Top infosec trends in the social media spotlight this week

It’s been a week of interesting security developments from Google, as the tech firm launches its own hardware keys for two-factor authentication (2FA) and continues in its quest for an HTTP-free internet.
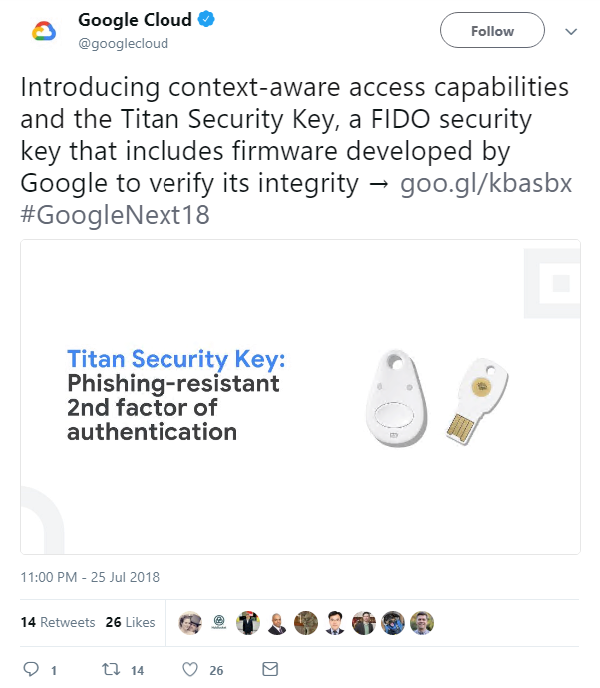
On Wednesday the company unveiled the Titan Security Key, a FIDO-made USB device that includes firmware developed by Google to “verify its integrity”.
“We’ve long advocated the use of security keys as the strongest, most phishing-resistant authentication factor for high-value users, especially cloud admins, to protect against the potentially damaging consequences of credential theft,” Google Cloud product manager Jennifer Lin said in a blog post.
The launch of Titan, which sees Google square up against incumbent hardware key giant Yubico, among others, comes as the company told Brian Krebs that not a single one of its 85,000+ employees had been successfully phished on their work-related accounts since early 2017.
Elsewhere, Chrome 68 was pushed out to Android, Linux, macOS, and Windows this week – complete with a new interface designed to steer users away from insecure sites.
As reported in The Daily Swig, the latest iteration of Google’s freeware browser sees the company follow through with its promise of marking all HTTP sites as “not secure”.
This might seem like one small step for Chrome, but the move is being hailed as a giant leap for web security, as it now effectively forces site owners who have previously failed to embrace the encrypted HTTPS protocol to do so – or else risk a sharp dip in traffic.
“Chrome’s new interface will help users understand that all HTTP sites are not secure, and continue to move the web towards a secure HTTPS web by default,” said Chrome security product manager, Emily Schechter.
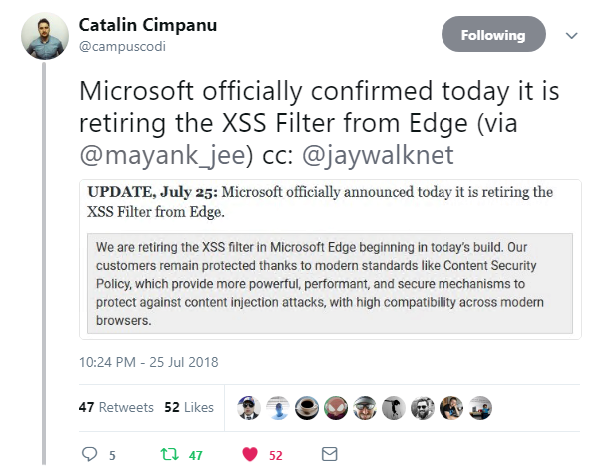
From Mountain View to Redmond, following our exclusive report last week that the XSS Filter had disappeared from Microsoft Edge, the company has confirmed the cross-site scripting defense mechanism has indeed been dropped for good.
“We are retiring the XSS Filter in Microsoft Edge beginning in today’s [Windows 10 Insider Preview] build,” the company said.
“Our customers remain protected thanks to modern standards like Content Security Policy, which provide more powerful, performant, and secure mechanisms to protect against content injection attacks, with high compatibility across modern browsers.”
Click here for the full story.
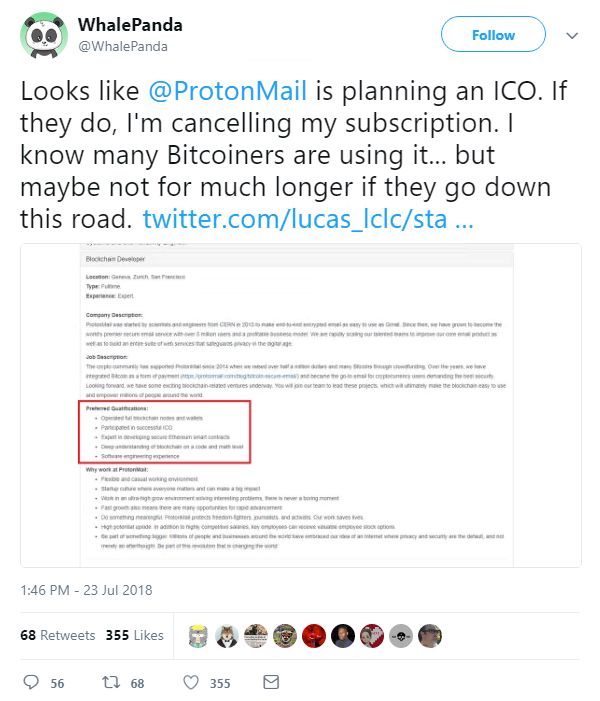
In other news, ProtonMail was this week revealed to be exploring new security technologies, as it emerged the encrypted email provider is currently looking for a ‘Blockchain Developer’ to join its team in Geneva.
