development, naturally there are bugs and hurdles to overcome.
A future improvement on the Nzyme roadmap is multi-node support and potentially the introduction of a node type that could allow sensors to be deployed to extend coverage, or perhaps go so far as to triangulate bandits.
“Currently, I am looking for community feedback after this initial release,” Koopmann commented. “Nzyme is my weekend project, and all feedback and contributions are always welcome.”
YOU MIGHT ALSO LIKE Isn’t it ironic: Exploiting GDPR laws to gain access to personal data