The job listing – coupled with the recent launch of the ProtonCoin website – was enough for some to conclude that the company was planning to raise new funding through a controversial initial coin offering (ICO).
Given ProtonMail’s popularity in the cryptocurrency community (and no doubt to quell fears that the privacy-focused email provider may soon shift focus by jumping on the bitcoin bandwagon), the company was quick to respond to the allegations.
“These are unsubstantiated rumors at this time, and we have made no announcements on this topic,” ProtonMail said in a Reddit post.
“Protoncoin.com is indeed owned by ProtonMail, but the site contains no details, as you might have noticed. We actually own hundreds of Proton domain names, many of which are parked in this fashion, to prevent trademark infringement by others. Many of these sites are also used to reduce the risk of phishing against Proton users.”
While the email provider said the existence of a site should not be taken to signify its immediate intention to launch a product, it said it was “actively engaged” in exploring the ways in which the blockchain can be leveraged to improve email security.
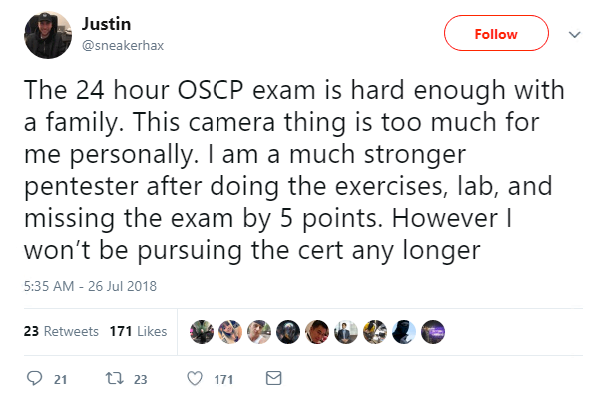
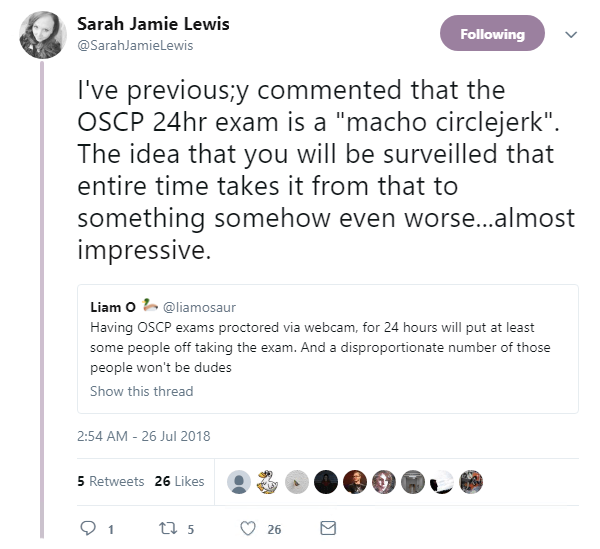
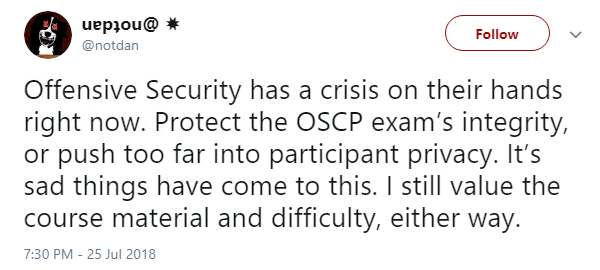
And finally, the infosec community took to Twitter in their droves this week to weigh in on a popular certification body’s recent decision to monitor examinees via their webcam.
Offensive Security is an information security training organization renowned for its grueling 24-hour OSCP examination aimed at testing candidates’ stamina, persistence, and determination.
While prospective pen testers are able to complete the test from the comfort of their own home, they will no longer be completely alone, thanks to a new “proctoring process” that requires them to use screen sharing software and their webcam.
Outlining the changes on its website earlier this week, Offensive Security said it had noted an “ever-increasing number of attempts to subvert or otherwise cheat the exam process”.
“The goal is to be able to be a silent observer during your exam to assist our exam graders with any anomalies they may see in your report,” the organization said.
Many did not take kindly to the news:
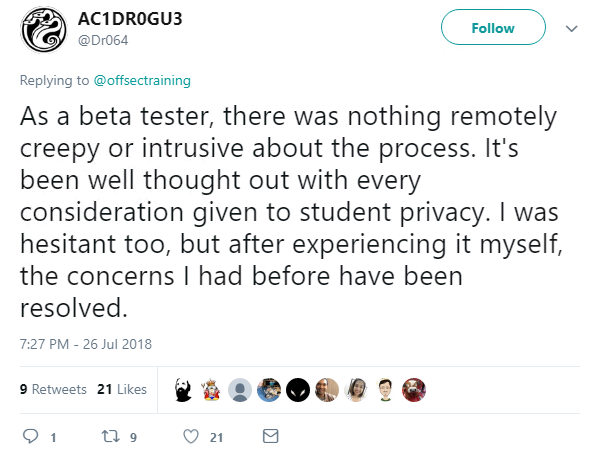
For others, the anti-monitoring advocates are kicking up are a fuss over nothing:
“We didn’t make the decision to move to proctored exams lightly,” Offensive Security said. “We fully understand that not everyone will agree with our decision and some may feel the addition of proctoring is personally not viable for them.”
We will be monitoring this story closely for developments.